Search Results for "How to detect malware"
Find videos related to your search query. Browse through our collection of videos matching "How to detect malware". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "How to detect malware"
50 results found

0:40
What Is Malware? | Malware Explained | Malware Attack | Definition of Malware
LOGIK EYE FORENSIC
85 views

0:20
Build a Python Malware Scanner 🔥 Detect Ransomware, Spyware & More! | Cybersecurity Project
Esraa Codes
1.8K views

0:20
Monoxide.exe virus #malware #wallpaperchange #testing #malware
Puteri sofea Ariana
138.8K views

0:14
Testing malware PT 1 today opium location re-upload from tiktok #virus #malware #test
Gray malware tester
603.3K views

4:49
What is Malware? | Malware Analysis for Beginners | Cyber Security Tutorial 2025
Cyber Gita
34 views

21:35
Hack.lu 2023: Malware AV Evasion Tricks: Cryptography In Malware by Cocomelonc
Cooper
872 views

0:17
Windows has a hidden malware removal tool | #shorts #trending #mrt #malware
Pre-view Tech
819.9K views

0:31
El adware es un tipo de malware que se instala en tu móvil y te asalta con anuncios #adware #malware
astrocell
6.2K views

0:11
Adware slows down your device and opens the door for more severe malware. #memes #funny #malware
IDSTRONG
1.2K views
![Detect Your Friend's Devices with a NodeMCU MAC Address Sniffer [Tutorial]](/image/i.ytimg.com/vi/30Eww40s9D0/hqdefault.jpg)
13:57
Detect Your Friend's Devices with a NodeMCU MAC Address Sniffer [Tutorial]
Null Byte
65.3K views

1:08
STEGANOGRAPHY - How to Detect Steganography Files in Windows
Aravind Ch
823 views

16:19
Use of steganographic tools like OpenStego, to detect data hiding or unauthorized file copying
VIVA Institute of Technology Computer Engg Dept
2.9K views

9:10
How to Detect Deepfakes: The Science of Recognizing AI Generated Content
NOVA PBS Official
97.5K views
0:55
Detect Squares - Leetcode 2013 - Python #shorts
NeetCode
501.4K views

0:48
PM Modi Please watch (how to detect deep fake)
AI a step towards Metaverse Concept
28 views

39:29
DEF CON 33 - Post Quantum Panic: When Will the Cracking Begin, & Can We Detect it? - K Karagiannis
DEFCONConference
74.3K views
![[RSAS] How to detect uninstalled Steganography tools](/image/i.ytimg.com/vi/PJQbkJrY35Y/hqdefault.jpg)
3:38
[RSAS] How to detect uninstalled Steganography tools
Nicola Talin
86 views

1:08
how to detect steganography files in windows stegdetect computer forensics
Aravind Ch
4.2K views

2:18
Detect Cloud Apps, Shadow IT, Threats, and Policy Violations with IBM Cloud Security Enforcer
Tiffanienc
2 views

1:58
Police detect IED in Baramulla, North Kashmir
NewsX
0 views

1:21
Twitch launches tool to detect banned users
Bang Gaming News
49 views

1:53
How Does Quantum Cryptography Detect Eavesdropping? - Quantum Tech Explained
Quantum Tech Explained
3 views

24:17
Visual Analytics - Detect the Expected and Discover the Unexpected
Tech
1 views

20:58
Cybersecurity Trends for 2022 – Strategies to Prevent, Detect and Respond to Threats
Eide Bailly
49 views

2:07
How To Detect Unauthorized Access? - SecurityFirstCorp.com
SecurityFirstCorp
97 views

5:44
How to detect baloney the Carl Sagan way | Michael Shermer
Big Think
1 views

1:05
AI trained to detect asian hornets in hope for bee populations
Stars Of Hollywood
20 views

1:02
How does France detect Covid-19 Brazilian, S. African and British variants?
FRANCE 24 English
17 views

22:52
How Web3 and cryptography can be used to detect authenticity of content (Amy and Devon James)
DarkHorse Podcast Clips
3.8K views
0:15
How to detect if your PC has been hacked
Scrandalftech
483.4K views

41:47
How Can We Detect Consciousness in Infants?
Simons Institute for the Theory of Computing
198 views

29:17
Data Exfiltration Explained: How to Use Splunk and Wireshark to Detect Data Exfiltration
Motasem Hamdan
366 views

1:01
How to prevent and detect insider data exfiltration.
Shield Identity
78 views

2:11
How To Detect Data Exfiltration? - SecurityFirstCorp.com
SecurityFirstCorp
184 views

3:54
Data Loss Prevention: How To Detect Data Exfiltration? - Virtual Communication Hub
Virtual Communication Hub
3 views

1:06
EU launches drone wall to 'detect and destroy'
euronews (in English)
4.7K views

1:10
Trained sniffer dog trained can detect power faults deep underground
The Independent
319 views

0:58
YouTube creates tools to detect AI-created videos
Bang Tech News
587 views
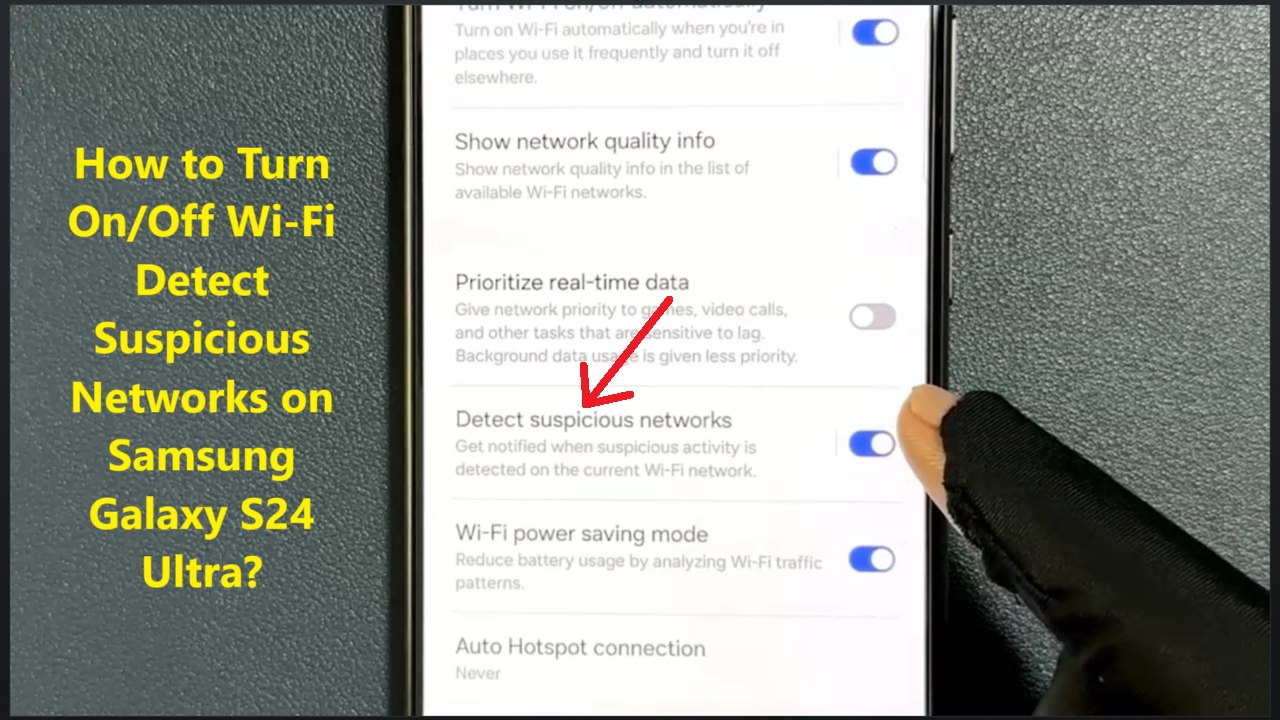
1:08
How to Turn On/Off Wi-Fi Detect Suspicious Networks on Samsung Galaxy S24 Ultra?
TechTips
230 views

0:35
🚨How Hidden Malware Sneaks into Your Files! #shortvideo #shorts #new #hacker
Beyond The Firewall
97 views

0:30
New Malware 'Koske' Uses Steganography to Hide in Images: Protect Your Linux System
Hacked dAily
850 views

1:00
Creating malicious software in Python. Pt:1 #Python #malware #linode #IT #tech #code #coding
NetworkChuck Academy
119.1K views

0:48
The Hidden Dangers of Steganography in #Cybersecurity #Steganography #Malware
Cyber Bharat
158 views

57:16
Hiding In Plain Sight - Advances In Malware Covert Communication Channels
Black Hat
5.4K views

9:45
Ethical Hacking Course Series 3: Steganography, Cryptography, Android Hacking, Kali Linux, Malware
KJR CYBER TECH
26 views

8:11
What is Ransomware | Types of Ransomware | Cryptovirology and Cryptography | Malware and its Types
World Walk
264 views

0:41
Hackers Can Hide Malware in Images! (Steganography Explained)
Byte Secure
1.8K views

17:02
Cyber Crime & Security Explained || Virus Malware Firewall Digital Certificate!!
Great Adib
169 views

3:29
How Is Steganography Used In Malware? - SecurityFirstCorp.com
SecurityFirstCorp
56 views

2:02
Hidden Malware in Images: Steganography Warning
How
79 views
Page 1