Search Results for "Fujitsu Security Operations Center"
Find videos related to your search query. Browse through our collection of videos matching "Fujitsu Security Operations Center". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Fujitsu Security Operations Center"
50 results found
1:44
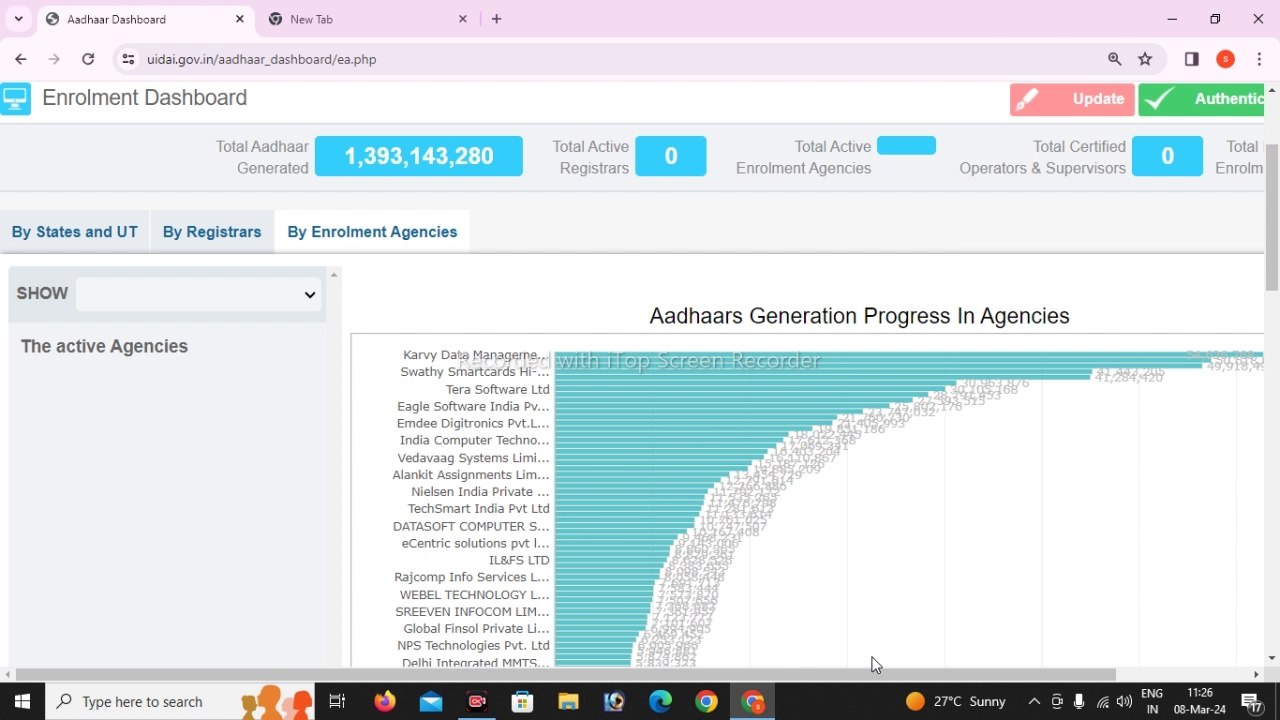
aadhar center kaise open kare || aadhar center new update 2024 || how to open aadhar center 2024
New york city
38 views

4:10
Entrevista Takihiro Matsumura Fujitsu MWC15
ComputerHoy
3 views
1:16
Demystifying 5G with Fujitsu: An Animated Infographics Explainer Video
Broadcast2 World
4 views

7:11
What is BODMAS Rule | PEMDAS | Easy Way | Order of Mathematical Operations | Order of Operations
Epic Learning
35.5K views

1:51
Así monitoreamos el estado de tus activos desde nuestro NOC (Network Operations Center): NSIT
NSIT
4.8K views

3:43
Call Center Games for Call Center Leaders
marjsheppard
186 views

1:07
Training Center Online Computer Training Courses Download - computer training center online training course 2014
Josiah Nonya
22 views
3:54
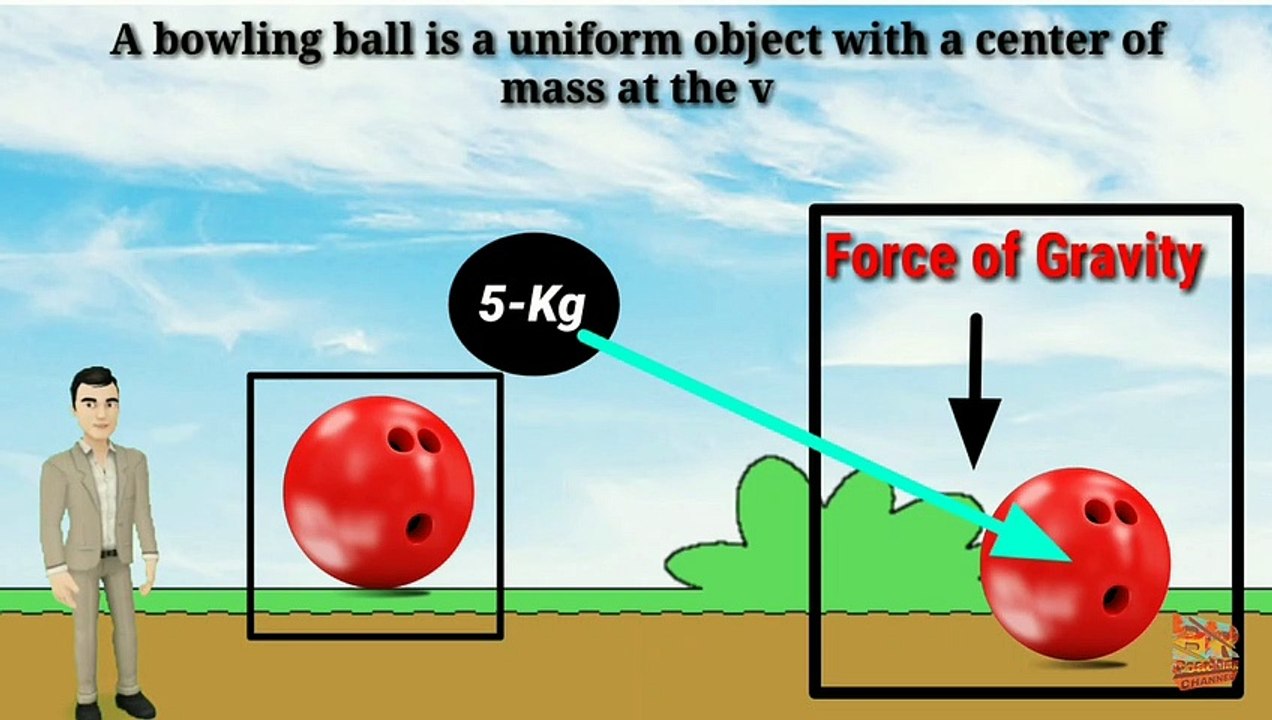
Difference between Center of mass and center of gravity--Physics--In English.
ฟิสิกส์ ราชมงคล
24 views

35:00
Informatica Power Center Training|Informatica Power Center Training|informatica online course|informatica training video
TEKCLASSES
1 views

1:08
Awards Center, Star Awards, Louisville, KY, awards center.net, trophy shop, custom awards
Awards Center
12 views

5:59
GITEX Global 2022: Cryptography Research Center & Autonomous Robotics Research Center
Forbes Middle East
97 views

25:59
AI-driven security operations reduce security analyst burnout
AWANI
111 views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

8:01
Web Security-Security Threats and their solution in hindi-Security Policy-computer network security
Unbeaten Learning
77.8K views
7:53
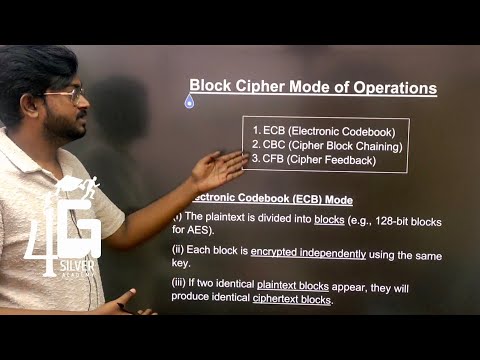
Block Cipher Mode of Operations in Tamil | Cryptography and Cyber Security in Tamil Unit 2 | CB3491
4G Silver Academy தமிழ்
23.1K views

9:37
Cryptography and Network Security: #3 Operations in Zn and Properties
Shreya's E-Learning
2.6K views
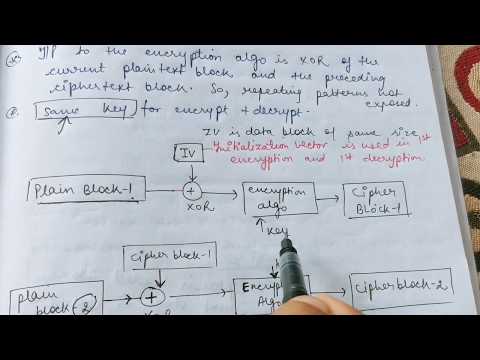
9:40
Block cipher modes of operations (part-1) in Cryptography and Network Security | Abhishek Sharma
Abhishek Sharma
266.5K views
0:30
Major security Forces operations in Bajaur and Mohmand Agency
Newsone Pk
38 views

0:58
Two major security operations in North Waziristan, 11 Terrorist killed
ARY NEWS
31 views

0:18
Cyber Security operations dashboard at Dubai Export city COP28 #Dubai #cybersecurity #technology
ANDYJune Travel Vlogs
43.4K views

4:27
Block Cipher Mode of Operations | Mode of Opreations in Block Cipher | Network security..
DK Technical Point 2.0
187 views

18:31
CISSP Lecture 41 CISSP Security Operations
URDUIT Academy
2.4K views

19:52
Blcok cipher modes of Operations | Cryptography and Network Security
Ekeeda
46 views
7:45
CRYPTOGRAPHY & NETWORK SECURITY Unit-2 Block Cipher & Operations
Algorithm Pod
87 views

11:51:18
Security Operations (SOC) 101 Course - 10+ Hours of Content!
The Cyber Mentor
195.1K views

36:54
CCSP DOMAIN 5 Cloud Security Operations Exam Prep
Prabh Nair
10.8K views

0:36
Rescue operations in Ardèche: French Civil Security helicopters in action
CGTN Europe
1.5K views

4:39
Key Distribution Center (KDC) explained in Hindi || Network security || Kerberos || Akant 360
Unbeaten Learning
26.8K views

3:21
KDC (Key Distribution Center): KDC in information security |KDC in cryptography in hindi | Hindi
Zixplain
9.1K views

5:22
Intro to IBM Cloud Security and Compliance Center
IBM Technology
5.8K views

0:18
Types of Cipher || Cyber Security || Networking training || ProSeek Training Center
ProSeek Training Center
270 views
5:54:54
The BIU Research Center on Applied Cryptography and Cyber Security Live Stream
The BIU Research Center on Applied Cryptography and Cyber Security
922 views

3:00
BTQ Technologies Mystery|Who Is Pushing This Company to the Center of Quantum Security? #BTQ
VALUETER: THE STOCK DETECTIVE
97 views

0:19
iPhone security tips | Disable control center on a locked iPhone
Apple info
161.1K views

2:47
IP Security overview, IP Security architecture, Cryptography and Network Security.
Algorithm Pod
488 views

44:53
Networks Security | Security Services | Security Goals | Cryptography | Steganography | Attacks | IA
Bhavishya Coaching SGNR
929 views

1:01:28
Cryptography & Network Security | CH1.2 The OSI Security Architecture & 1.3 Security Attacks
Computer & IT lectures
67 views

7:32
CRYPTOGRAPHY AND NETWORK SECURITY(2) Principles of security, Security Services
Algorithm Pod
143 views

7:07
What Is Cyber Security | How It Works? | Cyber Security In 7 Minutes | Cyber Security | Simplilearn
Simplilearn
4.8M views

18:38
Information Security- Part 3 - Wireless Security, Cryptography, Application/Host Security, and Logs
Russ Esposito
85 views

6:02
Introduction to cryptography and network security|network security|computers security
SCS VAJRA TUTORIALS
35 views

23:56
What Is Network Security? | Introduction To Network Security | Network Security Tutorial|Simplilearn
Simplilearn
124.2K views

12:12
#5 Security Mechanisms In Network Security | Information Security |
Trouble- Free
71.0K views

9:23
MIME protocol in Cryptography and Network Security | Email security in Network Security
Abhishek Sharma
119.7K views

3:42
GuardMe Security - Home Security Systems & Commercial Security Systems
Craig Metzger
5 views

1:55
Retina Network Security Scanner - Conficker Worm Serial - Retina Network Security Scanner - Conficker Wormretina network security scanner conficker worm (2015)
Jose Sanchez
2 views

4:53
Cyber Security in hindi | Cyber security | What is cyber security
hackploit
18 views

5:30
What is security , information security and cyber security
Noor_khan official
3 views

1:00
security system (security system) "security system"
localvideotv
5 views

10:19
#2 Security Approaches and Principles or Goals of Security- Cryptography |Information Security|
Trouble- Free
99.1K views