Search Results for "Extended Euclidean algorithm in cryptography and Network Security"
Find videos related to your search query. Browse through our collection of videos matching "Extended Euclidean algorithm in cryptography and Network Security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Extended Euclidean algorithm in cryptography and Network Security"
50 results found

44:45
EXTENDED EUCLIDEAN ALGORITHM (CRYPTOGRAPHY AND NETWORK SECURITY)
Samson Chukka
334 views

9:43
Extended Euclidean Algorithm in Cryptography and network security to Find GCD of 2 numbers examples
CSE concepts with Parinita
24.2K views

13:42
Euclidean and Extended Euclidean Algorithm. | CSS
AJS Tutorial
251 views

10:59
Multiplicative Inverse by Extended Euclidean Algorithm || Cryptography || Network Security
Prabhat Educator
352 views

20:51
Extended Euclidean Algorithm || gcd(a,b) || Cryptography || Network Security || with Example
Prabhat Educator
156 views

0:50
Euclidean Algorithm Way to Find the Greatest Common Divisor Euclidean algorithm to find gcd #shorts
Sarvajeet Vishwakarma
208 views

42:46
RSA Algorithm in Cryptography and Network Security - UGC NET PYQs | NETWORK SECURITY - RSA ALGORITHM
Unify Study
4.6K views

1:49:00
Public Cryptography, RSA Algorithm, Extended Euclidean Algorithm شرح
Mahmoud Essam
862 views
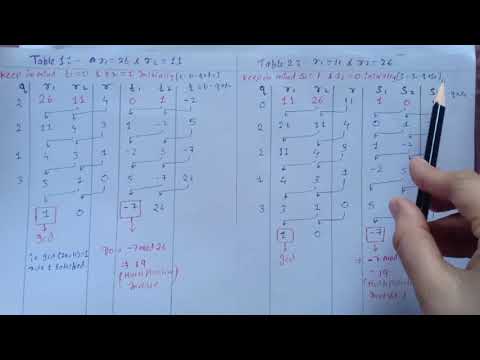
9:02
Cryptography and Network Security: #5 Multiplicative Inverse using Extended Euclidean Algo Part 2
Shreya's E-Learning
1.4K views

14:06
CRYPTOGRAPHY AND NETWORK SECURITY NOTES | NETWORK SECURITY NOTES | NETWORK SECURITY
DIVVELA SRINIVASA RAO
382 views

8:25
Cryptography and Network Security Unit 1- Part 5 | Network Security & Network Access Security Models
TN55 RLE
442 views
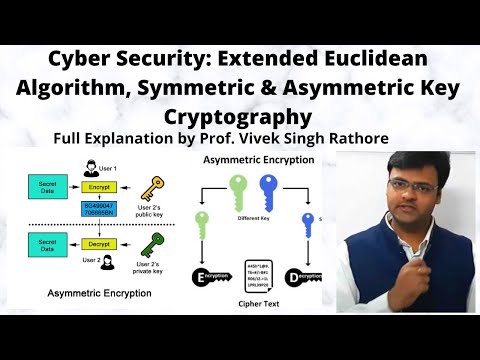
42:26
What is Extended Euclidean Algorithm ? || Symmetric & Asymmetric Key Cryptography || Cyber Security
Vivek Singh Rathore
92 views
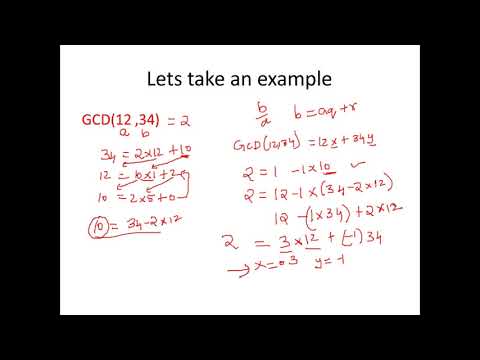
14:34
Extended Euclidean Algorithm - Cryptography - Cyber Security - CSE4003
Satish C J
10.1K views

7:28
Euclidean/ Euclid's algorithm in Cryptography and network security
Abhishek Sharma
232.3K views

5:54
EUCLIDEAN ALGORITHM| CRYPTOGRAPHY AND NETWORK SECURITY| SNS INSTITUTIONS
Suguna Suhashini
8 views
6:38
Euclidean Algorithm Problems (KTU CSE 409 - Cryptography And Network Security - Module 3)
KTU Computer Science Tutorials
3.1K views
6:30
Euclidean Algorithm | Cryptography and Network Security
Narayana Rao K
43 views

12:08
RSA algorithm|RSA algorithm example|rsa algorithm in cryptography and network security|RSA example
Last Night Study
3.3K views

9:00
(Hindi)RSA algorithm|What is rsa algorithm|RSA algorithm in cryptography and network security
Last Night Study
280 views
11:31
2.2 Extended Euclidean Algorithm | CP Algorithm | Codenzyme
Codenzyme
336 views

6:02
Network Security Model | Network security model in cryptography | Network Security
Chirag Bhalodia
22.5K views

10:09
Cryptography and Network Security Course | Cryptography and Network Security Playlist | Cryptography
Abhishek Sharma
397 views

17:45
Euclidean Algorithm || gcd(a,b) || Cryptography || Network Security || with Example
Prabhat Educator
208 views
8:12
Extended Euclidean algorithm(Information Security)
MADE_EASY_FOR_YOU
201 views
8:52
Extended Euclidean Algorithm to find Multiplicative Inverse explained with examples in Cryptography
CSE concepts with Parinita
29.2K views

15:43
Extended Euclidean Algorithm Problem- Number theory - Cryptography
Dr. Arul Selvan Gurumoorthy
388 views

11:19
Extended Euclidean Algorithm in Cryptography | Abhishek Sharma
Abhishek Sharma
193.8K views

4:24
Extended Euclidean Algorithm using Example Multiplicative inverse of a number | Cryptography
Learn MOD
17.3K views

10:00
Finding inverses by Extended Euclidean Algorithm .Cryptography . Easiest explanation ever
Infinite Maths
287 views
![MULTIPLICATIVE INVERSE IN CRYPTOGRAPHY: EXTENDED EUCLIDEAN ALGORITHM [EEA] EXAMPLE 1- (PART 3)](/image/i.ytimg.com/vi/H4EtYZo9V2Y/hqdefault.jpg)
13:10
MULTIPLICATIVE INVERSE IN CRYPTOGRAPHY: EXTENDED EUCLIDEAN ALGORITHM [EEA] EXAMPLE 1- (PART 3)
Lost Bong Coder
34 views
![MULTIPLICATIVE INVERSE IN CRYPTOGRAPHY: EXTENDED EUCLIDEAN ALGORITHM [EEA] - (PART 2)](/image/i.ytimg.com/vi/Ppp2rJq0RAg/hqdefault.jpg)
5:12
MULTIPLICATIVE INVERSE IN CRYPTOGRAPHY: EXTENDED EUCLIDEAN ALGORITHM [EEA] - (PART 2)
Lost Bong Coder
53 views

1:30:01
CNS- Cryptography, GCD, Extended Euclidean inverse modulo, Hill Cipher, RSA algorithm
Prof. Avinash Kumar
424 views

13:50
EXTENDED EUCLIDEAN ALGORITHM || MULTIPLICATIVE INVERSE || MATHEMATICS OF ASYMMETRIC CRYPTOGRAPHY
t v nagaraju Technical
4.5K views

23:56
What Is Network Security? | Introduction To Network Security | Network Security Tutorial|Simplilearn
Simplilearn
124.2K views

1:55
Retina Network Security Scanner - Conficker Worm Serial - Retina Network Security Scanner - Conficker Wormretina network security scanner conficker worm (2015)
Jose Sanchez
2 views

43:15
cryptography and network security || cryptography and network security bangla tutorial.
Online_learning_tube
229 views

3:04:03
Cryptography and Network Security - Cryptography and Network Security Full Bangla Course
BD Techno Expert
1.2K views

9:06
A Model for Network Security in cryptography and Network Security || Cryptography and NS
Lab Mug
10.9K views

1:20
Projects on Network Security and Cryptography | Thesis on Network Security and Cryptography
Phdtopic. com
516 views

10:59
RSA Algorithm | RSA Algorithm In Network Security | RSA Encryption Algorithm | Simplilearn
Simplilearn
1.6K views

12:36
MD5 Algorithm | What Is MD5 Algorithm? | MD5 Algorithm Explained | Network Security | Simplilearn
Simplilearn
125.9K views

6:02
Introduction to cryptography and network security|network security|computers security
SCS VAJRA TUTORIALS
35 views

6:06
Need for Security | Network Security | Cryptography and Network Security
Bikki Mahato
405 views

3:57
Security Mechanisms | Network Security | Cryptography and Network Security
Bikki Mahato
184 views

9:23
MIME protocol in Cryptography and Network Security | Email security in Network Security
Abhishek Sharma
119.7K views

10:54
Secure Hash Algorithm (SHA) in Cryptography and Network Security #cryptography #networking #security
Lab Mug
11.2K views

0:08
Download Euclidean and Non-Euclidean Geometries: Development and History Ebook Online
Robinasucarterasu
8 views

7:14
Extended Euclidean Algorithm(with Example) and Modular Inverse with Examples
Abhishek Sawalkar
105 views
6:00
Extended Euclidean Algorithm and Inverse Modulo Tutorial
Best Friends Farm
932.0K views

7:31
Paper and Pencil RSA (starring the extended Euclidean algorithm)
Jenn Janesko
221.8K views
Page 1