Search Results for "Exploitation techniques"
Find videos related to your search query. Browse through our collection of videos matching "Exploitation techniques". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Exploitation techniques"
50 results found

0:56
Gold Refining Techniques Traditional Techniques vs. Modern Techniques
K-jhil Scientific
3 views

1:34
work study techniques - study techniques for students - innovative study techniques
villaelisa5000z
1 views

0:24
Binary Exploitation vs. Web Security
LiveOverflow
503.9K views
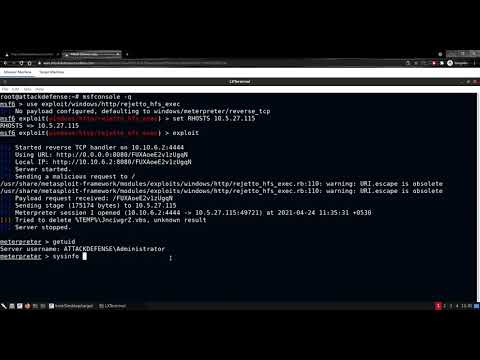
3:06
Post Exploitation With Metasploit Lab Walkthrough: FakeLogonScreen
Pentester Academy TV
1.2K views

0:41
Windows Exploitation Basics: Msfconsole | Answer the Questions Series #shorts #thm #tryhackme
CyberTodd
102 views

1:45
Un député australien met le feu à une rivière pour dénoncer l'exploitation du gaz de couche
OhMyMag FR
6 views

1:34:32
American Sweatshop 2025 full mystery thriller movie Lili Reinhart Daniela Melchior Joel Fry #AmericanSweatshop #Drama #DocumentaryStyle #SocialDrama #WorkersRights #Exploitation #EconomicStruggle #Gritty #Realism #IndieFilm #2025Movie #Powerful #ThoughtP
Daily Movies
126 views

1:45:30
Supervixens 1975 | Exploitation Film | Shari Eubank
moviextreme2024
106 views

5:19
php Calc | Web Exploitation | GrabCON CTF 2021
Rahul Singh Chauhan
1.5K views

26:27
Steganography and SUDO exploitation | Agent Sudo TryHackMe
Motasem Hamdan
1.8K views

24:25
The Future Is Female: Image-Based Sexual Abuse — Fighting Deepfake Exploitation
AWANI
61 views

13:36
Hacking Fundamentals: Enumeration And Exploitation
TheHackingLab
211 views

0:06
PDF Exploitation of Illness in Capitalist Society (The Bobbs-Merrill studies in sociology)
Gustavemanuel
1 views
0:37
🔒 Protect your computer from unauthorized access and data exploitation by turning off these.
Computer Geeks
1.5K views
27:06
Shmoocon 2013 - Hide and Seek, Post-Exploitation Style
theprez98
1.7K views

1:48
BROWSER EXPLOITATION MEME
Jo Praveen
250 views

10:41
USENIX Security '20 - TeeRex: Discovery and Exploitation of Memory Corruption Vulnerabilities...
USENIX
668 views

2:52
Practical Exploitation - Intro
practicalexplt
33 views

3:45
Meterpreter - Advanced Exploitation, Kali Linux Full Course (Part 28) by Pakfreedownloadspot.blogspot.com
HD Movies Only
95 views

5:33
Sandrine Murcia (Cosmian): Cosmian, une nouvelle approche de l'exploitation des données via le chiffrement - 08/01
BFM Business
17 views
18:14
Website Security and Exploitation in Urdu/Hindi
SUPER BEST
842 views
3:20
4LYN - Club Exploitation (Official Music Video)
4LYNTV
180 views

2:33
Lawmakers Lament Alleged Exploitation Of Electricity Consumers By DisCos
TVC News Nigeria
397 views

12:09
Keyless and Keyed Transposition techniques | Types of transposition techniques in Cryptography
Abhishek Sharma
169.7K views

5:45
CRYPTOGRAPHY & NETWORK SECURITY(7) Cryptography Techniques substitution techniques, Hill Cipher
Algorithm Pod
72 views

5:29
#8 Encryption Techniques - Substitution & Transposition Techniques |Information Security|
Trouble- Free
72.5K views

5:33
L-6.2: Collision Resolution Techniques in Hashing | What are the collision resolution techniques?
Gate Smashers
1.1M views

16:34
Rail Fence and Row Transposition cipher techniques | Types Of Transposition Techniques
Abhishek Sharma
352.9K views

7:47
CRYPTOGRAPHY & NETWORK SECURITY(6) Cryptography Techniques substitution techniques, Playfair Cipher
Algorithm Pod
67 views

13:13
Substitution Techniques in Cryptography Techniques || Cryptography and NS in Telugu
Lab Mug
17.2K views

1:38
Massage Techniques : Sports Massage Therapy Techniques
eHow
221 views
![Techniques in Prayer Therapy [PDF Download] Techniques in Prayer Therapy# [Read] Full Ebook](/image/s1.dmcdn.net/v/Cy8fq1clbokSyvy-W/xx720.pagespeed.ic.105E6k0Di1.jpg)
0:08
Techniques in Prayer Therapy [PDF Download] Techniques in Prayer Therapy# [Read] Full Ebook
Abdou Rezak
5 views
6:36
Self hypnosis techniques - conversational hypnosis techniques
Erlindarg3
4 views

10:41
Massage techniques massage techniques
Massage Club
81 views

0:21
Read Techniques in Airway Management Basic Advanced Techniques Ebook Free
Manuela Perera
1 views

0:08
Read Conservation Education and Outreach Techniques (Techniques in Ecology & Conservation)
Rose Brown 1990
0 views
![[Read PDF] Conservation Education and Outreach Techniques (Techniques in Ecology Conservation)](/image/s2.dmcdn.net/v/Hf11O1cmZK0Fg3bo6/x720)
0:25
[Read PDF] Conservation Education and Outreach Techniques (Techniques in Ecology Conservation)
DontaeBailey
5 views

2:06
Negative Techniques vs Positive Techniques
Dating Tips
24 views

1:13
BJJ Techniques - Brazilian Jiu-Jitsu Techniques
JCash1972
1 views

0:34
Normal techniques VS Indian Techniques memes_480p
Republic of Neal
2 views

25:00
Artistic Marquetry Techniques - Parquetry Techniques
Tutorials Arena
53 views

0:57
SOME BEST TECHNIQUES|Techniques
Rizwan Malik
2 views

1:02
Law of Attraction in Hindi Law of Attraction Techniques LOA Techniques
Adhyatmik Vikas Mission
0 views

0:10
Tree Grafting Techniques #tree #grafting #techniques
MakeMagic
13 views

6:23
Scissor Techniques: Learn scissor cutting techniques ...
Grant Sharp
11 views

3:35
Persuasion Techniques: 9 Effective Persuasive Techniques
The China Gadgets
2 views

4:49
CRYPTOGRAPHY & NETWORK SECURITY(5) Cryptography Techniques substitution techniques
Algorithm Pod
57 views

6:50
CRYPTOGRAPHY & NETWORK SECURITY(4) Cryptography Techniques substitution techniques, Ceaser Cipher
Algorithm Pod
88 views

7:32
L-4.1: Introduction to Greedy Techniques With Example | What is Greedy Techniques
Gate Smashers
1.2M views

15:27
CLASSICAL ENCRYPTION TECHNIQUES 1.SUBSTITUTION TECHNIQUES2.TRANSPOSITION TECHNIQUES
simplified sem tutorials
6.4K views