Search Results for "Encrypted detonators"
Find videos related to your search query. Browse through our collection of videos matching "Encrypted detonators". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Encrypted detonators"
50 results found

7:02
Separable Reversible Encrypted Data Hiding in Encrypted Image-AES Algorithm&BPCS Algorithm
MyProjectBazaar
66 views

8:36
Final Year Projects | Separable Reversible Encrypted Data Hiding in Encrypted Image
ClickMyProject
158 views
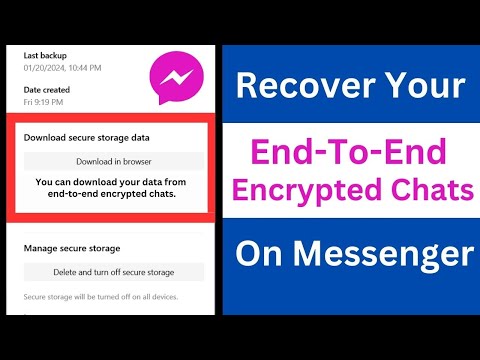
1:42
How to Recover End-To-End Encrypted Chats on Messenger | Restore End-To-End Encrypted Chats
World 360
369.3K views
0:55
(New) Turn off End to end encrypted on messenger | Turn off end-to-end encrypted (2025) #endtoend
Solution Prove
173.9K views

1:30
How To Find EFS Encrypted Files On Windows 10/11 | How To Locate EFS Encrypted Files And Disable EFS
Tech Pro Advice
723 views

0:44
Explained:Symmetric Encryption🔑 #privacy #encryption #symmetric #datasecurity #encrypted #techshorts
Way To Privacy
2.9K views

31:43
Data Hiding with Encrypted Multi Secret Sharing using Modified LSB Technique
IJERT
167 views

0:23
Does the email subject line need to be encrypted to HIPAA compliant?
Paubox
1.7K views

9:48
This Video was Not Encrypted with RSA | Infinite Series
PBS Infinite Series
76.1K views

4:10
Lossless and Reversible Data Hiding in Encrypted Images with Public Key Cryptography
SD Pro Solutions Pvt Ltd
1.0K views

0:13
End to end encrypted Whatsapp chat backup #chatbackup #whatsapp #youtubeshorts
Mobile Digital Tricks & Solutions
1.0M views

0:32
👩🏻💻Explained:Encryption ✅ #privacy #privacymatters #security #whatsapp #encryption #encrypted #data
Way To Privacy
1.2K views
3:39
End to End Encryption Sinhala | End to End Encrypted WhatsApp and Messenger | How It's Works Chat
Hiruuu Tech
5.2K views

0:36
"Encrypted Image" beneath a Full CGI.
Metro Cúbico Digital
749 views

0:25
Encrypted Meaning
SDictionary
61.6K views

3:06
Attacks on Encrypted Messages
Manju Tech Nest
61 views

4:41
Steganography: Hide Encrypted Messages, Images & Executable files inside JPG Images.
Horizon Software Engineering
251 views

14:21
Efficient and Expressive Keyword Search Over Encrypted Data in Cloud
Micans Infotech Project CSE Video 2017-2018
136 views

0:09
🕵️♀️ Kryptos: Encrypted Enigma in Granite
Lazy Learnings
45 views
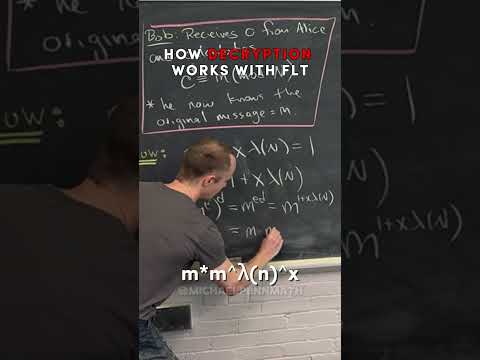
1:58
how your computer decrypts encrypted messages
Michael Penn
2.0K views

0:39
The Encrypted Letters of Alan Turing
The Untold Stories
445 views

3:16
How to Remove Cl0p (.clop) Ransomware and Decrypt Encrypted Data | #CLOP #Ransomware #Virus
Cl0p Decryptor
46 views

0:41
Encrypted email just got a blockchain UPGRADE
All Things Secured
6.2K views
1:26
OpenSSL made Easy - Part 3: Generating an Encrypted RSA Key with AES-128 🔒#shorts
SRKMasterStack
279 views

0:55
The Unsolved Mystery of Kryptos: CIA's Encrypted Sculpture #shorts
RiddleMeThis Mysteries
1.1K views

19:35
Fully Homomorphic Encrypted Facial Recognition with TenSEAL in Python
Sefik Ilkin Serengil
4.0K views

5:19
Hiding Compressed and Encrypted Data by using a Technique of Steganography
IJERT
160 views

20:22
Processing Encrypted Data
Samantha Medina
79 views
20:09
HYBRID CRYPTOGRAPHY AND STEGANOGRAPHY METHOD TO EMBED ENCRYPTED TEXT MESSAGE WITHIN IMAGE-3D-DWT
VERILOG COURSE TEAM-MATLAB PROJECT
208 views

9:34
INS: Unit-1 Symmetric cipher Model and Attacks on Encrypted Message
Twinkal Patel
1.7K views
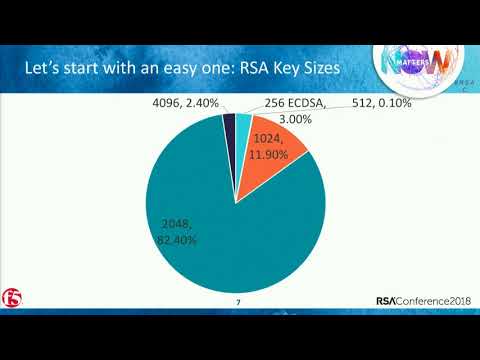
43:11
Secrets of the Encrypted Internet—Worldwide Cryptographic Statistics
RSA Conference
310 views

8:49
Lossless and Reversible Data Hiding in Encrypted Images with Public Key Cryptography
MyProjectBazaar
99 views

21:21
HYBRID CRYPTOGRAPHY AND STEGANOGRAPHY METHOD TO EMBED ENCRYPTED TEXT MESSAGE WITHIN IMAGE
VERILOG COURSE TEAM-MATLAB PROJECT
493 views
0:43
The Unsolved Mystery of Kryptos: CIA's Encrypted Sculpture!
Mystery Stories of the World 🌎
612 views

10:37
Authentication by Encrypted Negative Password in Python
OKOKPROJECTS
183 views

0:47
The Encrypted Messages of World War II
CineDecoded
54 views

54:29
Charalampos Papamanthou: Leakage Abuse Attacks in Encrypted Databases
CMU Cylab Crypto Seminar
191 views

21:16
NSDI '20 - TimeCrypt: Encrypted Data Stream Processing at Scale with Cryptographic Access Control
USENIX
924 views

21:30
Computing On Encrypted Data // Kurt Rohloff, Duality (Firstmark's Data Driven NYC)
The MAD Podcast with Matt Turck
482 views

4:40
Reversible 3D encrypted image steganography with lossless recovery using MATLAB
IEEE Projects Bengaluru
27 views

52:37
12 Jan 2015, Computing on Encrypted Data - Somewhat Homomorphic Encryption
Secure IoT at Stanford
3.8K views

59:15
Computing On Encrypted Data with C++
CoreCppIL
481 views

23:57
Efficient Boolean Search over Encrypted Data with Reduced Leakage
IACR
206 views

1:07:27
Lattices and Encrypted Computation
Simons Institute for the Theory of Computing
3.2K views

3:05
Encrypted Steganography using command prompt
HackerWorld
198 views

4:11
Separable Reversible Data Hiding in Encrypted JPEG Bitstreams
ArihantTechnoSolutions ATS
89 views

3:45
separable reversible data hiding in encrypted image FINAL BTECH - MTECH IEEE PROJECTS IN HYDERABD
TRU PROJECTS
96 views

0:21
encrypted passwords generator Using few lines of Python code#python #trending #short #shorts #viral
To-TechArea
907 views

3:25
How Is Data Encrypted With Asymmetric Encryption? - CryptoBasics360.com
CryptoBasics360
4 views

2:51
Understanding Cryptanalysis: Unlocking the Secrets of Encrypted Language
Vocabulary Vault
14 views