Search Results for "Cryptography Technique"
Find videos related to your search query. Browse through our collection of videos matching "Cryptography Technique". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Cryptography Technique"
50 results found

0:11
Cryptography techniques || Substitutional technique || Transpositional technique || UNIT 01
Online Learning
5.0K views

4:05
Substitution Cipher Technique V/s Transposition Cipher Technique in Cryptography and Network Securit
Short Tricks Learning
631 views
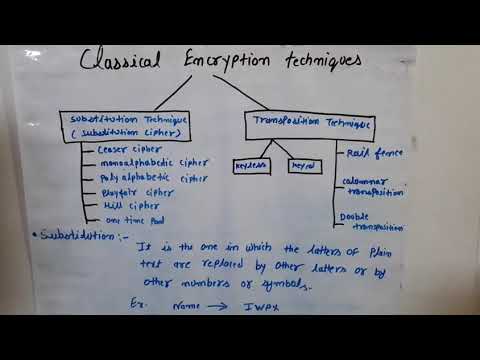
4:05
Classical encryptiin techniques, substitution technique, transposition technique
Gaurav Khatri
498 views

23:16
NIS-3.2-1 : Types of Cipher Technique (Substitution Cipher Technique, Caesar cipher)
rathod_sir
361 views

0:46
What technique do you use during competitive eating?: Competitive Eating Strategy And Technique
Scribble
1 views

5:42
Hair Cutting Technique: Mahogany Cutting Technique
Grant Sharp
8.7K views
2:25:42
Cryptography in network& computer security |Cryptography Encryption Technique| chapter three #በአማርኛ
Universal-tube
6.2K views
23:53
Caesar Cipher | Substitution Technique in cryptography explain in telugu#Cryptography #CaesarCipher
Chinni Educationalclub
4.3K views

12:27
Ceaser Cipher| Substitution Cryptography Technique | in Cryptography and Network Security
Shiksha Academic & Tutorials
464 views

5:44
CRYPTOGRAPHY & NETWORK SECURITY(8) Cryptography Techniques Transposition Technique
Algorithm Pod
66 views

36:04
''RSA technique in Asymmetric Key Cryptography'' Cryptography Network Security Lecture 04 By Ms Tah
AKGEC Digital School
10 views

3:40
What is Cryptography? | Explain Cryptography | How Cryptography Works? | Cryptography Information
Crypto & Blockchain News (CBN)
4 views
![[Cryptography] What is Cryptography? | Introduction To Cryptography | Cryptography Tutorial in Hindi](/image/i.ytimg.com/vi/8are73H9oUQ/hqdefault.jpg)
19:28
[Cryptography] What is Cryptography? | Introduction To Cryptography | Cryptography Tutorial in Hindi
Cyber Odisha
97 views

8:20
Cryptography|Cryptography in computer network | Cryptography in Matrices|Cryptography linear Algebra
Smart Studies Academy
35 views

1:15
Cryptography Projects | Cryptography Thesis | Cryptography Experts | Cryptography Projects Ideas
MatlabSimulation. Com
416 views

4:40
Cryptography|What is cryptography|Cryptography tutorial|Cryptography and network security lecture
Last Night Study
287 views

4:35
Cryptography Explained - What is Cryptography | History Of Cryptography | Types of Cryptography
Encryption Consulting LLC
404 views

0:21
Cryptography | Definition of Cryptography | What is Cryptography? | Define Cryptography
Maths With Bushra
16 views

8:37
Cryptography||Symmetric Key cryptography||Asymmetric Key Cryptography||Cryptography Notes
PPC Learning
2.3K views

4:03
cryptography, cryptography introduction, cryptography definition, cryptography example
Ahmad Hassan
7 views

4:14
Row Transposition Technique|| Cryptography and Network Security
Lab Mug
7.1K views
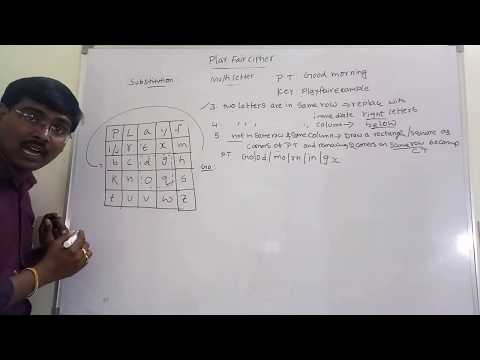
16:00
PLAYFAIR CIPHER WITH EXAMPLE||SUBSTITUTION TECHNIQUE||MATHEMATICS OF CRYPTOGRAPHY-- NETWORK SECURITY
t v nagaraju Technical
45.9K views

10:53
PART 4 | HASH FUNCTION ATHENTICATION TECHNIQUE IN CRYPTOGRAPHY & NETWORK SECURITY (BANGLA)
COMPUTER SCIENCE WITH BHASKAR SIR
229 views

10:57
Additive Shift Ceaser Cipher Technique || Lesson 5 || Cryptography || Learning Monkey ||
Wisdomers - Computer Science and Engineering
435 views
7:38
MONOALPHABETIC CIPHER || SUBSTITUTION TECHNIQUE || CRYPTOGRAPHY || LECTURE 6 || HIRALSHASTRI
Shastri Hiral
112 views

4:58
Mono Alphabetic Substitution Technique in CNS Cryptography & Network Security in Tamil
Won the ARREARS
21.9K views
11:56
Multilevel Data Concealing Technique Using Steganography and Visual Cryptography MTECH PROJECTS
TRU PROJECTS
96 views

4:51
Hill Cipher Technique | Encryption process | Cryptography | @Alfiya12
Let IT be easy
191 views

4:10
substitution cipher in hindi / Transposition technique in cryptography || #mscoder
ms coder
19.4K views

8:23
Vernam Cipher method | One time pad | Cryptography technique | @Alfiya12
Let IT be easy
285 views

12:07
A Hybrid Encryption Technique based on DNA Cryptography and Steganography | IEMCON 2022
A.I. Enthusiast
130 views
![Caesar cipher (first cipher technique) Cryptography and Network security in HINDI [ हिंदी ].](/image/i.ytimg.com/vi/efEXsGIALuE/hqdefault.jpg)
9:23
Caesar cipher (first cipher technique) Cryptography and Network security in HINDI [ हिंदी ].
Helping Tutorials
6.4K views
7:54
Vigenere cipher technique Cryptography Anna University
My Study Hour
3.6K views
8:43
Substitution Encryption & Transposition Encryption Technique in Cryptography in bangla.
content on demand
659 views

5:44
Vigenere Cipher | polyalphabetic cipher |Cryptography technique | @Alfiya12
Let IT be easy
144 views

15:00
Rabin Cryptosystem | Asymmetric Cryptographic Technique | Cryptography & Network Security
Quick Trixx
26.3K views
15:37
CAESAR CIPHER || SUBSTITUTION TECHNIQUE || CRYPTOGRAPHY || LECTURE 5 || HIRALSHASTRI
Shastri Hiral
168 views

1:01:03
A Quantum Proof Technique for Symmetric-Key Cryptography
Quiques 2021
51 views
13:43
Substition and transposition technique in cryptography and network security
VKTECHGROUP
48 views
5:20
playfair cipher #cns substitution technique cryptography and network security
all in one
205 views

4:56
Rail Fence cipher example : Rail fence cipher encryption and decryption technique in Cryptography
CSE concepts with Parinita
126.5K views

12:02
Caesar Cipher Technique in CNS (Cryptography & Network Security) in Tamil
Won the ARREARS
23.5K views
7:53
Hiding Data Using Efficient Combination of RSA Cryptography, and Compression Steganography Technique
OKOKPROJECTS
411 views

5:48
ROT13 Encryption Technique Algorithm || ROT13 Cryptography Cipher with Example
A Z Computing
9.9K views

3:14
lecture 5 classification of encryption technique in cryptography & network security #viral network
GainThroughIT
17 views

10:29
Cryptography and Network Security- Playfair Cipher Technique
Simple Engineering
930 views

13:31
Caesar Cipher | Substitution Technique in Cryptography and Network Security |CNS | WELCOME ENGINEERS
WELCOME ENGINEERS
2.9K views

4:07
Multilevel Data Concealing Technique Using Steganography and Visual Cryptography'
TRU PROJECTS
133 views

14:46
Playfair cipher technique Cryptography Anna University
My Study Hour
10.6K views

9:02
Multilevel Data Concealing Technique Using Steganography and Visual Cryptography
TRU PROJECTS
25 views