Search Results for "A Robust and Secure Video Steganography Method"
Find videos related to your search query. Browse through our collection of videos matching "A Robust and Secure Video Steganography Method". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "A Robust and Secure Video Steganography Method"
50 results found

1:53
A Robust and Secure Video Steganography Method in DWT-DCT Domains | Projects
Projectsatbangalore
218 views
0:10
A Robust and Secure Video Steganography Method
IEEE PROJECTS 2020
66 views

5:48
A Robust And Secure Video Steganography Method In DWT DCT Domains Based On Multiple Object Tracking
1 Crore Projects
109 views

1:13
Comedy videov video comedy video comedy video comedy video comedy video comedy video comedy video comedy video comedy video comedy video comedy video comedy video comedy video comedy video comedy video comedy video comedy video comedy video c
Ananad Yadav
16.3K views

0:20
Trial Advanced Windows Debugging: Developing and Administering Reliable, Robust, and Secure
virizovok
0 views
0:50
Ensuring Secure and Compliant Banking Apps Through Robust Software Testing
HeadSpin
18 views

20:32
Bisection method numerical analysis in hindi | Bisection method to find roots | Bisection Method
Mechanical in Hindi
41 views
0:09
Native video Native video Native video Native video Native video Native video Native video Native video Native video Native video Native video Native video Native video Native video
arunbalakumar
93 views

4:08
* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Vi
Layalina - ليالينا
50 views

7:15
How to secure Gmail ? || Gmail ko secure kaise kare ?क्या आपका Gmail Secure है ?
DoWithMe Start Learning
1 views
4:19
Towards Robust Image Steganography || 2019 IEEE JAVA PROJECT
Venkat Innovative Projects
426 views
0:22
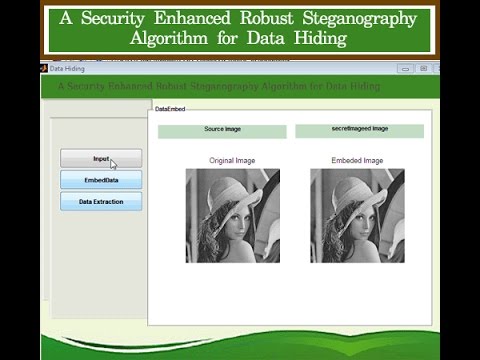
Robust Steganography Algorithm for DataHiding Matlab Project
kasanpro
159 views

1:50
steganography/steganography in hindi/steganography example/ steganography in cyber security|#mscoder
ms coder
4.5K views

3:42
Video Uploader Video Uploader Video Uploader Video Uploader Video Uploader Video Uploader Video Uploader Video Uploader Video Uploader Video Uploader Video Uploader Video Uploader Video Up
Layalina - ليالينا
133 views
5:00
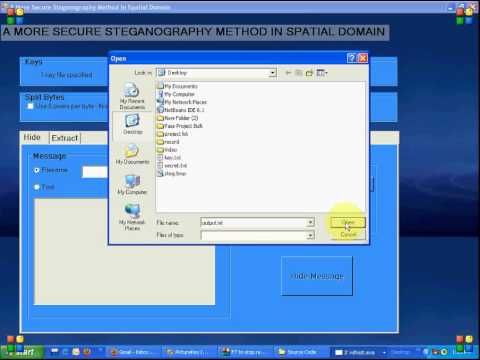
A More Secure Steganography Method in Spatial Domain -PASS 2011 IEEE Projects
pass pandian
320 views
4:42
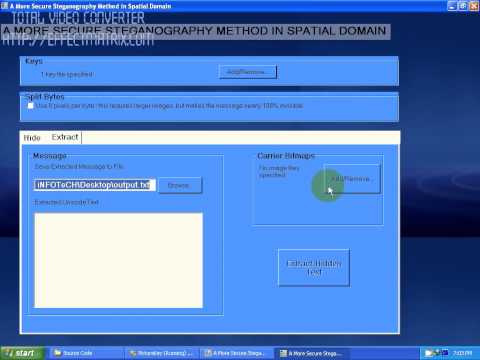
A More Secure Steganography Method in Spatial Domain
projectsnine
772 views
5:01
Steganography method to secure patients’ medical report using Wavelet Transform
Raja Sekar J
17 views
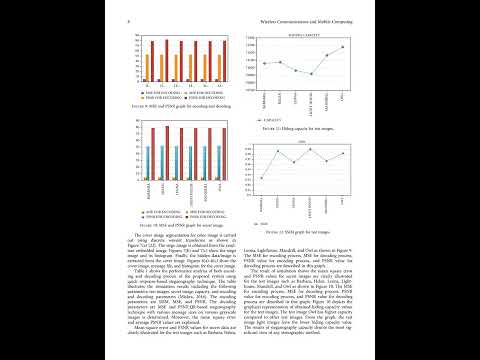
0:56
Histogram Shifting-Based Quick Response Steganography Method for Secure Communication
Electrical Engineering
166 views

3:42
* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:
Layalina - ليالينا
85 views

2:34
ROBUST VIDEO DATA HIDING USING FORBIDDEN ZONE DATA HIDING AND SELECTIVE EMBEDDING.avi
eprotechnologies
3.6K views

0:08
Read Advanced Robust and Nonparametric Methods in Efficiency Analysis: Methodology and Applications
Mtoscano
1 views

3:42
* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:* Video Title:
Layalina - ليالينا
70 views

2:21
Hide any file in a photo or a video steganography || Steganography ||steganography tutorial
Uday Kumar Madarapu
181 views
0:30
short video, short video kaise banaye, short वीडियो, short video status, short video comedy, short video viral tips and tricks, short video song, short वीडियोस, short video dance, short videos, short video bhojpuri, short video tiktok, short video viral k
Shivraj Music Bhojpuri
156 views

0:13
Difference between unconditionally secure and computationally secure in cryptography and .....
SUKANYA BASU
973 views

0:05
Read Secure Software and Comm. on Handheld Devices: Secure Software and Communication on Handheld
Isaksen
2 views

7:01
Robust visual cryptography-based watermarking scheme for multiple cover images and multiple owners
MyProjectBazaar
133 views
![Hartmut Neven (Google) [Jan 2012, NASA QFTC] Robust Classification with Non-Convex Loss and...](/image/i.ytimg.com/vi/9W8HKDkRwe4/hqdefault.jpg)
35:00
Hartmut Neven (Google) [Jan 2012, NASA QFTC] Robust Classification with Non-Convex Loss and...
Saul Colquhoun
894 views

24:06
Robust Inference and Local Algorithms
Simons Institute for the Theory of Computing
412 views

23:21
Symmetric Key Exchange with Full Forward Security and Robust Synchronization
IACR
315 views

9:35
'We Are Seeing Robust Demand In AC Sales Due To Festive Season And GST Rate Cuts': PG Electroplast
NDTV Profit Markets
1.3K views
5:32
RRW—A Robust and Reversible Watermarking Technique for Relational Data
Naren Projects
352 views
35:45
Tree-Ring Watermarks: Fingerprints for Diffusion Images that are Invisible and Robust (Explained)
Yannic Kilcher
29.4K views

0:06
Download Algebraic and Differential Topology of Robust Stability PDF Free
Maral Janikyan
4 views

2:09
RRW - A Robust and Reversible Watermarking Technique for Relational Data 2
Projects Goal
1 views

0:34
Engineering Methods for Robust Product Design: Using Taguchi Methods in Technology and Product
panubiw
1 views

6:30
What tools are available for developing robust financial models, and how do they enhance the modeling process?
eTrainerbox
65 views
7:41
Robust watermarking Of Compressed And Encrypted Jpeg2000 Images
chennaisunday.tn
29 views

0:45
Forward and reverse blood grouping method. How to prepare cell suspension for reverse method? Next
Pathofied Mindful tips
2.5K views

0:58
"The Most Secure Method Are Telegram And WhatsApp" Bryce Case Jr - Shawn Ryan Show
Armed Sphere
39.2K views

0:07
“Increase your business operations with Paymaxima secure and innovative online payment method”.
Fatima Tahir
11 views

1:10
My video My video My video My video My video My video My video My video My video My video
AJ
85 views

4:18
Funny video #comedy #video #comedy #video #comedy #video #comedy #comedy #comedy #comedy #comedy #comedy #comedy #comedy #comedy #comedy #comedy #comedy #comedy #comedy #video #comedy #video #comedy #video #comedy #video #funny #video #funny #video
kainatking66
64.1K views

4:10
Difference between Computationally Secure and Unconditional Secure Cipher | Information Security
Easy Engineering Classes
6.4K views

3:26
Matlab Image Processing Project - Robust Reversible Watermarking in Encrypted Image - ClickMyProject
ClickMyProject
54 views
13:34
A Novel Robust Zero-Watermarking Algorithm for Medical Images
COMPUTER GRAPHICS INTERNATIONAL 2021
545 views

4:45
Hashing vs Encryption: Powerful Techniques for Robust Data Protection
Learn Cybersecurity
37 views
14:16
Color Image Encryption Using Robust Chaotic Map
Lab of Nonlinear Systems - Circuits & Complexity
386 views

59:55
Algorithmic High Dimensional Robust Statistics I
Simons Institute for the Theory of Computing
2.4K views

1:04:27
Algorithmic High Dimensional Robust Statistics II
Simons Institute for the Theory of Computing
979 views