Search Results for "man in middle attack in cryptography"
Find videos related to your search query. Browse through our collection of videos matching "man in middle attack in cryptography". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "man in middle attack in cryptography"
50 results found

11:47
Man in the middle attack in Diffie Hellman Key Exchange | Prevention against Man in Middle Attack
Chirag Bhalodia
72.5K views

1:24
ten10@attack Lions attack Animal attack Top Attack to Animal Attacks And Loves when animals attack
Le Monde Artistique
129 views

4:00
What is man-in-the-middle Attack in hindi | mitm attack in hindi | HOW MITM WORKS #mitm
Charon19d
225 views

2:58
passive attack and active attack in hindi / passive attack and active attack difference ||#mscoder
ms coder
3.9K views

20:04
Diffie-Hellman Key Exchange & Man-in-the-Middle Attack #21is71 #cryptography #networksecurity #VTU
VTU padhai
3.7K views
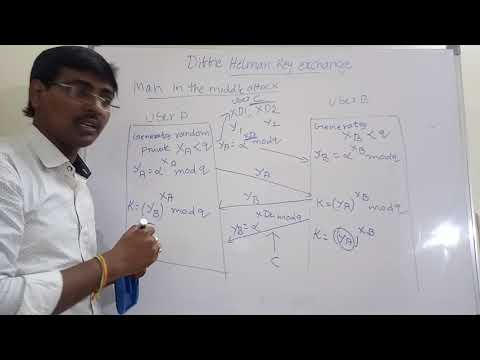
16:29
DIFFIE HELLMAN KEY EXCHANGE || MAN IN THE MIDDLE ATTACK || EXAMPLE || ASYMMETRIC KEY CRYPTOGRAPHY
t v nagaraju Technical
46.1K views

1:18
DES-Brute Force attack-in cryptography/ define brute Force attack/what is brute Force attack
Cse View
1.8K views

7:24
Symmetric Keys, Asymmetric Keys, Public Key Encryption And Man In The Middle Attack
Akshay N
18 views
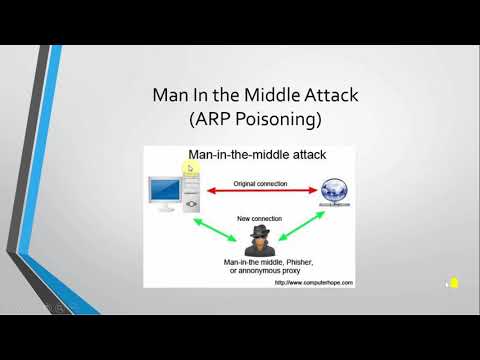
7:28
40. Network Hacking: What Is Man In The Middle Attack & How To Perform It Using ARP Poisoning
Tutorials By IT Consultants
643 views

0:51
Man-In-The-Middle Attack Explained #hacking #security
ByteQuest
11.2K views
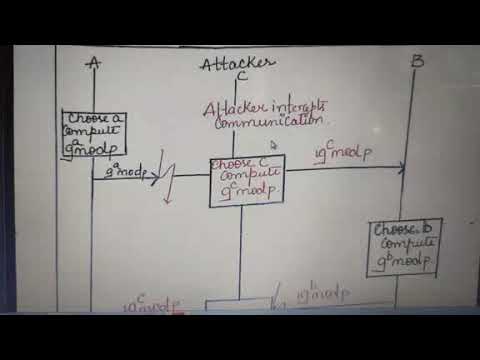
8:01
man in the middle attack
Mala Gowda
51 views
2:51
Man in the Middle Attack | MITM | Cyber Security | Short Intro
Techie AB
389 views

0:26
Man in the middle attack hindi 🔥
Hacking In Hindi
38.8K views

0:24
CyberSecurity Definitions | Man in the Middle Attack
Relative Security
969 views
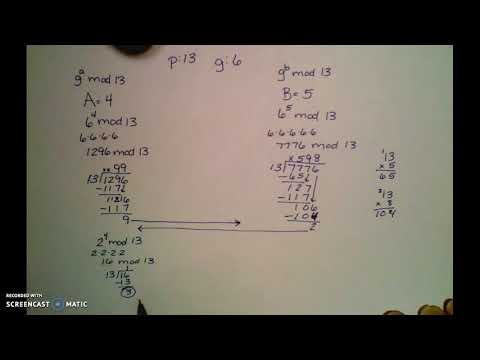
13:37
The Math of Diffie Hellman with Man in the Middle Attack
Amanda Sopko
1.3K views

26:11
No Good Nick - Se1 - Ep09 - The Man in the Middle Attack HD Watch
bekiirsaylicomam
1.0K views

3:49
Daphne Loves Derby - Middle Middle (acoustic)
Xenia Tanaka
1 views

33:34
Ancient King’s Highway in Middle East - MIDDLE EAST TOUR ON MOTORCYCLE
Tootie Leaks
2 views
![@New Middle East, Islamic Middle East [Eng]](/image/s1.dmcdn.net/v/3W-Of1e0Ilh7-x6dc/x720)
4:50
@New Middle East, Islamic Middle East [Eng]
i.awakening79
16 views
![@New Middle East, Islamic Middle East [Arabic]](/image/s2.dmcdn.net/v/3W_uK1e8mPEs6ItlZ/xx720.pagespeed.ic.vQGTLrzOJm.jpg)
4:50
@New Middle East, Islamic Middle East [Arabic]
i.awakening79
17 views

3:02
Difference between Active and Passive attack | Active vs Passive attack | Passive vs Active attack
Chirag Bhalodia
15.9K views
0:58
Heart Attack: Early Signs and Symptoms - What is a heart attack Hindi Urdu | What Causes a Heart Attack?
All viral available
13 views

1:31
Attack! Attack! Attack
mtwmike
19 views

8:49
Piranha Attack on Humans [Animals Attack, Animal Attacks, Piranha Attacks, Piranha Attack
Leann Coronel
2 views

19:23
DDoS Attack | DDoS Attack Explained | What Is A DDoS Attack? | Cyber Attacks Explained | Simplilearn
Simplilearn
43.0K views

17:12
Dos and Ddos attack | Dos attack | denial of service attack | lecture 35
Simply Made
104.8K views

0:53
Dictionary attack in Cryptography|Cryptography attack
Cse View
79 views

6:21
Wow Crazy Man Crazy Crazy Man Crazy Man Crazy Man
X Series
16 views

6:18
Play Doh Spider Man | Spider Man | How To Make Spider Man | Spider Man Toys
Margarettong39
23 views

0:25
Balance man! Passe Man! Shoot Man! Vas y marque Man!
Melot
4 views

6:45
Intro to Encryption, in Friendly Terms: Cryptography, AES, Man In The Middle, and HTTPS
Studying With Alex
10.2K views
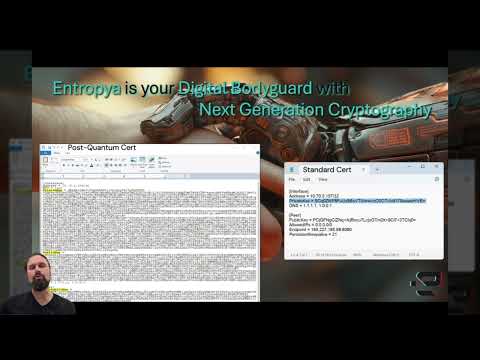
0:59
How Post‑Quantum Cryptography Stops Man‑in‑the‑Middle Attacks
Entropya
31 views
9:17
Another Big Attack | Pak Afghan Conflict | Middle East Updates | 5 AM News Headlines | 1 NOV 2025
SAMAA TV
97.0K views

6:25
What Is Men in Middle Attack || Full Explanation In Hindi || By UnOfficial_Hacker02
UnOfficial_Hacker02
37 views

0:10
Volleyball Attack Training For Middle Blockers #volleyball #shorts #training #drill #sports #fivb
Mikhail Karpol
58.3M views
14:11
Pak-Afghan Ceasefire | Another Big Attack | Middle East Updates | Petrol Price |10AM Dunya Headlines
Dunya News
17.2K views

0:21
Meet-in-the-Middle Attack, Cybersecurity Mini Dictionary #shorts
Datasafe World
11 views

16:29
Birthday Attack in Cryptography | Part 2 | How to attack a Person | Explained In Hindi | AR Network
A.R Network
803 views

6:26
Active Attack in network security | Types of security attack in cryptography | What is cryptanalysis
Chirag Bhalodia
17.2K views

14:08
Low Exponent Attack | Attacks on RSA | Protocol Failure Attack | Cryptography & Network Security
Quick Trixx
11.4K views

4:58
Passive Attack in network security | Types of security attack in cryptography | Cryptanalysis
Chirag Bhalodia
27.5K views

14:37
Cryptography Part 4: Cryptanalysis, Attack Surfaces, Attack Trees
Tech Lover
2.3K views

12:16
Common Modulus Attack | Attacks on RSA | Protocol Failure Attack | Cryptography & Network Security
Quick Trixx
14.1K views

9:09
Birthday Attack in Cryptography | How to attack a Person | Explained In Hindi | AR Network
A.R Network
15.8K views

15:53
Cryptography and Network Security Attacks | Active Attack Vs Passive Attack | Steganography | AKTU
Edu Desire
1.9K views
7:26
IT Sicherheit #13 - Asymmetrische Krypto und Man in the middle Angriffe
The Morpheus Tutorials
18.4K views
0:06
Man in the middle
Quick Cybersecurity Study
449 views

9:20
Man in the Middle (MITM) Attacks theory with ARP||How ARP Poisoning used in MITM||Coder-K||MITM||ARP
CODER-K
153 views

8:38
Theorie: Man-In-The-Middle Attacke
SecureOne1000
3.4K views

17:46
DHCP Exhaustion and DNS Man-in-the-Middle Attacks - Hak5
Hak5
3 views