Search Results for "hmac sha256 explained"
Find videos related to your search query. Browse through our collection of videos matching "hmac sha256 explained". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "hmac sha256 explained"
50 results found

10:26
Razorpay integration in asp.net web app | HMac SHA256 signature create and matching
New Arts
1.4K views

11:03
Learn the ART of CRYPTOGRAPHY - SHA-1 HMAC Hashing Explained (Urdu/Hindi)
Cybersecurity Academy - CertificationHUB
184 views
20:58
16-HMAC Algorithm Explained 🔐 | Hash-Based Message Authentication Code in Network Security
Sundeep Saradhi Kanthety
168.4K views
6:33
HMAC explained | keyed hash message authentication code
Jan Goebel
85.3K views
1:00
🔐 Brute Force Hashing & SHA256 Explained!
TechVerseTrends
242 views

0:27
How Bitcoin Stays Secure - SHA256 & Mining Explained
THE BIT INSIGHT
282 views

2:14
Bitcoin Security Explained: The Role of SHA-256 #sha256 #bitcoin #cryptocurrency
Cryptocurrency Guide
39 views

12:36
Hashing and Hash Cracking Explained Simply! (2021) | MD5, SHA1, and SHA256
Josh Madakor
22.3K views
1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views
7:24
Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - Cryptography
Practical Networking
77.9K views
7:05
HMAC - Cryptography I
Nguyen Duong Anh
80 views

6:52
MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes
Practical Networking
30.0K views

8:10
#36 HMAC (Hash Based) & CMAC (Cipher Based) |CNS|
Trouble- Free
232.6K views
22:00
CNS HMAC
Kallam Gopala Reddy
312 views

9:00
HMAC and CMAC in Cryptography Hash Function || Network Security in Telugu
Lab Mug
10.9K views

9:24
Securing Stream Ciphers (HMAC) - Computerphile
Computerphile
326.5K views
20:35
HMAC | Cryptography and Network Security
Ekeeda
677 views
1:09:59
Go UUID HMAC
Learn To Code
945 views

0:46
HMAC Promo take 2
Players 2Pros
29 views

12:48
Função de Hash - MD5 e SHA - Código HMAC - Aula completa
Prof. Sergio Villarreal
3.7K views
57:46
Applied Cryptography: 3. Hash functions and HMAC
Applied Cryptography by University of Tartu
635 views
29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views
8:08
MAC in Hindi - Message Authentication Code Process, Significance, HMAC Concept
Easy Engineering Classes
111.9K views

13:49
V4b: CBC-MAC and HMAC (Applied Cryptography 101)
Cryptography 101
1.1K views
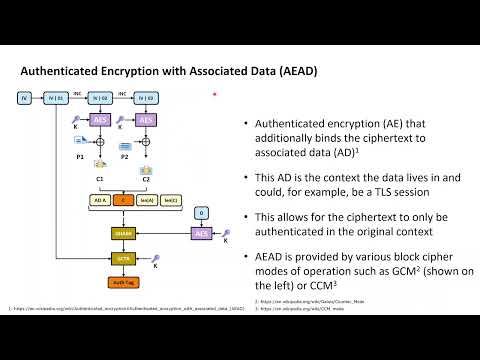
12:51
Cryptography with Python 30: HMAC, Encrypt-then-MAC and GCM
Cyrill Gössi
1.1K views
5:15
HMAC Nested MAC Method || Lesson 73 || Cryptography || Learning Monkey||
Wisdomers - Computer Science and Engineering
1.1K views

11:19
MAC function ,HMAC,CMAC in Cryptography and cyber security tamil||CCS||Anna university reg-2021.
Murugan Tech World
7.8K views
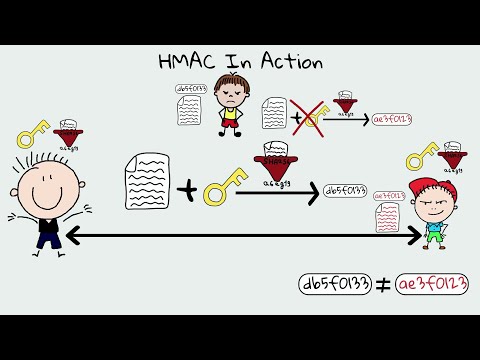
6:09
HMAC & Message Authentication Codes (MACs) - Why Hashing alone is NOT ENOUGH for data integrity
JayPMedia
6.7K views

9:40
Message Authentication Codes: CMAC and HMAC
Cihangir Tezcan
4.8K views

7:40
MAC Based on Hash Function | HMAC in network security
Chirag Bhalodia
67.7K views
14:13
#4 Why do we need cryptography hash functions SHA256 for blockchain network?
FuTech
274 views
![Basics of Crypto Part 1 - Block (SHA256 Cryptographic Hash Function) [Compact]](/image/i.ytimg.com/vi/DELAC8fWOR8/hqdefault.jpg)
1:55
Basics of Crypto Part 1 - Block (SHA256 Cryptographic Hash Function) [Compact]
Unofficed
135 views

0:42
🔐 What is SHA-256? | How This Powerful 🔢 Hash Function Keeps Your Data Secure! 🛡️#sha256 #crypto
BitnByte Mining
8.1K views

6:03
Hashing and Hashing Algorithms - md5 sha1 sha256 sha2 sha3 - Cryptography Essentials
Practical Networking
25.0K views
![[Hindi] What is Hashing with Example | Hashing Algorithm | MD5 | SHA256](/image/i.ytimg.com/vi/tzB5VD-DzJE/xhqdefault.jpg.pagespeed.ic.U_7ZbE_rYf.jpg)
4:02
[Hindi] What is Hashing with Example | Hashing Algorithm | MD5 | SHA256
Cyber Aware Hub
27.0K views

3:18
Rainbow table Attack | Password MD5, SHA1, SHA256, Salting | EP18 | Hacking | Cyber security | Tamil
Micah Tech
1.2K views

1:09:43
Cryptography Basics Part 1 | Symmetric & Asymmetric Encryption | RC4, AES, DES, MD5, SHA256, Cipher
LearnwithPinaki
39 views

5:39
Bitcoin Technologie für Anfänger - Bitcoin SHA256 erkärt! (Kryptographie & Dezentralität)
Kryptoranden
292 views

1:00
₿ BITCOIN verschlüsselung SHA256 wie gross ist 2 hoch 256 genau?
BtcBrienz
131 views

16:20
Como Funciona a Criptografia e SHA256? - Exemplo em Python
Hashtag Programação
23.3K views

0:25
SHA256 é a chave para o Futuro do Bitcoin
CortesPodcast XD
4.0K views
12:29
Hashing Files in Python | Hash Generator Using Hashlib (md5, sha256, etc)
Fabio Musanni - Programming Channel
28.7K views
3:36
How To Create Hash SHA256 With PHP
Ridho Tegar
3.4K views
0:58
Bitcoin vs Computação Quântica ECDSA x SHA256
EddieOz
172 views

0:54
hashing #cybersecurity #securityplus #comptia_security #encryption #hashing #md5 #sha256
Lessons With Ricardo
422 views
6:22
Controle SHA256 sur ISO Debian
Association infothema
1 views
3:56
How To Make SHA256 Hash Converter (VB.NET)
Lifestyle
7 views

2:09
Bitmain Antminer Bitcoin Miner S19 Pro Hyd. 184T 5428W SHA256 Hydro-cooling Mining Machine
Apexto Mining
13 views

0:17
Bitmain Antminer S9 Sha256 ASIC miner money БИТКОИН Асик майнер майнинг how to earn money как заработать деньги
Adema Adema
4 views

28:17
Parte 1 - Introdução ao Algoritmo SHA 256 - Secure Hash Algorithm SHA256
Laboratório de Inutilidade Pública
7.2K views