Search Results for "SHA-1 Vulnerabilities"
Find videos related to your search query. Browse through our collection of videos matching "SHA-1 Vulnerabilities". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "SHA-1 Vulnerabilities"
51 results found

7:31
SHA 1, SHA 224, SHA 256, SHA 384, SHA 512 Hashing - Cryptography with Python
lazy tutorials
2.7K views

1:39
SHA Happy Birthday Song – Happy Birthday SHA - Happy Birthday Song - SHA birthday song #SHA
Greetings with name
223 views

14:50
SHA 256 | SHA 256 Algorithm Explanation | How SHA 256 Algorithm Works | Cryptography | Simplilearn
Simplilearn
179.4K views

11:42
SHA 1 | Secure Hash Algorithm | Working of SHA 1 | Parameters of SHA512 and SHA 256
Chirag Bhalodia
73.4K views

1:40
Hashing Explained: MD5, SHA-256, SHA-512 & Digital Signatures | Security+ in 60 Seconds
Cyber Buddy
72 views

10:16
SHA – Secure Hash Algorithm in Hindi - Properties, Working, Comparison b/w SHA and MD5
Easy Engineering Classes
196.1K views
12:16
How Does SHA-1 Work - Intro to Cryptographic Hash Functions and SHA-1
Fullstack Academy
69.1K views

0:57
Understanding SHA-1 & SHA-256 Hash Functions Explained
TWiT Tech Podcast Network
7.8K views

0:29
World of Warcraft Patch 5.4: Sha of Pride (Sha de l'Orgueil)
JudgeHype
211 views
0:56
How to Get SHA1 or SHA-256 key in Android Studio for firebase Flutter | Easy & First Tricks. Sha-1 Key Terminal Flutter.
Instructive Tech
5 views

25:17
CS C S009 Non-Cryptographic Protocol Vulnerabilities
Studio IIT Bombay
539 views
38:56
Nmap Tutorial For Beginners | Nmap Tutorial to find Network Vulnerabilities | Amader Canvas
Amader Canvas
45.1K views

5:45
Threats Vulnerabilities and Exploits
IBM Technology
34.4K views

2:26:01
Virtual Machine Reset Vulnerabilities; Subspace LWE; Cryptography Against Continuous Memory Attacks
Microsoft Research
314 views

20:58
Hackers expose deep cybersecurity vulnerabilities in AI | BBC News
BBC News
524.3K views

1:11:10
Black Hat EU 2010 - Hiding in the Familiar: Steganography & Vulnerabilities in Pop Archives Formats
Black Hat
231 views

29:23
Quantum Threat: Impact of Quantum Computers on Cybersecurity | Threats & Vulnerabilities Summit 2025
Cloud Security Alliance
155 views

10:41
USENIX Security '20 - TeeRex: Discovery and Exploitation of Memory Corruption Vulnerabilities...
USENIX
668 views

10:01
Blackhat Europe 2010: Steganography and Vulnerabilities in Popular Archives Formats 7/8
Christiaan008
148 views

17:37
TWIM Episode 2: Sodinokibi Ransomware Vulnerabilities & Maryland Criminalizes Malware Possession
This Week in Malware
66 views
0:33
SQL Injection 101: Exploiting Vulnerabilities
CyberSquad
354.4K views

0:18
Critical Go Parser Vulnerabilities Enable Authentication Bypass and Data Theft in Production Systems
Secure Thread
122 views

9:35
Data Exfiltration Vulnerabilities in LLM Applications and Chatbots: Bing Chat, ChatGPT and Claude
Embrace The Red
1.9K views

2:56
How Common are Cryptographic Vulnerabilities?
Cryptosense
615 views

4:48
What Are The Biggest Microservices Security Vulnerabilities? - Next LVL Programming
NextLVLProgramming
6 views

10:01
Blackhat Europe 2010: Steganography and Vulnerabilities in Popular Archives Formats 1/8
Christiaan008
1.8K views

5:35
Cryptography Basics: Symmetric and Asymmetric Cryptography - Identifying Security Vulnerabilities
Petrina Corine
25 views

2:06:36
Cybersecurity Assets, Network Threats & Vulnerabilities | Google Cybersecurity Certificate
Google Career Certificates
153.5K views

34:39
Cryptography careers and IoT vulnerabilities | Cyber Work Podcast
Infosec
4.0K views

0:32
How Attackers Exploit Diameter Protocol Vulnerabilities
Offensive Wireless
523 views
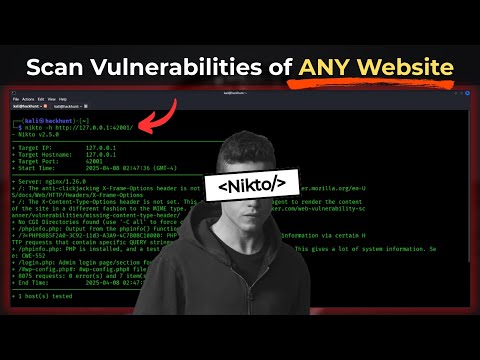
3:27
How Hackers Scan Vulnerabilities of Any Website | Nikto - Kali Linux
HackHunt
30.0K views

10:01
Blackhat Europe 2010: Steganography and Vulnerabilities in Popular Archives Formats 6/8
Christiaan008
194 views

8:44
Armitage- Scanning a network for computers and finding their Vulnerabilities
DonDoes30
19 views

5:10
Exploiting Windows Vulnerabilities with Metasploit
Hak5
831 views

0:47
Researchers Discover New Vulnerabilities In Common Email Encryption Tech
Entertainment (now)
5 views

0:46
Risks Are Accelerating, Yet Traditional Security Vulnerabilities Plague Cryptocurrencies
Benzinga
14 views

1:59
Week 1 Rust And Vulnerabilities: Bengals Vs. Browns
SportsGrid
3.2K views
0:41
911 Outage Sparks Concerns Over Emergency System Vulnerabilities
Benzinga
610 views

1:04
The Weeknd has used music to 'hide' his vulnerabilities
Bang Showbiz
486 views

1:32:49
RWPQC 2024 Session 5: Applied Cryptography, Vulnerabilities, and Countermeasures
SandboxAQ
26.2K views

41:17
CS M S022 Non-Cryptographic Protocol Vulnerabilities
Studio IIT Bombay
429 views

3:21
How Does The Rise Of AI Impact Military Cryptography Vulnerabilities? - Tactical Warfare Experts
Tactical Warfare Experts
17 views

28:17
Parte 1 - Introdução ao Algoritmo SHA 256 - Secure Hash Algorithm SHA256
Laboratório de Inutilidade Pública
7.2K views

37:17
How we created the first SHA-1 collision and what it means for hash security - Defcon 25
Elie Bursztein
9.2K views

25:20
Asymmetric Key Cryptography & Hashing Explained | RSA, DSA, SHA-256 in Blockchain Part 03 Hindi 2025
Akshay Kurhekar
116 views

0:35
Cracking The Code - Exploring Secure Hash Algorithms - SHA Short #cybersecurity #hashing
Technically U
1.1K views
6:09
cryptography and network security sha 3 keccak and ripemd 160
CodeMade
14 views

6:17
Bitcoin & SHA-256 Explained With Animations
I Explain Crypto
1.1K views

10:03
Cryptography Hashing functions SHA and specificaly SHA1 hashing
Alon Lalezari - אלון ללזרי
11 views

28:38
#ክሪፕቶግራፊ How Blockchain Uses SHA-256 for Cryptographic Hashing | Simplified in Amharic
Self Programmers
268 views

1:59
Week 1 Rust And Vulnerabilities: Bengals Vs. Browns
SportsGrid
3.2K views
Page 1 Next