Search Results for "Cryptographic protocols"
Find videos related to your search query. Browse through our collection of videos matching "Cryptographic protocols". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Cryptographic protocols"
50 results found

0:59
Protocols | meaning of Protocols
The Definition Channel
504 views

0:11
network protocols and ports | networking protocols interview questions
Technical Spartan - Thakur
149.4K views

1:21
Solar Energy - Renewable Energy - Montreal Protocols & Kyoto Protocols
Cyber Energy Ltd
11 views

0:08
Read [ AACN Protocols for Practice: Noninvasive Monitoring[ AACN PROTOCOLS FOR PRACTICE: NONINVASIVE
Airini Arono
0 views

0:05
Download Telephone Triage Protocols for Adults 18 Years and Older (Telephone Triage Protocols
MarianRench
1 views

0:35
Best product Telephone Triage Protocols for Nurses (Briggs, Telephone Triage Protocols for
walker
1 views
![[Read] TCP/IP Illustrated, Volume 1: The Protocols: The Protocols v. 1 (Addison-Wesley](/image/s2.dmcdn.net/v/Pt3_y1e9_0lvZvH-V/xx720.pagespeed.ic.GE78wmqjuE.jpg)
0:33
[Read] TCP/IP Illustrated, Volume 1: The Protocols: The Protocols v. 1 (Addison-Wesley
phamza-elhaddars
7 views

0:36
TCP/IP Illustrated, Volume 1: The Protocols: Protocols v. 1 (APC) Review
yoheg
5 views

4:37
Adherence to Covid-19 Protocols: Clamp-down on persons violating protocols begins (10-8-21)
The Multimedia group
3 views

23:38
The Price Of Active Security In Cryptographic Protocols
Fidelity Center for Applied Technology (FCAT®)
31 views

6:06
Unplugged: The show. Part 8: Cryptographic protocols
UC Computer Science Education
14.4K views

1:38:51
PETS 2022 Moti Yung Keynote Privacy Integrated Computing” Cryptographic Protocols in Practice
All Hacking Cons
17 views

42:40
AppSecIL 2018 - How to hack cryptographic protocols with formal methods, Ofer Rivlin
OWASP Israel
112 views

3:46
An assessment of cryptographic protocols susceptible to quantum attacks
Aliro
63 views
![[PriSC'25] Keynote: Bringing Verified Cryptographic Protocols to Practice](/image/i.ytimg.com/vi/3mshgSCvH40/hqdefault.jpg)
1:00:28
[PriSC'25] Keynote: Bringing Verified Cryptographic Protocols to Practice
ACM SIGPLAN
32 views
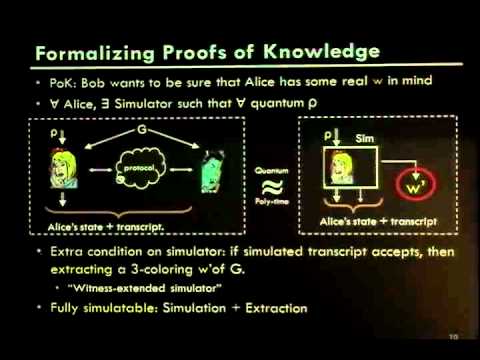
19:25
Classical Cryptographic Protocols in a Quantum World
IACR
532 views

38:57
HOPE Number Six (2006): Constructing Cryptographic Protocols
Channel2600
112 views
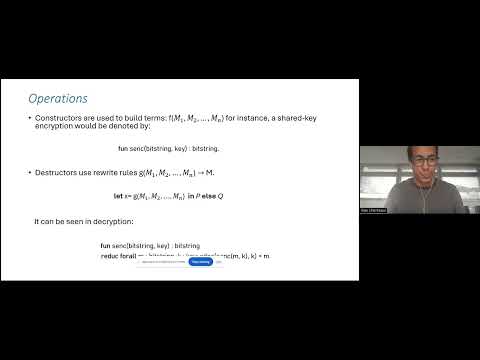
![[POPL'23] A Core Calculus for Equational Proofs of Cryptographic Protocols](/image/i.ytimg.com/vi/5rQstrKftGE/hqdefault.jpg)
25:50
[POPL'23] A Core Calculus for Equational Proofs of Cryptographic Protocols
ACM SIGPLAN
291 views

27:51
Cryptographic Protocols
GNS S
203 views

28:26
Ran Cohen - Probabilistic Termination and Composability of Cryptographic Protocols
DIMACS CCICADA
113 views

9:23
Innovations in Cryptographic Protocols: Interview with Dr. Muhammed Ali Bingol | Computing 2024
SAIConference
234 views
20:51
Verification of cryptographic protocols. ilias Cherkaoui (Walton Institute, Ireland)
Muhammad Usama Sardar
16 views

2:48
Securing Digital Assets: Cryptographic Protocols for Data Catalogs Explained
Operational Excellence Mastery
6 views
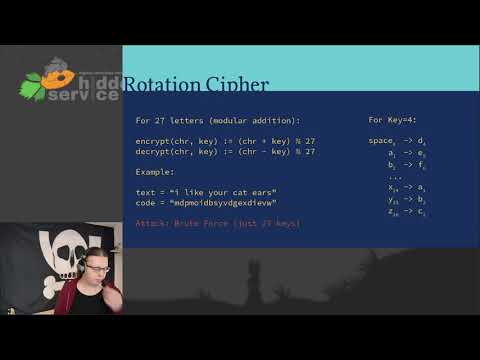
50:35
DiVOC20 - Quantum Hardening Cryptographic Protocols - EN
media.ccc.de
5.0K views

3:10
What Are Cryptographic Protocols? - Next LVL Programming
NextLVLProgramming
96 views

38:57
HOPE Number Six 2006 Constructing Cryptographic Protocols
All Hacking Cons
3 views
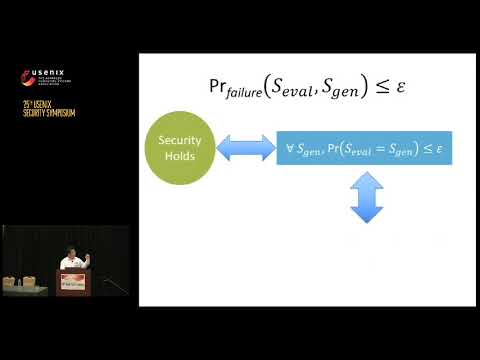
21:55
USENIX Security '16 - The Cut-and-Choose Game and Its Application to Cryptographic Protocols
USENIX
186 views

19:47
Cryptographic Protocols By Sunil Chebolu, Undergraduate Colloquium in Mathematics ISU, Part-2
P Sravya
146 views
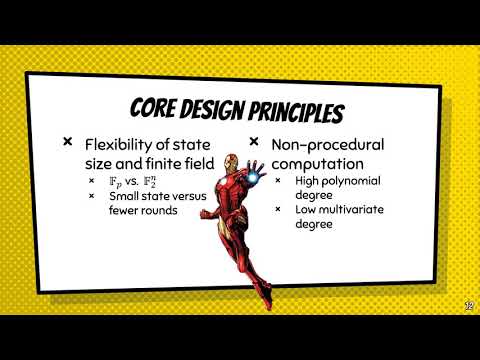
21:17
"Design of Symmetric-Key Primitives for Advanced Cryptographic Protocols" (FSE 2020)
COSIC - Computer Security and Industrial Cryptography
139 views
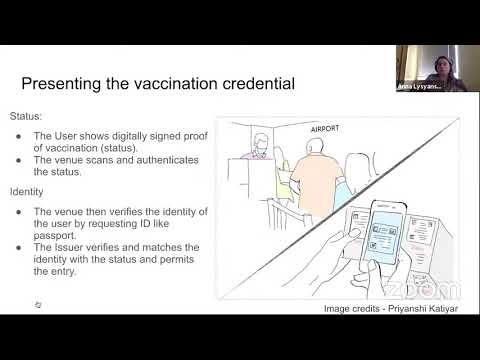
27:52
Cryptographic Protocols for Vaccine Eligibility, Dose Coordination, and Reporting Side Effects
cameraculturegroup
6 views

4:35
How Do VPNs Use Cryptographic Protocols? - Next LVL Programming
NextLVLProgramming
6 views

2:47
Locking Down Data: Cryptographic Protocols for Secure Communication Explained
Operational Excellence Mastery
6 views
1:03:26
Automatically Binding Cryptographic Context to Messages in Network Protocols Using Formal Methods
UCYBR - UMBC Center for Cybersecurity
60 views

2:11:01
Day 3 Session 2 / Distributed Cryptographic Protocols II
Ingeniería, Ciencia y Tecnología - URosario
66 views
29:49
Security Protocols: Lecture 7b (Cryptographic Storage)
Antonis M
266 views

21:17
Design of Symmetric-Key Primitives for Advanced Cryptographic Protocols
IACR
225 views

0:18
What are cryptographic protocols?
Intelligence Gateway
82 views
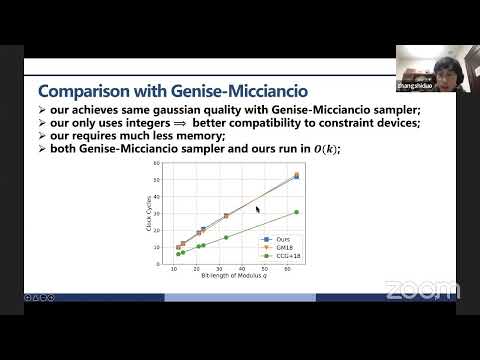
1:11:02
session-14: Cryptographic Protocols + Tools
IACR
259 views
1:09:14
s-20: Cryptographic Protocols and Secure Computation II
IACR
361 views

2:45
The Fascinating World of Cryptographic Protocols
BITCOIN HARDER
9.4K views

21:02
The Price of Active Security in Cryptographic Protocols
Rg G
2 views

8:07
3 14 Applying Cryptography Cryptographic Protocols CISSP
cissp kuwait
57 views

25:09
Card-based cryptographic protocols for three-input functions using private operations
Fields Institute
139 views
17:13
Clear-text Vs Cryptographic Protocols | Network Security // Perumal Jegan
Perumal Jegan
194 views
9:41
Cryptographic Protocols CompTIA Security+ Study Session 21 August 2020
Cyberkraft
52 views

15:46
🌟🔒 Preparing for Quantum Threats Developing Quantum Resistant Cryptographic Protocols
Science News
10 views

58:51
MPC-TP: Probabilistic Termination and Composability of Cryptographic Protocols - Juan A Garay
CrIS Lab IISc
127 views

58:41
Cryptographic protocols in the era of cloud computing
All Hacking Cons
8 views
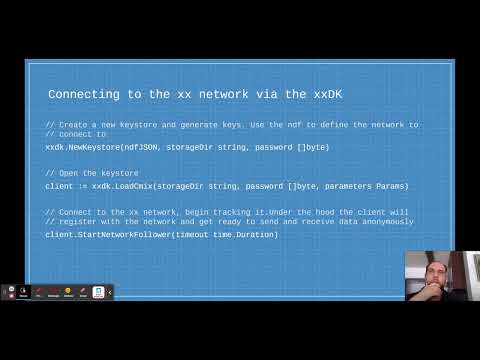
10:01
Preserving a user’s anonymity with cryptographic protocols | BeWater DevCon II
BeWater Community
257 views
39:30
An Industry Perspective On Automated Analysis For Designing Cryptographic Protocols - Marc Ilunga
BlackAlps CyberSecurityConference
71 views
Page 1