Search Results for "importance of security protocols"
Find videos related to your search query. Browse through our collection of videos matching "importance of security protocols". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "importance of security protocols"
50 results found

0:13
Importance of education l essay on importance of education l speech on importance of education
Study Yard
1.1M views

1:50
THE IMPORTANCE OF PATIENCE, IN SUCCESS #IMPORTANCE #Motivation
Popular World
22 views

0:59
Protocols | meaning of Protocols
The Definition Channel
504 views

0:11
network protocols and ports | networking protocols interview questions
Technical Spartan - Thakur
149.4K views

1:21
Solar Energy - Renewable Energy - Montreal Protocols & Kyoto Protocols
Cyber Energy Ltd
11 views

0:08
Read [ AACN Protocols for Practice: Noninvasive Monitoring[ AACN PROTOCOLS FOR PRACTICE: NONINVASIVE
Airini Arono
0 views

0:05
Download Telephone Triage Protocols for Adults 18 Years and Older (Telephone Triage Protocols
MarianRench
1 views

0:35
Best product Telephone Triage Protocols for Nurses (Briggs, Telephone Triage Protocols for
walker
1 views
![[Read] TCP/IP Illustrated, Volume 1: The Protocols: The Protocols v. 1 (Addison-Wesley](/image/s2.dmcdn.net/v/Pt3_y1e9_0lvZvH-V/xx720.pagespeed.ic.GE78wmqjuE.jpg)
0:33
[Read] TCP/IP Illustrated, Volume 1: The Protocols: The Protocols v. 1 (Addison-Wesley
phamza-elhaddars
7 views

0:36
TCP/IP Illustrated, Volume 1: The Protocols: Protocols v. 1 (APC) Review
yoheg
5 views

4:37
Adherence to Covid-19 Protocols: Clamp-down on persons violating protocols begins (10-8-21)
The Multimedia group
3 views

7:34
Security in Digital Image Processing:Importance of Digital Image Security: Module V,Lecture 5,EC703A
Dr. SANGITA ROY
28 views

0:05
Read Formal Correctness of Security Protocols (Information Security and Cryptography) Ebook
Kurtanidze 83
0 views
![[PDF] Operational Semantics and Verification of Security Protocols (Information Security and](/image/s1.dmcdn.net/v/FVG161e0X8s_TZyY4/x720)
0:07
[PDF] Operational Semantics and Verification of Security Protocols (Information Security and
SoletteHawkins
8 views

0:08
Read Formal Correctness of Security Protocols (Information Security and Cryptography) Ebook
Mlexer
1 views

0:06
Read Formal Correctness of Security Protocols (Information Security and Cryptography) Ebook
Hannawald
0 views

0:08
Read Operational Semantics and Verification of Security Protocols (Information Security and
Kstocker
0 views

0:24
Read Formal Correctness of Security Protocols (Information Security and Cryptography) Ebook Free
London Schwartz
2 views
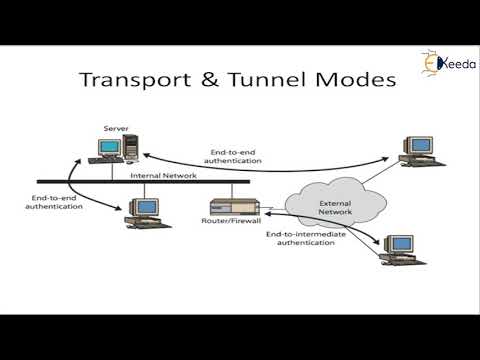
22:37
Internet Security Protocols IPSEC | Cryptography and System Security
Ekeeda
89 views

8:01
Web Security-Security Threats and their solution in hindi-Security Policy-computer network security
Unbeaten Learning
77.8K views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

5:06
Importance of Prime Numbers in Cryptography | Information Security Lectures Hindi
Easy Engineering Classes
4.6K views

0:21
Is Your Online Security at Risk. Exploring the Importance of Post Quantum Cryptography
Crypto Dypto
10 views

2:32
Event Security & The Importance Of Installation
susan
2 views

29:50
The importance of security
Faizan e Mohammad S.A.W.W
0 views

4:15
Know the importance of child's security
ABS-CBN News
1 views

1:24
Cameron stresses importance of enhancing UK security
ODN
784 views

0:44
The Importance of Home Security Cameras
judasmaxim
26 views

18:42
Cryptography And Network Security Importance of Subject in Hindi
SR COMPUTER EDUCATION
513 views

23:38
The Price Of Active Security In Cryptographic Protocols
Fidelity Center for Applied Technology (FCAT®)
31 views

14:39
The Ports and Protocols You Need for the Security+ SY0 701 Exam
Cyberkraft
67.2K views

11:19
USENIX Security '23 - Automated Analysis of Protocols that use Authenticated Encryption: How...
USENIX
148 views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views
11:30
Client Work (Coursework)COMP.SEC.220 Security Protocols & Functional Encryption| Tampere University
Europe Assignment Helper
4 views

3:40
How Do Encryption Protocols Work Within Cloud Security? | Cloud Stack Studio News
Cloud Stack Studio
0 views

0:29
How We Protect Your Crypto: Cold Storage & Security Protocols Explained
Caleb & Brown - Cryptocurrency Brokerage
563 views

4:47
Secure Protocols - CompTIA Security+ SY0-701 - 4.5
Professor Messer
71.1K views
13:37
SSL/TLS Protocols Explained: Security, Encryption & the Handshake Process
CodeLucky
35 views

8:38
IPsec Explained Simply: A Deep Dive into VPN Security Protocols (IKE, AH, ESP, Tunnel Modes)
LevelUP I.T.
43 views

13:57
HTTPS Security | SSL | TLS | Network Protocols | System Design
ByteMonk
28.7K views

1:56
Security Protocols (TLS), Public-Key Cryptography, X.509 & Certificate Issuance
Carizmian
496 views
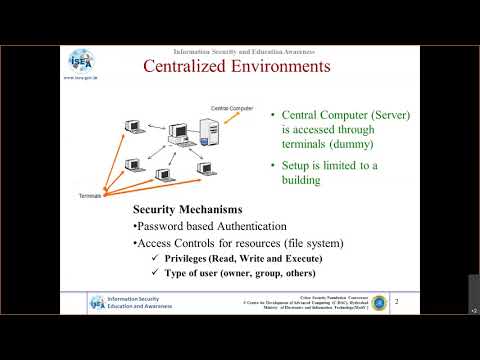
10:34
Cryptography and Network Security Protocols - Part 1
Information Security Awareness
87 views
21:55
USENIX Security '16 - The Cut-and-Choose Game and Its Application to Cryptographic Protocols
USENIX
186 views

1:58
PCI Requirement 4.1 – Use Strong Cryptography & Security Protocols to Safeguard Sensitive CHD
KirkpatrickPrice
1.3K views

7:48
IPsec vs. SSH vs. SSL/TLS | Network Security Protocols
Gate Smashers
68.2K views
24:31
Security Protocols: Lecture 2d (Asymmetric Encryption)
Antonis M
415 views

0:44
Crypto Investment: Evaluating Security Protocols for Profit
FINANCE-HACK25
87 views
41:18
Security Protocols: Lecture 2c (Symmetric Encryption)
Antonis M
557 views

17:04
UNIT IV-COMMUNICATION SECURITY,AUTHENTICATION PROTOCOLS
janadeep n
24 views
29:49
Security Protocols: Lecture 7b (Cryptographic Storage)
Antonis M
266 views