Search Results for "Network Access"
Find videos related to your search query. Browse through our collection of videos matching "Network Access". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Network Access"
50 results found

8:25
Cryptography and Network Security Unit 1- Part 5 | Network Security & Network Access Security Models
TN55 RLE
442 views

1:00
Pre launch access: unboxing PS5 Access Controller from Sony! #shorts
86hands
10.5M views

0:30
UniFi Access. Replacing old system with two Enterprise Access Hubs. #ubiquiti #accesscontrol
YesTechie
110.6K views

0:31
ESSL Js32 access control password programming system #essl #access #control
NF CCTV
3.8K views

1:27
You need Permission to access & request access
ABC of Knowledge, A family of Rahmat E Alam
163.6K views
0:41
you need access good drive | Goggle drive request access problem fix #googledrive #shorts
Basics About System
79.6K views

5:00
Access Control Security Explained | Types of Access Control Systems
Heimdal®
4.8K views

52:34
SA: SQL Server Encryption from Access by Susan Pyne. Q&A with Ben Clothier - Access with SQL Server
AccessUserGroups.org
778 views

7:39
Role-based access control (RBAC) vs. Attribute-based access control (ABAC)
IBM Technology
127.6K views

0:25
Access Control System Wiring Diagram | access control system installation
Electrical genius
148.2K views

8:12
Door access control system |How to install Access control system |Secureye B4CB installation /Wiring
Technical GuideWala
5.3K views

5:17
How To Install Access Control Access Door Lock How Configuration Multi Star Smart Door Lock
nature & future tech
203.5K views
![Microsoft Office Access 2010 Key Gen [microsoft office access 2010 tutorial pdf]](/image/s2.dmcdn.net/v/8zc0E1e98ooN1ZWKi/xx720.pagespeed.ic.1wyg8YbTNb.jpg)
1:20
Microsoft Office Access 2010 Key Gen [microsoft office access 2010 tutorial pdf]
Devin Dieujuste
88 views
![[PDF Download] MathXL Standalone Access Card (6-month access) [PDF] Full Ebook](/image/s1.dmcdn.net/v/DGgXd1cms4bnMfJHf/xx720.pagespeed.ic.J7vuwIHVdb.jpg)
0:05
[PDF Download] MathXL Standalone Access Card (6-month access) [PDF] Full Ebook
Gerloza241
11 views

0:08
PDF Access to Health Plus MasteringHealth with eText -- Access Card Package (13th Edition)
ConcettaCaffertyPamella
7 views
![[PDF] Access 2016 For Dummies (Access for Dummies) Popular Colection](/image/s2.dmcdn.net/v/HGztL1e9l53xLGn2J/xx720.pagespeed.ic.UNz-1LYwo5.jpg)
0:29
[PDF] Access 2016 For Dummies (Access for Dummies) Popular Colection
Heatherskoa
8 views

1:29
Biometric Access Systems-Q2 Fingerprint Access Control
ZakariasNordstrom
304 views

1:39:05
Vascular Access Demonstration - Femoral Access - By Dr.M.Srinivas Rao
TeluguOneTV
386 views

4:34
How To Use Microsoft Access - How To Use MS Access
accesstrainingdvd
4 views

5:19
Learn the Basics of Access Control in this Video: Access Control 101
Security Camera King
151.9K views

6:02
Network Security Model | Network security model in cryptography | Network Security
Chirag Bhalodia
22.5K views

14:06
CRYPTOGRAPHY AND NETWORK SECURITY NOTES | NETWORK SECURITY NOTES | NETWORK SECURITY
DIVVELA SRINIVASA RAO
382 views

45:59
01731, Network Steganography / Network Information Hiding, Chapter 7a Network-level Countermeasures)
Steffen Wendzel
812 views

23:56
What Is Network Security? | Introduction To Network Security | Network Security Tutorial|Simplilearn
Simplilearn
124.2K views

40:38
Cryptography in network (Network security basics) |Lecture 25| Data Communication & Computer Network
Mateen Yaqoob
58 views

1:55
Retina Network Security Scanner - Conficker Worm Serial - Retina Network Security Scanner - Conficker Wormretina network security scanner conficker worm (2015)
Jose Sanchez
2 views

6:33
What Is Network Marketing Network Marketing Explained! What Is Network Marketing Anyways
Most Popular Videos
1 views

11:37
What is Pi Network | Pi Network in Pakistan | Pi Network kya Hai | Pi Cryptocurrency Review in urdu
90s Mentor
25 views

7:54
Network Marketing Nedir, Neden Network Marketing, Network Marketing Gerçeği
musaduman
3 views

3:42
How Can I Protect My Network From Unauthorized Access and Data Breaches? | SecurityFirstCorp News
SecurityFirstCorp
16 views
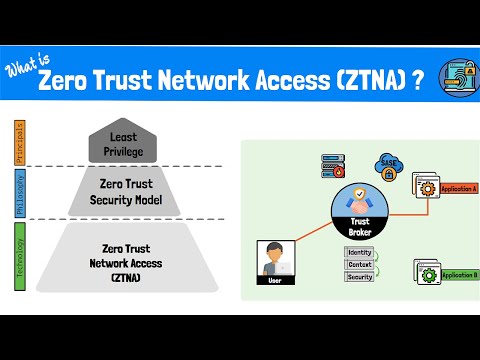
7:44
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
The CISO Perspective
164.3K views

0:25
Network Security Risks: Developer Access and Cyber Threats #shorts
Simply Cyber - Gerald Auger, PhD
1.7K views

2:10
How To Check For Unauthorized Network Access? - SecurityFirstCorp.com
SecurityFirstCorp
44 views
6:01
Understanding Network Access Control | CB3491 Cryptography and Cyber Security Unit 5 Anna University
CSE IT Exam Preparation
2.7K views

0:24
Read Now CompTIA Security+ Guide to Network Security Fundamentals (with CertBlaster Printed Access
Nigbau
0 views

0:39
Comptia Security+ Guide to Network Security Fundamentals (with Certblaster Printed Access Card)
dm_95d3a8a1d18d6c422de1845ecaa6e6b0
1 views

1:18
Private DNS server cannot be accessed problem fix | Mobile network has no internet access
Android Urdu
1.7K views
11:56
Access Control Principles - Network Security and Cryptography
Nadia Naureen J 23MIA1074
5 views

29:03
Critical Infrastructure Network Attacks: Code Red, Alert Network Operators
RSA Conference
551 views

5:38
Network Layer In Computer Network | OSI Model | Networking Layers | Computer Networks | Simplilearn
Simplilearn
38.0K views

20:58
Network Information Hiding, Chapter 4 (Fundamentals of Network-based Information Hiding)
Steffen Wendzel
276 views

43:15
cryptography and network security || cryptography and network security bangla tutorial.
Online_learning_tube
229 views

4:27
NAS vs SAN - Network Attached Storage vs Storage Area Network
PowerCert Animated Videos
2.0M views

38:05
Network Security Tutorial | Introduction to Network Security
CRAW SECURITY
1.1K views

8:36
Network Security Model| Model of Network Security | Information and Cyber Security
T N V S PRAVEEN
292 views

42:46
RSA Algorithm in Cryptography and Network Security - UGC NET PYQs | NETWORK SECURITY - RSA ALGORITHM
Unify Study
4.6K views

39:52
Network Security | What is a network and reference model? | Great Learning
Great Learning
4.4K views

6:53
Network security attacks in Hindi | Active attacks and Passive attacks in Network security in Hindi
QuickCS
1.2K views

12:05
What is Network Security? | Types of Network Attacks | How these Attacks are done
Tech Guru Manjit
14.6K views

13:06
Steganography | network Security in tamil,#sscomputerstudies,#steganography,#network,#security
SS Computer Studies
1.5K views