Search Results for "cbc padding attacks"
Find videos related to your search query. Browse through our collection of videos matching "cbc padding attacks". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "cbc padding attacks"
50 results found

0:31
WHEN CULTIST ATTACKS💀🔥 99Nights InThe Forest🌙 Animation #blockblast #99nightintheforest #99nights
Sarahlyn Arts
276.0K views

11:19
How to Avoid Password Attacks
Kirkham IronTech
61 views

32:54
Why are big UK cyber attacks on the rise? | BBC Newscast
BBC News
25.0K views

54:29
Charalampos Papamanthou: Leakage Abuse Attacks in Encrypted Databases
CMU Cylab Crypto Seminar
191 views

0:59
Top 3 Biggest Cyber Attacks In History | Cyber Security | Intellipaat
Intellipaat
10.6K views
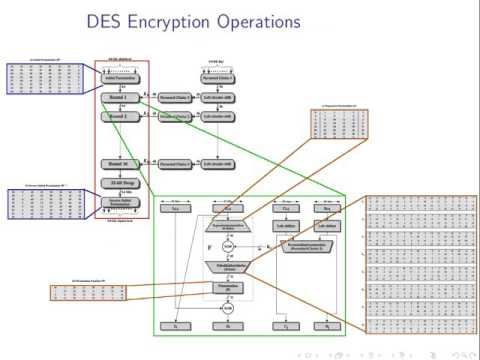
1:16:17
Symmetric Key Encryption and Brute Force Attacks (ITS335, L03, Y15)
Steven Gordon
2.7K views

51:33
Tales from the Crypt(analysis): A survey of side-channel attacks
UTD CSG
46 views

3:09
Megalodon attacks boat south africa
Ali H. Abbas
7.1M views
29:03
Critical Infrastructure Network Attacks: Code Red, Alert Network Operators
RSA Conference
551 views
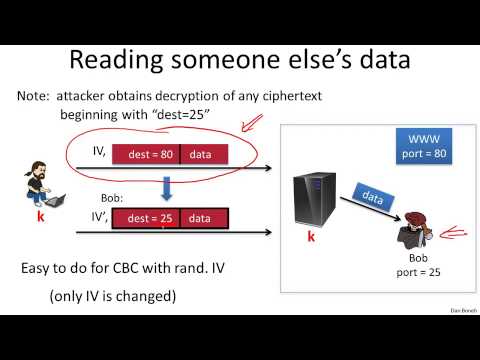
12:54
7 1 Active attacks on CPA secure encryption 13 min
Jake Danniel
305 views

3:32
Wireless Replay Attacks - CompTIA Security+ SY0-501 - 1.2
Professor Messer
148.3K views

6:05
What is Cryptography? Introduction and Types of Attacks
Algorithm Pod
361 views

7:24
Password Attacks: Social Engineering, Brute Force, Rainbow table
Cyberconnect
163 views
17:52
🚨 BREAKING NEWS: US Senators WARN of ATTACKS on the Homeland - Prepare NOW
Patrick Humphrey
21.7K views
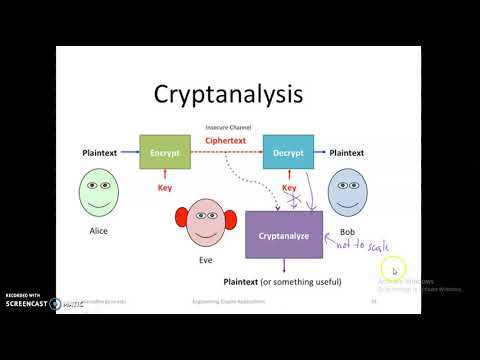
14:51
Cryptanalysis and its types of attacks, II M.Sc(CS),R.A.College For Women, Tiruvarur
Razool Begum
53 views
2:43
Lebanon’s Aoun calls for end to Israeli attacks in meeting with US envoy
Al Jazeera English
44.7K views

2:47
UK sanctions Russian spies accused of assassination attempts, cyber attacks and sabotage | BBC News
BBC News
109.5K views

8:37
CSS #9 Cryptanalytic attacks|Ciphertext only|Known Plaintext|Chosen Plaintext|Chosen Ciphertext|BTB
Be The Best
3.1K views

1:17:41
session-8: Cryptographic Attacks on Privacy
IACR
918 views

2:16:56
Craziest Lion Attacks Ever Caught On Camera #NatureDocumentary | Wild Animals
The Majestic - Animal Documentary
3.4K views

8:01
Multimedia - Cryptography - Product Ciphers - DES - Attacks - Arabic - Video 10
Alaa Abdelmohsen
141 views

0:15
Types of cyber attacks
AthulRaj
2.7K views

0:39
Godzilla Attacks Brawl Stars!!!
Brawl Stars
15.9M views
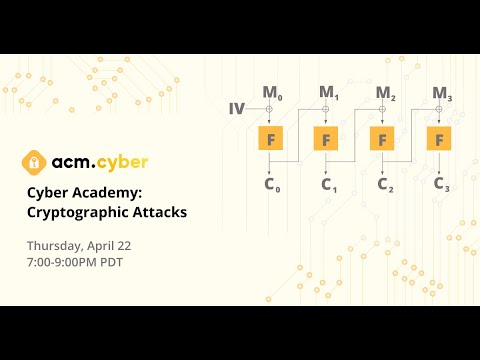
44:46
ACM Cyber | Cryptographic Attacks
ACM at UCLA
73 views

4:48
Aquaman and the Lost Kingdom (2023) - Black Manta Attacks Atlantis | Movieclips
Movieclips
268.9K views
2:14
Cryptanalysis | cryptanalysis in network security in hindi | cryptanalysis attacks | #mscoder
ms coder
7.0K views

6:34
Ukraine recording hundreds of cyber-attacks on critical infrastructure daily
Sky News Australia
1.0K views
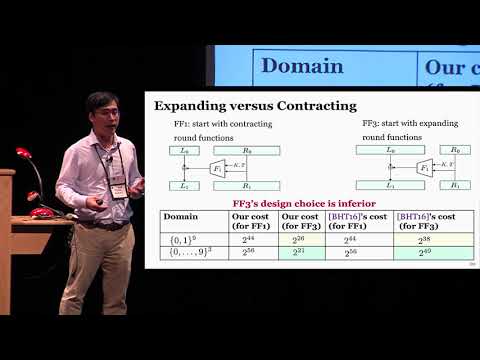
19:46
The Curse of Small Domains New Attacks on Format Preserving Encryption
IACR
370 views

3:46
An assessment of cryptographic protocols susceptible to quantum attacks
Aliro
63 views

1:22:16
16. Side-Channel Attacks
MIT OpenCourseWare
48.1K views

2:08
Japan deploys troops to northern mountains to tackle wave of deadly bear attacks
Al Jazeera English
124.4K views

2:11
Types of Password Attacks
Keeper Security
180 views

3:23
CISSP -60 Security Architecture and Engineering: Understand methods of cryptanalytic attacks
sumon infosec
128 views

47:07
Live sessions Sep 30 - session Quantum Algorithms, Attacks and Models (director's cut)
PQCrypto conference videos
130 views

3:35
Will the US Be Able to Withstand Cyber Attacks on Critical Infrastructure? | GZERO World
GZERO Media
1.5K views

1:03:37
Cryptography as a Network Security Tool in Hindi Urdu|Types of cryptography attacks LECTURE 10
Virtual Comsats
1.0K views
0:16
Types of Cyber-Attacks!!! #ccna #cybersecurity #networking #programming #techshorts #cryptocurrency
Networks Professionals
11 views

7:33
10 Most Common Cybersecurity Threats | Types of Cyber Attacks | Cybersecurity for Beginners |
E-Software Hub
4.2K views
0:52
Apple Reinforces iMessage Security Against Quantum Computer Attacks
Pick Digi
62 views

1:02
A look at Gaza City before and after October 7 ahead of 1st anniversary of Hamas attacks
AP Archive
105.8K views
13:45
COURSERA:INTRODUCTION TO CYBER SECURITY TOOLS AND CYBER ATTACKS | WEEK 3:KEY CONCEPTS| QUIZ ANSWERS
Anand Ranjit Kumar Mukkala
15.0K views
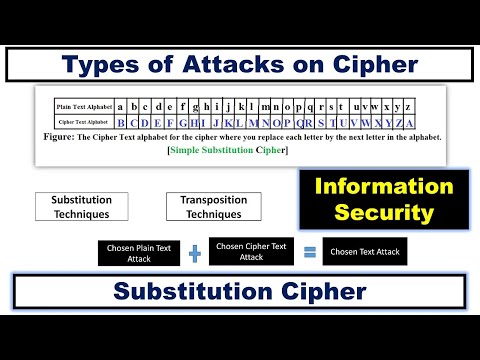
6:09
Types of Attacks on Cipher ~xRay Pixy
Ritika xRay Pixy
789 views

8:34
0317 Attacks on cryptography
Free Tech Courses
0 views

9:15
1.0: Security Goals and attacks- Cryptography and System Security
Ishita Lalan
12 views

1:33
UK accuses Russian military intelligence of global cyber attacks campaign
FRANCE 24 English
1.1K views
![Alfonso Muñoz - Stego attacks by design. A deep dive about stegomalware & ... [RootedCON2020-ES]](/image/i.ytimg.com/vi/5udFjDbSEaA/hqdefault.jpg)
1:02:26
Alfonso Muñoz - Stego attacks by design. A deep dive about stegomalware & ... [RootedCON2020-ES]
Rooted CON
844 views

28:41
USENIX Security '16 - Dancing on the Lip of the Volcano: Chosen Ciphertext Attacks on Apple iMessage
USENIX
186 views
3:04
Is Quantum Cryptography Vulnerable To Side-channel Attacks? - Quantum Tech Explained
Quantum Tech Explained
8 views

9:34
(CH7/2) Cryptography - Types of Cybersecurity Attacks Part 2
FENIXSOYA
30 views

55:57
Obvious in Hindsight From Side Channel Attacks to the Security Challenges Ahead
IACR
2.6K views