Search Results for "used to be"
Find videos related to your search query. Browse through our collection of videos matching "used to be". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "used to be"
51 results found

1:27
2013 Jeep Wrangler Sport Used Cars - Leavenworth,Kansas - 2013-08-09
TheKCcarguy
3 views

2:49
How Were Acronyms Used In Cryptography During War? - The Daily Definition
The Daily Definition
4 views
2:51
What Is Steganography And How Is It Used? - Emerging Tech Insider
Emerging Tech Insider
5 views

0:20
removing Cof from used LCD TV #lcd #soldering #cof #tv #television #repair
Jupri S Elektronik
299.2K views

1:00
If Disney characters used THE TREADMILL #shorts 🏰😅
Kurt Tocci
41.0M views
13:47
Is Afghan soil being used against Pakistan? - How many ter*orists came from Afghanistan? - Geo News
Geo News
3.0K views
6:14
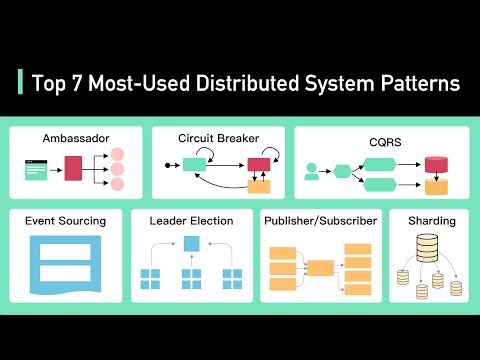
Top 7 Most-Used Distributed System Patterns
ByteByteGo
320.6K views
44:39
DEF CON 22 - Steganography in Commonly Used HF Radio Protocols
SecurityRelated
493 views

0:42
Top 3 tricks used to hack your password that hackers don’t want you to know about
Cybersecurity Girl
53.0K views

13:57
The Used Car Market Has Lost Its Mind (in 2025)
Ideal
24.8K views

0:36
Why Kali Linux Is Used For Hacking ? | Kali Linux For Ethical Hackers #Shorts #Simplilearn
Simplilearn
495.3K views
4:38
How Is Steganography Used With Audio Files? - SecurityFirstCorp.com
SecurityFirstCorp
57 views

3:38
How Is Steganography Used With Text? - SecurityFirstCorp.com
SecurityFirstCorp
18 views
11:58
CAR MARKET UPDATE for New & Used Vehicles (October 2025)
CarEdge
81.4K views

1:35
Hand Sanitizer Used by Teens To Get Drunk: Dangerous Teen Trends
ABC News
342.1K views

2:46
What Are Ciphers And How Were They Used During WWII? - Inside Museum Walls
InsideMuseumWalls
18 views

0:30
This Looks Like Gibberish… But It’s Not 👀 Caesar Used This to Send Messages
Dot by Dot
95 views

3:24
How Are Hashing Algorithms Used In Blockchain? - CryptoBasics360.com
CryptoBasics360
6 views

0:22
How to send photos through WhatsApp web | Dell Inspiron laptop used #5minutestech #WhatsApp #photos
5-Minutes Tech
54.6K views

0:15
Used Maruti Suzuki Swift car for sale
Faizal's View
20.3K views

0:41
9 Sniper rifles used by Indian Forces | NSG | SPG | Special Forces
Agniveer India
3.1M views
24:58
10TOOLS AND METHODS USED TO PERFORM CYBERCRIME
SimpliPy
16 views

2:55
Is Cryptographic Obfuscation Used For Security? - CryptoBasics360.com
CryptoBasics360
7 views

0:23
These didn’t used to be on my packages……just sayin. #80smusic #surveillancetech #control
Marty Real Estate & Photography
1.4K views

3:25
How Is Steganography Used In Data Security? - SecurityFirstCorp.com
SecurityFirstCorp
5 views

2:11
What Is Cryptology? | Where Is Cryptology Used?
All in All Sheela
44 views
0:44
A global key was used multiple times inside one widgets child list
dbestech
11.3K views

8:15
What is Cryptography? why it used? objectives of Cryptography and Types of Cryptography
InforMation TechnoLogY
172 views

4:26
What Are The Different Types Of Quantum Entanglement Used For Cryptography? - SecurityFirstCorp.com
SecurityFirstCorp
4 views

1:00:25
What kind of cryptography is used in Bitcoin cryptowallets | Vadym Hrusha
Cyber Academy Global
32 views

2:42
Where Is Steganography Used? - Tactical Warfare Experts
Tactical Warfare Experts
0 views
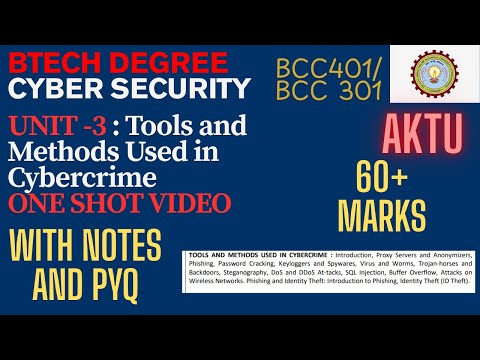
39:33
Unit 3 | Cyber Security AKTU | Tools & Methods Used in Cybercrime | One Shot with Notes & PYQs
Factify learning
224 views

2:40
Computer Science for Everyone - 35 - What are algorithms used for?
teclado
4.9K views

14:44
Which Calculus Textbooks Are Used At City Tutoring?
citytutoringmath
12.3K views

4:18
Taliban crisis: Our focus is that Afghan soil should not be used for terrorist activities, says MEA
The Economic Times
666 views

12:46
What is Cryptography? Why is it used? What is its value in real life? Part-1
CICTIT Sansthan
0 views

12:55
Car Market Update For New & Used Vehicles | Watch Before Buying | Summer 2025
CarEdge
131.5K views

56:46
How Cryptography is used in IT Security - Explained
it learning
19 views

3:15
What Are The Common Code-breaking Techniques Used Against The Caesar Cipher?
Tactical Warfare Experts
20 views

3:38
BDS AUTOMOTIVE USED VAN SALES WIGAN - COMMERCIAL VEHICLE DEALER FORD TRANSIT MK7 GREATER MANCHESTER
BDS AUTOMOTIVE
166 views
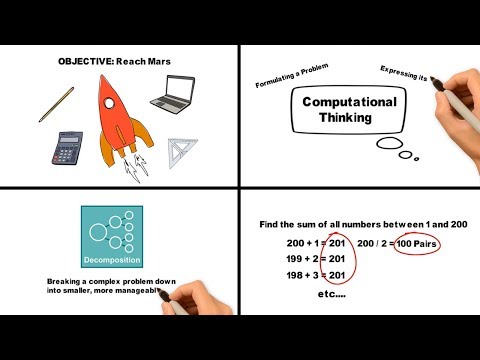
5:42
Computational Thinking: What Is It? How Is It Used?
College & Career Ready Labs │ Paxton Patterson
378.7K views

0:20
At first I was just used as an outlet and in the end I was truly loved #cdrama #kdrama #chinesdrama
Danoratv drama
4.4M views

3:08
How Is Steganography Used In Anti-forensics? - SecurityFirstCorp.com
SecurityFirstCorp
15 views

0:09
Top 7 Most Used Data Science Tools 🔥🔥🔥 #Shorts #DataScience #Simplilearn #YTShorts
Simplilearn
3.1K views

0:06
💰 He Used His Mother’s Birthday… And Won ₹240 CRORE Lottery in UAE! 😱❤️ | Real Life Miracle#shorts
Instant Facts by Nur
19.0K views

4:00
Are Post-Quantum Cryptography Methods Used by Crypto Exchanges Yet? - All About Crypto Exchanges
All About Crypto Exchanges
2 views

0:54
Reality of Luxury Used Cars !! #luxurycars #highstreetcars #luxurybyharnoor #usedcar #secondhandcars
luxurybyharnoor
568.2K views

0:27
They Used Their Fingers to Learn THIS! 🧠✋ #quiz #millionaire #education #retro #korea #math #tv
THINK & PLAY
24.2K views

0:35
Top 3 Secret Codes That Were ACTUALLY Used
Extreme Ariz
3.9K views
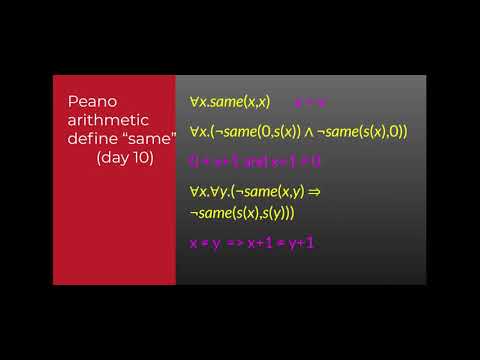
4:43
Herbrand logic used to define Peano arithmetic
Chris Kuszmaul
167 views
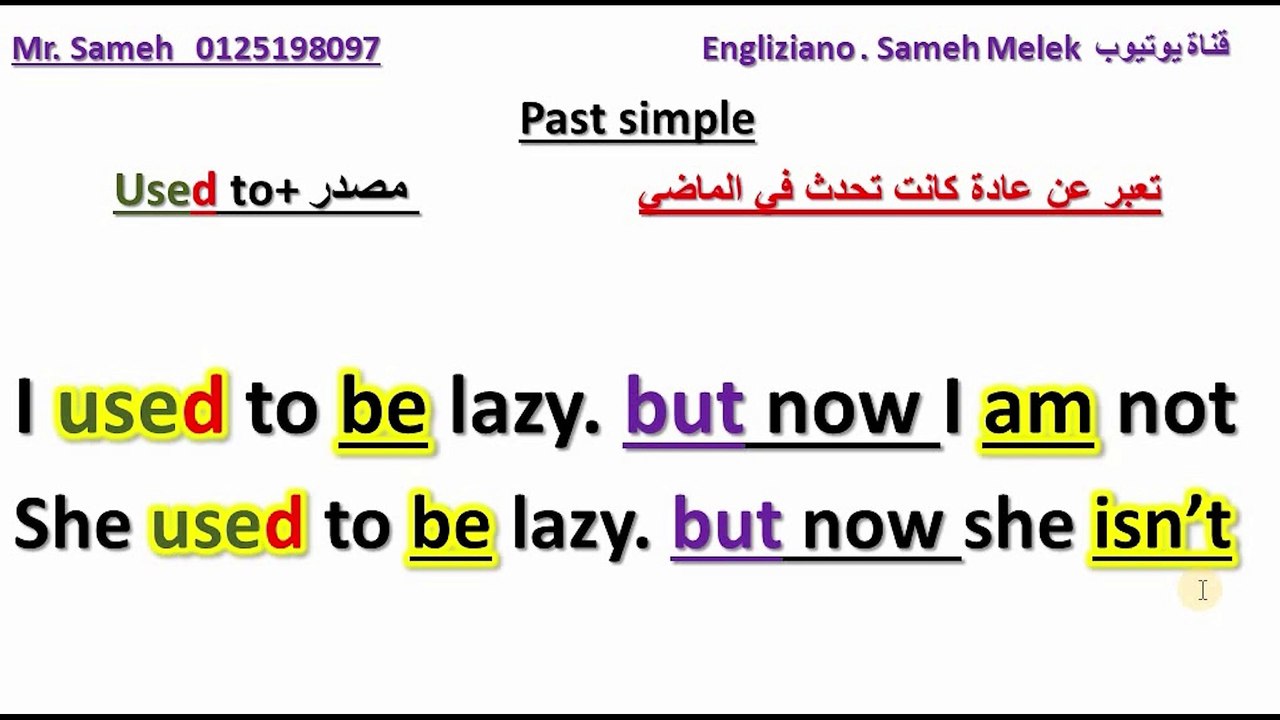
4:37
شرح الفرق بين Used to | Be (am- is -are) used to | Get used to - would في اللغه الانجليزيه بسهولة
Engliziano
388 views