Search Results for "algorithm upgrades"
Find videos related to your search query. Browse through our collection of videos matching "algorithm upgrades". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "algorithm upgrades"
50 results found
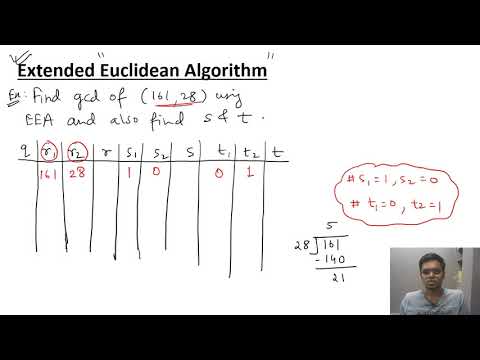
7:40
Extended Euclidean Algorithm - Example (Simplified)
Shrenik Jain
169.1K views

28:17
Parte 1 - Introdução ao Algoritmo SHA 256 - Secure Hash Algorithm SHA256
Laboratório de Inutilidade Pública
7.2K views

3:07
RSA Algorithm Explained — Public & Private Key Encryption Made Simple
Dr. Eman Daraghmi
23 views
14:43
Cryptography in Python using RSA Algorithm
Code With Nabeel
298 views

0:38
Shamir's Secret Sharing The 1979 Algorithm Securing Your Crypto in 2025
Cypherock
395 views
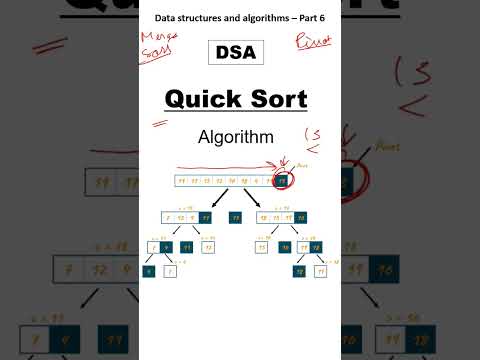
1:01
Quick Sort Algorithm in any language. #datastructuresandalgorithms
Codejob Roadmap
91.4K views

0:14
The RSA algorithm is the secret handshake of the internet
The Code Bit
44 views

25:12
Elliptic Curve Scalar Multiplication: The Double-and-Add Algorithm Explained
Network Technician
2 views

2:49
AUDIO STEGANOGRAPHY USING RSA ALGORITHM AND GENETIC BASED SUBSTITUTION METHOD TO ENHANCE SECURITY
VERILOG COURSE TEAM
909 views

9:08
L-5.1: Introduction to Dynamic Programming | Greedy Vs Dynamic Programming | Algorithm(DAA)
Gate Smashers
953.6K views

32:13
Introduction to RSA Algorithm
Kifayat Ullah
279 views
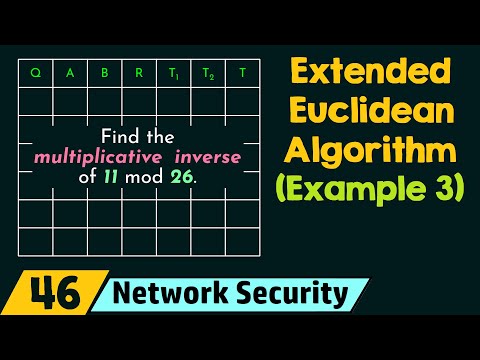
6:54
Extended Euclidean Algorithm (Solved Example 3)
Neso Academy
94.3K views

0:20
IMAGE ENCRYPTION AND DECRYPTION USING AES ALGORITHM WITH DATA HIDING
Matlab Source Code
29 views

29:50
Theory of Computation Lecture 39: Turing Machines (2): The Definition of Algorithm
Ghassan Shobaki Computer Science Lectures
1.1K views

10:32
IDEA algorithm in cryptography and network security
Lab Mug
4.7K views

9:18
Extended Euclid Algorithm - Number Theory Advanced | C++ Placement Course | Lecture 37.1
Apna College
36.4K views

12:58
RSA Algorithm with Example | Asymmetric Key Cryptography (Public Key Cryptography)
Simple Snippets
26.4K views
10:58
Introduction to Computation Theory: What is an algorithm
Complexity Explorer
5.8K views

13:47
Formal Concept Analysis - Week 3, 2-04 - The complexity of the algorithm
arisbe, 𝑎 𝑔𝑢𝑒𝑠𝑠 𝑎𝑡 𝑡ℎ𝑒 𝑟𝑖𝑑𝑑𝑙𝑒
134 views
2:11
Computer Science: What is the fastest addition algorithm on a turing machine?
Roel Van de Paar
8 views
1:01
Traveling Salesman: Expert Drivers vs. Algorithm Control
MLs like teen spirit
3 views

8:52
The theory of algorithm complexity
Muhammad_Alfarisyi_Raska_Ramadani Mahasiswa
11 views

12:02
Algorithm to Delete Element from Queue or Circular Queue | Data Structure
Ankit Verma
3.5K views

0:47
Prim's Algorithm for Creating a Minimum Spanning Tree (MST) - Min Cost to Connect Points (LC 1584)
Greg Hogg
38.7K views

16:44
Model of computation | Analyzing an algorithm | Data Structure & Algorithms | Appliedcourse
GATE Applied Course
29.2K views

0:53
Travelling Salesman problem #cseguru #shorts #shorts_video #shortsfeed #algorithm #cseguruadavideos
CSE Guru
15.5K views

0:20
IMAGE ENCRYPTION AND DECRYPTION USING AES ALGORITHM WITH DATA HIDING
MATLAB ASSIGNMENTS AND PROJECTS
83 views

7:07
Knapsack algorithm | Cryptography and System Security
Ekeeda
326 views

28:53
Master the Pelican Optimization Algorithm: A Complete Step-by-Step Guide
Mrinmoy Majumder
10 views

2:08
Java Hashing Explained! #java #coding #programming #software #hashing #algorithm #encryption #data
Michael Olech Coding
664 views

1:03:20
Basic Maths for DSA | Euclidean Algorithm | Strivers A2Z DSA Course
take U forward
1.5M views

0:21
TikTok Algorithm 2025: Hack the FYP in 3 Seconds!
Yann Bakebongo | Ai Automation For Businesses
5.8K views

8:48
Prim's Algorithm Visually Explained (Minimum Spanning Tree)
Hello Byte
2.6K views

17:48
Lec 17: Preemptive Priority Scheduling Algorithm in OS with example | Operating System
Jenny's Lectures CS IT
548.3K views

8:07
Matlab Image Processing Projects - IMAGE ENCRYPTION USING PARALLEL RSA ALGORITHM - ClickMyProject
ClickMyProject
361 views

13:10
Logistic Regression Algorithm in Machine Learning with Solved Numerical Example by Mahesh Huddar
Mahesh Huddar
172.7K views
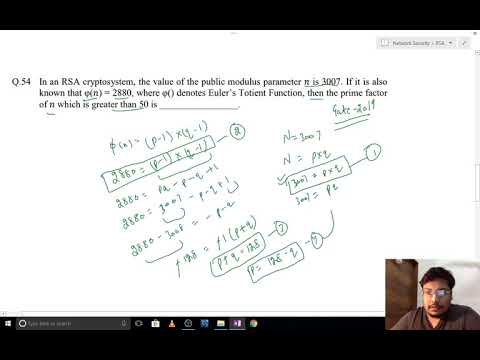
6:14
RSA Algorithm || GATE-2019 Solution.
CS Factory
141 views
11:56
LSB algorithm|| Steganography|| in Tamil
Amala_vlogs
2.5K views

32:14
Data Encryption Standard Algorithm || Bit Level Encryption || Private Key Cryptography.
CS Factory
25 views

14:46
Lets Algorithm P #P #NP #NPComplete NP Complete #NPHard NP Hard Problem Non-Deterministic Polynomial
Ahmed N. Elghannam
38.2K views

41:24
Discrete Mathematical Structures, Lecture 3.7: The Euclidean algorithm
Professor Macauley
1.5K views

2:17
A Lightweight Image Encryption Algorithm Based on Secure Key Generation
Takeoff Edu Group
229 views

10:41
Euclidean Algorithm- gcd(21029,12597)
Prime Newtons
3.4K views

21:37
Diffie-Hellman Key exchange Algorithm | Lecture | Cryptanalysis | Cryptography
Cybersecurity Mechanic
592 views

18:01
RSA Algorithm || Rivest, Shamir, Adleman Algo. Basics. || Public Key Cryptography.
CS Factory
29 views

10:38
RSA Algorithm in Cryptography-Full with Examples
DesignerXCoder
209 views

32:44
Cryptography & Security - Hill Cipher Algorithm
Vaishali Yadav
92 views
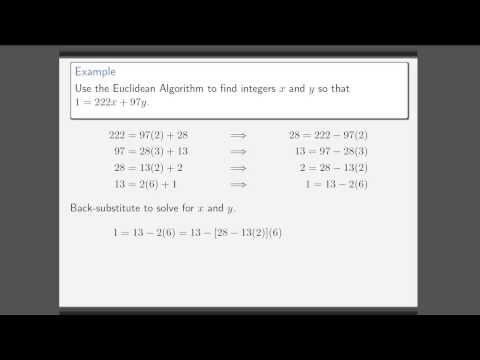
2:42
Extended Euclidean Algorithm
Math Dad (Serge Ballif)
45.1K views

23:04
11-Learn RSA Algorithm Step-by-Step 💡 | Public Key Encryption in Network Security
Sundeep Saradhi Kanthety
319.5K views

16:47
#Blowfish BLOWFISH ALGORITHM In Cryptography | Round Function | Key Expansion #Jntuh #cns #feed
Concept Clear
749 views