Search Results for "sending information securely"
Find videos related to your search query. Browse through our collection of videos matching "sending information securely". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "sending information securely"
50 results found

0:21
What is Information Technology
3Scode
899 views

0:31
Unlocking the Secrets of Cryptography: How Algorithms Keep Your Information Safe
BillionaireMotivation
41 views

1:58
Justin Holmgren, Research Scientist, Cryptography & Information Security Lab
NTT Research
134 views

5:16
Fighting an Information War, Israel Hosts Christian Media Summit
CBN News
6.9K views

11:47
Information Security: Context and Introduction || Coursera || The Complete Solution
saisoluz
2.3K views

1:41
Cybersecurity Shorts for Executives: The New Chief Information Security Officer
George Mason University Television
210 views

0:47
Saif ko bahar se information mil rahi hai? 😱 - #OvaisRiaz | #AyazSamoo | #ARYPodcast
ARY Podcast
136.1K views

10:21
Caesar Cipher Encryption and Decryption in Hindi | Information Security
Hamza Learning
987 views

0:59
Who was Charles Babbage? Interesting information
Misha.Prayu. Show
304 views

16:06
Substitution Techniques | Caesar Cipher | Monoalphabetic Cipher | Part 1 | Information Security
eVeda
79 views

1:10:02
Single Systems | Understanding Quantum Information & Computation | Lesson 01
Qiskit
271.7K views

1:00:52
Quantum Circuits | Understanding Quantum Information & Computation | Lesson 03
Qiskit
77.5K views
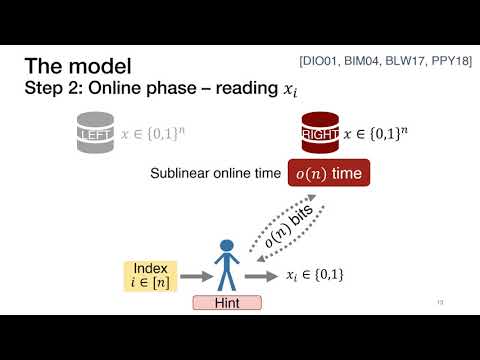
21:18
Private Information Retrieval with Sublinear Online Time
IACR
2.0K views

0:45
Symmetric and Asymmetric Cryptography|CC-413|Information Security|@PU-shift-swift
PU-Shift-Swift
6 views

4:46
Asymmetric Information, Adverse Selection & Moral Hazard | Economics Explained
INOMICS
117.2K views

4:31
Steganography of Binary Information in Image Using Deep Learning Method
IBIMA Media
80 views

8:51
Hill Cipher Decryption in 5 steps Example in hindi | Information and Network Security Course | GTU
AXL huB
200 views
![What is Python With Full Information? – [Hindi] – Quick Support](/image/i.ytimg.com/vi/3dy_PYF9xOI/hqdefault.jpg)
8:56
What is Python With Full Information? – [Hindi] – Quick Support
Quick Support
2.1M views
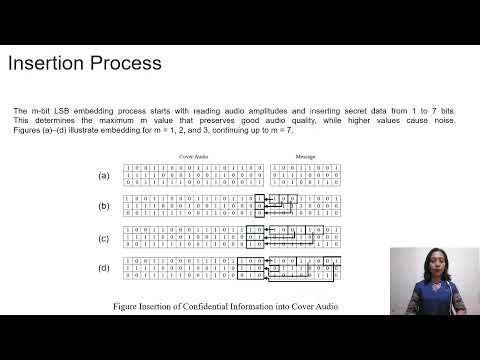
8:54
Comparison of the Use of M-Bit LSB Steganography Methods on MAV Files in Information Storage
imelda duma
20 views

3:28
Charles Babbage || Father of Computer || Information || P S Computer
P S Computer Center
6.6K views

18:38
Information and Network Security , Module 1, Introduction
GNS S
173 views

6:37
Quantum information and quantum cryptography
Science Technology And Engineering
4 views
2:12
Android Based Image Steganography System | Information Security Projects Ideas
Nevon Projects
7.6K views

2:16:24
Information Security Oversight Office Training Seminar
US National Archives
617 views

0:33
Image Hide text file information#education#informationsecurity #img#hacker#hack#command#datasecurity
Cyber Neta IT
33 views

0:21
Reality of Scholarship in Italy.Watch full video get the information #internationalstudents #italy
Indian in Europe
219.6K views

0:38
Binwalk Image forensic extract information from image #cybersecurity #imageforensic #binwalk #exif
Zodiac
8.1K views

9:51
Computer Science vs. Information Technology | Which Career & Degree Should You Pursue?
GRC For Mere Mortals
34.5K views

8:36
Network Security Model| Model of Network Security | Information and Cyber Security
T N V S PRAVEEN
292 views

1:19:25
Russian Information Warfare Threats
CSNP
271 views

7:04
Information Technology in 5 mins | What is IT
Explore with Epaphra
87.5K views
25:12
Steganography, cryptography and information hiding
proQA
125 views
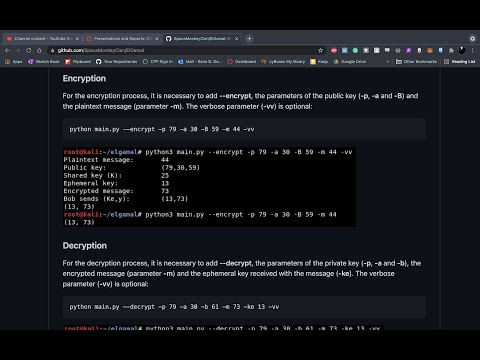
25:25
Cryptography and Information Security - ElGamal Cryptosystem and Variants
Rene Dena
211 views
4:12
Steganography:Hide Information Behind Any File
VHackTech
45 views
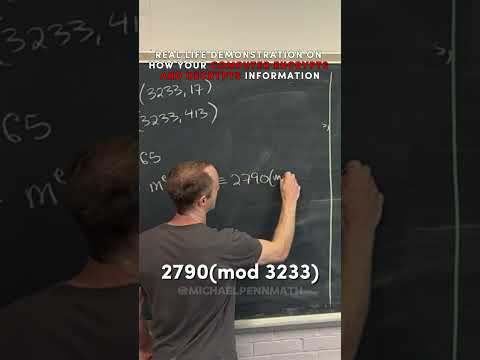
2:11
how your computer sends encrypted information
Michael Penn
3.5K views
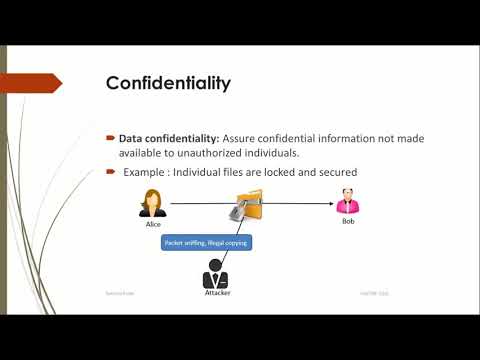
5:00
INS: Unit-1 Introduction to Information and Network Security
Twinkal Patel
729 views

3:40
What is Cryptography? | Explain Cryptography | How Cryptography Works? | Cryptography Information
Crypto & Blockchain News (CBN)
4 views

14:09
Information Security Measures (Authentication, Digital Signature, Firewalls, Steganography)
5-Minute Lessons by Victor
973 views

26:08
Information Security : Blowfish
Techbytes CSE
48 views

22:03
Introduction to Information Technology
Elimika Mtandaoni
185.3K views

5:37
How to store hidden information in Kali Linux using Steghide| Steganography| Cybersecurity
Revathy Mohan Kannara
61 views

0:22
symmetric key cryptography क्या है || Useful Information🔥 #technology #networksecurity #shortsvideo
VL Facts
385 views

8:32
Steganography: Hiding Information in Plain Sight
Akshaya G K
10 views

3:11
How to FIX PS4 Error Code WC-34891-5 (Credit card information is invalid)
YourSixStudios
3.8K views

1:00
Cybersecurity Chronicles: The Pioneering Women of Information Security
Raleigh Guevarra
122 views

41:47
Network Information Hiding, Chapter 1 (Introduction to Steganography and Covert Channels)
Steffen Wendzel
1.7K views

14:08
Attacks-Malicious Code-Brute Force(KTU CS 472 Principles of Information Security-S8CS-Mod 1 Part 6)
KTU Computer Science Tutorials
1.3K views

0:44
Cryptography and information security: encryption algorithms and methods for ensuring data security.
Superpupt
75 views

26:46
Code-based cryptography V - Information-set decoding
Tanja Lange: Post-quantum cryptography
1.9K views

14:27
What is Information Technology?
Tech Gee
5.9K views