Search Results for "polyalphabetic substitution technique"
Find videos related to your search query. Browse through our collection of videos matching "polyalphabetic substitution technique". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "polyalphabetic substitution technique"
51 results found

15:14
BEHAVIOURAL Interview Questions & Answers! (The STAR Technique for Behavioral Interview Questions!)
CareerVidz
663.7K views

10:53
PART 4 | HASH FUNCTION ATHENTICATION TECHNIQUE IN CRYPTOGRAPHY & NETWORK SECURITY (BANGLA)
COMPUTER SCIENCE WITH BHASKAR SIR
229 views

11:08
5 STAR Interview Questions and ANSWERS! How To Use The STAR Technique!
CareerVidz
87.8K views
2:25:42
Cryptography in network& computer security |Cryptography Encryption Technique| chapter three #በአማርኛ
Universal-tube
6.2K views

10:57
Additive Shift Ceaser Cipher Technique || Lesson 5 || Cryptography || Learning Monkey ||
Wisdomers - Computer Science and Engineering
435 views
4:55
A new image encryption technique combining Elliptic Curve Cryptosystem with Hill cipher in Matlab
OKOKPROJECTS
204 views

12:06
TRANSPOSITION TECHNIQUES || RAIL FENCE TECHNIQUE || COLUMNAR TRANSPOSITION -- NETWORK SECURITY
t v nagaraju Technical
11.8K views
16:50
The Caesar Cipher: A Simple Yet Powerful Cryptographic Technique
Harshit Jain
78 views

0:39
Amazing Fishing Technique In River Big Monster Fish Video#fish#video
Attractive Fish Content
41.5M views

43:20
Encryption Techniques From Traditional To Modern Encryption Technique - Devconf2025
DevConf
61 views

0:14
Collar grab self defence technique #fighttechniques #martialarts #boxing
Kishor Joshi self defence and fitness.
7.5M views

8:38
This Hybrid Shot Technique Is SO Effective Especially for Older Golfers
The Art of Simple Golf
670.9K views
10:19
BATCH CRYPTOGRAPHIC TECHNIQUE TO DISCOVER INVALID SIGNATURES IN ADVERSARIAL NETWORKS
SOWMIYA SRINIVASAN
99 views

0:48
Caesar Cipher Explained: Oldest Encryption Technique! 🔐L#shorts #cybersecurity
Tech With Vyshali
961 views

11:56
Multilevel Data Concealing Technique Using Steganography and Visual Cryptography MTECH PROJECTS
TRU PROJECTS
96 views
7:52
A New Fuzzy DNA Image Encryption and Steganography Technique
XOOM PROJECTS
8 views

4:51
Hill Cipher Technique | Encryption process | Cryptography | @Alfiya12
Let IT be easy
191 views

3:00
Steganography - A technique To Hide Your Message Behind Image #Tutorial
Hackers Online Club
663 views

8:09
Every Espionage Technique Explained in 8 Minutes
The Paint Explainer
284.0K views

0:08
The best feeling ever!!🙌🏼 #pov #dance #dancer #dancelife #dancers #dancemoms #technique #real
Raina Elegado
3.7M views

16:14
STAR TECHNIQUE Interview Questions and Answers
Amri Celeste - Interview Coach
157.0K views
![When someone slap you [self-defense technique against slap] #selfdefense #kravmaga #youtube](/image/i.ytimg.com/vi/8uwTH-D_t8c/hqdefault.jpg)
0:18
When someone slap you [self-defense technique against slap] #selfdefense #kravmaga #youtube
NJ clan
7.6M views

11:14
Difference Array Technique | Tutorial | Range Updates | Competitive Programming Tricks Part 1
TLE Eliminators - by Priyansh
48.1K views

1:00
CIA’s Secret Spy Shoe Technique!
Dhruv Rathee Shorts
1.7M views
6:26
Caesar cipher encryption/decryption technique
Sameh Reda
97 views
0:46
Image Steganography using the LSB (Least Significant Bit) technique!
Atanu
97 views

4:07
2.12 Rail Fence Technique
EngiNerd
59 views
1:20
UN BITCOIN À $330,000 D'APRÈS CET INDICATEUR TECHNIQUE ! 😱 #crypto #bitcoin #btc #bullrun
Crypto Le Trone
13.0K views
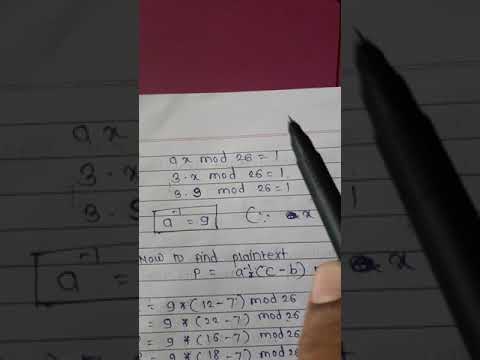
9:49
Affine Cipher Encryption Technique with Example
sofiya mujawar
54.2K views

5:53
STAR Technique for Answering Interview Questions
Afzal Hussein
10.3K views

12:44
Cryptographic Technique(BCA, MCA)
Guru Kpo
382 views

1:08
A former member of the KGB explains the most valuable technique for espionage
Business Insider
213.2K views

11:33
Trent’s Technique 🤩 Mainoo's Curler, CLINICAL Palmer & Stones' WORLDIE | Inside Training | England
England
518.9K views
28:25
Project Name: Hidden Secret Message using Steganography Technique (LSB)
ezaini-ismail
216 views
0:06
In Den of Thieves (2018), Pablo Schreiber demonstrates flawless firing technique with the M240B
andyy
16.8M views
13:41
How To Solve LeetCode (as a Beginner) And Learn DSA in 2024 *Proven Technique*
The Code Skool
213.4K views

0:54
Charles Leclerc est le seul à utiliser cet technique de pilotage en formule 1 #f1 #charlesleclerc
Alan On Track
662.1K views
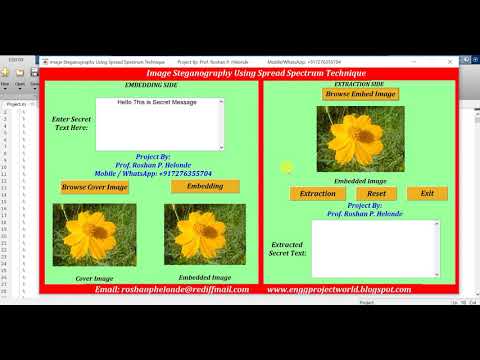
1:04
Matlab Code for Image Steganography Using Spread Spectrum Technique | IEEE Based Project
Roshan Helonde
1.2K views

12:45
NTA UGC NET Previous Year Question Papers || Columnar Transposition Technique with Example in Hindi
CoverWorld99
292 views
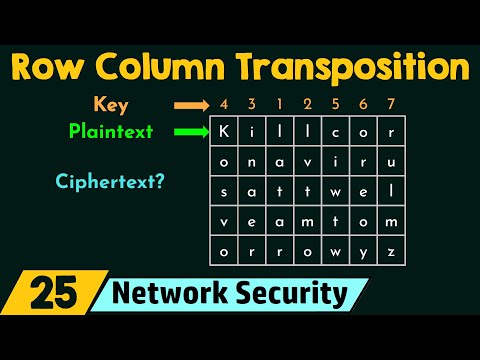
8:15
Row Column Transposition Ciphering Technique
Neso Academy
387.9K views
11:40
How to hide data/file/folder inside a image(Steganography technique)
Ajinkya Ranaware
1.8K views
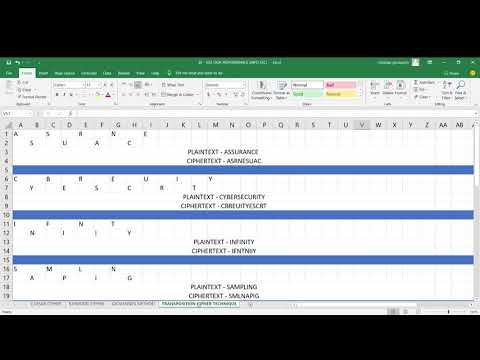
1:58
Giovanni's Method and Transposition Cipher Technique BT-502 TP
christian geolagon
2.1K views

10:52
VERNAM CIPHER ENCRYPTION and decryption TECHNIQUE explanation with examples in telugy
PBRAO
479 views
![caesar Cipher technique [HINDI]](/image/i.ytimg.com/vi/cZUQkkdfUdc/hqdefault.jpg)
6:35
caesar Cipher technique [HINDI]
Knowledge Radar
11.0K views

1:58
Rail Fence Cipher Example - Transposition Technique ~xRay Pixy
Ritika xRay Pixy
682 views
10:08
Hackers Use This Technique to Hide Files in Plain Sight - Steganography
Pen Ace
4.8K views

16:55
Combat technique Boucher Ketchup Vs Badou Zaki au Canada 🇨🇦
Lutte TV
395.2K views

8:23
Vernam Cipher method | One time pad | Cryptography technique | @Alfiya12
Let IT be easy
285 views

18:46
Combat très technique entre Abdallah Diallo et Cheikh Ahmed Tidiane Diop au stade Amadou Barry…
Eric Favre TV
1.2K views
6:09
AES ALGORITHM BASED SECURE DISCRETE WAVELET TRANSFORM STEGANOGRAPHIC TECHNIQUE FOR THE IMAGES
VERILOG COURSE TEAM
739 views

1:05
Substitution - Bring Her Back Teaser VF
Allociné
2.9K views