Search Results for "digital forensics roadmap"
Find videos related to your search query. Browse through our collection of videos matching "digital forensics roadmap". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "digital forensics roadmap"
52 results found
18:28
Cyber Forensics Tutorial | Exiftool Tutorial | Invisible Secrets 4 | What is Steganography
FORnSEC Solutions
941 views

0:55
What is computer forensics? || cyber law || part 1 || part 2 is in description box
Amisha Sharma
1.2K views
9:19
Cyber Hui Forensics Training - Lab One (Steganography)
HawaiiCyberHui
547 views
6:10
How to view hidden picture metadata in a computer forensics case
Tech Pub
6.9K views
10:54
BlueHens UDCTF 2022 Writeup | Forensics | Audio Salad
HxN0n3
5.1K views

3:08
How Is Steganography Used In Anti-forensics? - SecurityFirstCorp.com
SecurityFirstCorp
15 views
12:30
CTF - Image Forensics 101
GuyInTheShell
13.9K views
![Steg Ultimate [Forensics Challenge] | Author: StephenCurry396 | Cyber Yoddha CTF](/image/i.ytimg.com/vi/Rzr2GvmZU9I/hqdefault.jpg)
3:20
Steg Ultimate [Forensics Challenge] | Author: StephenCurry396 | Cyber Yoddha CTF
106_Sam
179 views

39:54
The Use of Steganography and Steganalysis Trends in Computer Forensics
CAE in Cybersecurity Community
219 views
2:31
What Is Steganography In Image Forensics? - SecurityFirstCorp.com
SecurityFirstCorp
15 views
2:50
CTFLearn Forensics 101
Alex Checchi
965 views

1:08
how to detect steganography files in windows stegdetect computer forensics
Aravind Ch
4.2K views

25:56
8 Best Forensics Tools In Kali Linux | Deleted Data Recovery | Ethical Hacking | FREE Tutorial
The Novice Learner
385 views
2:00
Iberia Parish crime lab enhances forensics with new DNA tech
KLFY News 10
40 views

0:05
Read Cyber Security Cyber Crime and Cyber Forensics: Applications and Perspectives Ebook Free
Reimold
3 views

0:07
Read Computational Forensics: Third International Workshop IWCF 2009 The Hague The Netherlands
Abicht
0 views

0:08
Read Cyber Security Cyber Crime and Cyber Forensics: Applications and Perspectives PDF Online
Myrthenbaum
2 views

0:08
Read Learning Python for Forensics PDF Online
Bgerstner
5 views

0:06
Read Introduction to Security and Network Forensics Ebook Free
Maisi Baker
0 views

0:08
Download Android Forensics: Investigation Analysis and Mobile Security for Google Android PDF
Sladouph
1 views

0:17
Free Online Forensics Courses
NN IT
7 views
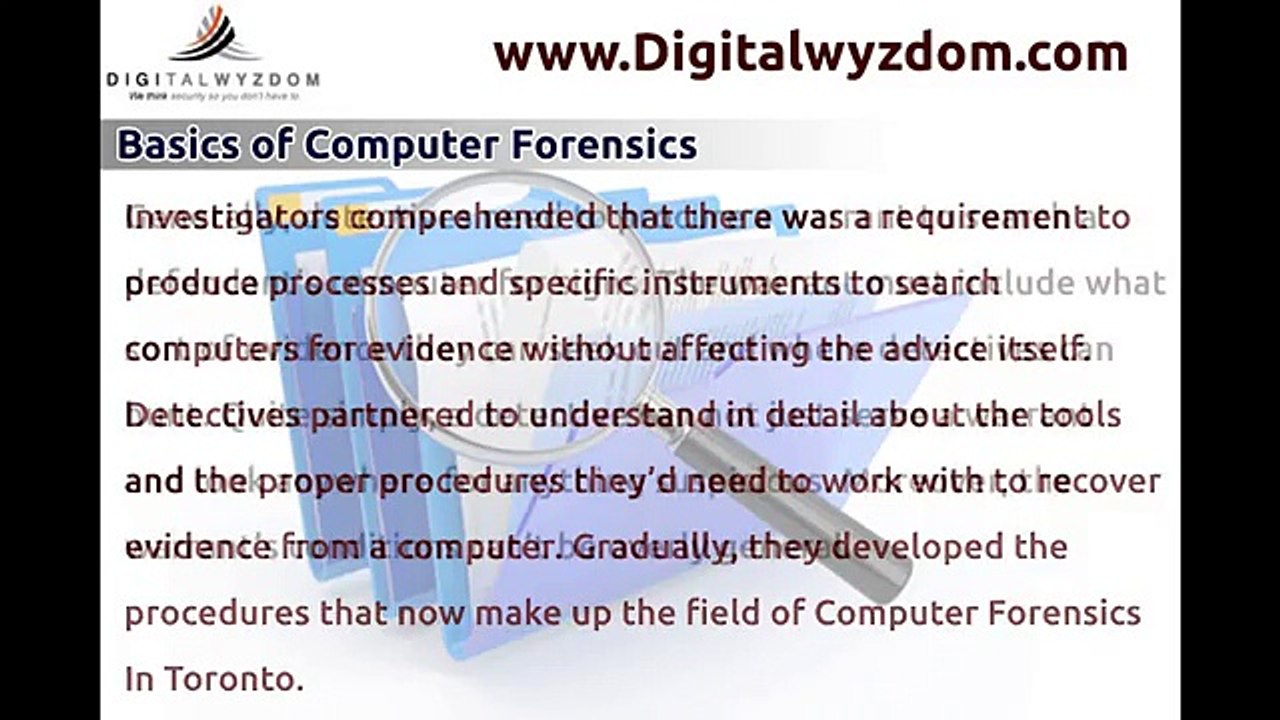
1:03
Basics of Computer Forensics
Computer Forensics
6 views

43:18
Crime Watch - Cold Case Killers (Killer Forensics)
Crime Watch
88 views

0:22
Forensics at the scene of a serious incident in Kingsthorpe
Northampton Chronicle
372 views

4:59
A Forensics Expert on Princess Kate’s Photo—and How Credentialing Tools Can Help Build Trust in a World of Increasing Uncertainty
TIME
824 views

0:30
Hartlepool police incident ongoing as forensics teams spotted
Hartlepool Mail
6.8K views

0:21
Police and forensics in Henderson Drive, Dartford, on Sunday
KentOnline / KMTV
15.4K views

2:14:23
【ENG SUB】Modern forensics travel through ancient times to become a princess, autopsy solve the case!
Completed Short Drama
2.3K views

0:21
Corby boating lake forensics harshita murder -
Northants Telegraph
82.5K views

1:55
Penetration Testing, Incident Response and Forensics Week 1 Quiz Answer | Penetration Test
Course Fry
384 views
41:12
DEFT Jam, Forensics with Autopsy- A Look Inside our CHFI Training Course
Advanced Security
2.2K views
11:55
Introduction to Computer Forensics - Intro to Steganography
David Hays
170 views

22:00
Exiftool Image Forensics Kali Linux 2024 - Extract Info from Images/Photos
Mr. Instruction Pointer
14.4K views
0:41
PDF hidden Text #picoctf #crytography #forensics
hengki lodwig
429 views

2:33
PicoCTF - Enhance! - File Forensics
Hoplite Security
412 views
5:38
CTF Learning Series – ExifTool in Forensics
Knull CTF
47 views

0:58
Zayn Rayyan murder: Forensics team returns to Idaman Apartment
The Star
6.1K views

1:44
What is ADSL | Asymmetric Digital Subscriber Line | Digital Subscriber Line | Purushotam Academy
Purushotam Academy
12.5K views

14:01
Privacy in digital world, Basics of GDPR, Personal Data, Digital Privacy, Emerging Technologies, mba
DWIVEDI GUIDANCE
18.6K views

7:34
Security in Digital Image Processing:Importance of Digital Image Security: Module V,Lecture 5,EC703A
Dr. SANGITA ROY
28 views

1:00
Difference between Digital signature and Digital Certificate in Cryptography in bangla.
content on demand
203 views
0:57
Digital Signature vs Digital Certificate #cybersecurity #crytography #crypto #cissp #cism #shorts
KS InfoSec NG
2.8K views
![8 - Introduction to Cryptography | What is a digital signature & RSA digital signatures [Arabic]](/image/i.ytimg.com/vi/Be_tFoJT0CI/hqdefault.jpg)
5:20
8 - Introduction to Cryptography | What is a digital signature & RSA digital signatures [Arabic]
X-Vector
586 views

11:11
What is digital Signature and how it works | Properties of digital signature
Chirag Bhalodia
40.6K views

2:04
Digital Privacy and the Right to be Protected | Protect Digital Privacy
2 Minute Teachables
639 views

1:01
Digital Circus Episódio 5 - NOVOS VAZAMENTOS do Circo Digital
Rk Play
505.7K views

8:22
Digital Circus Episódio 7 TUDO o que VAZOU - Circo Digital
Rk Play
71.0K views
0:22
😃 What say you about digital signatures? #howto #tutorial #course #notetaking #digital
Paperless Humans
753 views

1:27:35
De la alfabetización tradicional a la digital | Tertulia Pedagógica DocencIA Digital
Docencia Digital
514 views

4:23
Half Adder || Combinational Circuit || Digital Logic Design || Digital Electronics || DLD || DE
Sudhakar Atchala
75.4K views

1:04
Palworld roadmap revealed
Bang Gaming News
4.0K views

0:21
Corby boating lake forensics harshita murder -
Northants Telegraph
82.5K views