Search Results for "deadlock prevention methods in os"
Find videos related to your search query. Browse through our collection of videos matching "deadlock prevention methods in os". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "deadlock prevention methods in os"
50 results found

5:49
World Obesity Day | Awareness, Prevention, and Healthier Choices | Dr. Nikhil Gupta
Sri Balaji Action Medical Institute
8 views

2:44
Baccho Me Food Poisoning Ke Lakshan|Food Poisoning Prevention Tips In Hindi |Boldsky
Boldsky
226 views

7:59
Shainin Problem Solving and Prevention
21CBTV
2 views

0:41
Floods: Prevention measures
Meteored UK
2.9K views

2:20
FLOOD PREVENTION IN BAMBOO
CCNTV6
811 views

3:33
Car security, car theft prevention, home security tips,
JUSTTV5
565 views

3:34
Home Fire Safety – Prevention is Key
foryourlifeca
174 views

6:26
Talking Backflow Prevention and Cross Connection Control
sprinklerdaddy
9 views

1:34
Stop Identity Theft | How To Prevent Identity Theft | Identity Theft Protection Services | Identity Theft Prevention
Identity crew
1 views

1:03
Prévention et sécurité
Parti Socialiste
271 views

1:57
Ant Prevention And Control Techniques
MonkeySee
149 views

3:59
What Compliance Standards Are Relevant To Ransomware Data Exfiltration Prevention?
SecurityFirstCorp
2 views

0:50
Business Crime Prevention Week
The Scarborough News
422 views

25:03
California Governor Gavin Newsom Announces New Statewide Wildfire Prevention Strategies
Forbes Breaking News
4.2K views

1:28
Southern police launches crime prevention program
The Manila Times
1.9K views
0:59
Christian Prouteau : «Le problème de prévention du harcèlement est un problème d’écoute»
CNEWS
250 views

5:15
Garbarino Hammers Janet Yellen: ‘It’d Be A Serious Mistake To Limit Our Fraud Prevention Tools’
Forbes Breaking News
9.0K views

0:50
Etude Notifications smartphone 2025 Route Assurance Prévention
LaTribuneAuto
907 views
![VTU COMPUTER NETWORKS AND SECURITY (18CS52) [Security Methods, Cryptography] (M4 L2)](/image/i.ytimg.com/vi/-TKiDUSDoqk/hqdefault.jpg)
28:04
VTU COMPUTER NETWORKS AND SECURITY (18CS52) [Security Methods, Cryptography] (M4 L2)
Canara Engineering College Mangalore
7.0K views

1:00:27
Tools and Methods Used in Cybercrime Part 4 | Dr. Reshma Kadam
Reshma Patil
309 views

10:45
3 Ways to Make Money with GPT-5 (Beginner Methods)
Liam Ottley
222.9K views

11:08
Tanner Chidester Review (Elite CEO) - Can his methods scale online coaching biz?
Hunter Martin
174 views

8:19
System of Equations: Solve by Graphing and Substitution Methods
Kwakulus
312 views
6:36
Introduction to Substitution Methods | Differential Equations
The Math Tutor
3.6K views
0:45
3 Forecasting Methods in Excel
Kenji Explains
124.2K views

0:21
Time Complexity of sorting methods - Best Case, Average Case, Worst Case/ Data structure - I
Education Guru
50 views

4:16
Spam Review Detection Using the Linguistic and Spammer Behavioral Methods | IEEE Projects Hyderabad
Cloud Technologies
240 views

42:40
AppSecIL 2018 - How to hack cryptographic protocols with formal methods, Ofer Rivlin
OWASP Israel
112 views

8:54
Comparison of the Use of M-Bit LSB Steganography Methods on MAV Files in Information Storage
imelda duma
20 views

3:23
CISSP -60 Security Architecture and Engineering: Understand methods of cryptanalytic attacks
sumon infosec
128 views

32:44
JNTUK R16 III CSE SEM2 CYBER SECURITY UNIT 4 INTRODUCTION TO TOOLS & METHODS USED IN CYBER CRIME LEC
RVIT — Autonomous, Guntur
1.8K views
0:16
Which One’s the Worst? Testing Dent Repair Methods on a Car!#car #dentrepair #Carlovers
Car Lover's Corner
25.9M views
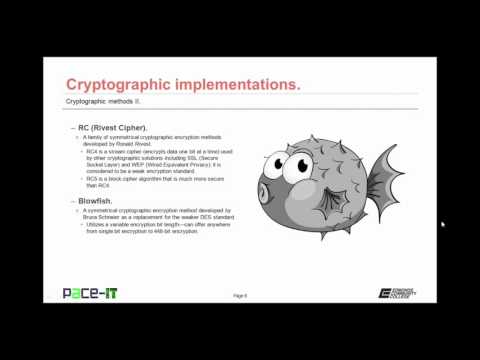
7:54
PACE-IT: Security + 6.2 - Cryptographic Methods (part 2)
PaceIT Online
249 views

9:31
Learn about Encryption Methods in CISSP Exam Prep Part 2 from GogoTraining
GogoTraining - PeopleCert Accredited (ATO)
240 views

0:44
Quantum Algorithm Achieves Major Speedup Over Classical Methods
AI Tech Pulse
1.3K views

52:55
Tools and Methods Used in Cybercrime Part 2 | Dr. Reshma Kadam
Reshma Patil
826 views

1:41
Implementation And Comparison of Three Network Steganography Methods
IBIMA Media
43 views

0:44
Cryptography and information security: encryption algorithms and methods for ensuring data security.
Superpupt
75 views

18:54
Post Quantum Crypto - Lattice Methods
Bill Buchanan OBE
10.1K views

6:28
PACE-IT: Security + 6.2 - Cryptographic Methods (part 1)
PaceIT Online
233 views

35:11
Introduction to cost estimation methods in construction | Estimating project costs
Cost Engineering Professional
181.3K views
1:58
Cryptography and Formal Methods
Galois
3.4K views

1:43
4 Common Encryption Methods to Shield Sensitive Data From Prying Eyes
GetApp
2.2K views

1:03:24
Konstantinos Kartas: Nonstandard methods in almost mathematics
Hausdorff Center for Mathematics
177 views
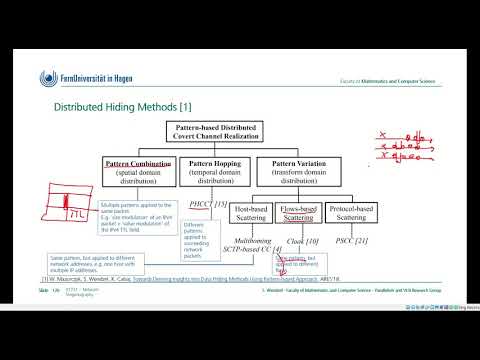
1:10:03
01731, Network Steganography, Chapter 6 (Distributed Hiding Methods), FernUniversität in Hagen
Steffen Wendzel
885 views

3:42
Securing ISF Data: Encryption and Integrity Methods!
ISF Solution
6 views
7:19
Tools and Methods in Cyber Security
Rohini CSE Tech Talk (RCTT)
630 views

24:31
KGB HQ - All Methods - Call of Duty Black Ops Cold War
AFGuidesHD
2.0M views

10:21
#59 Internet Key Exchange - Phases, Modes, Methods |CNS|
Trouble- Free
72.1K views
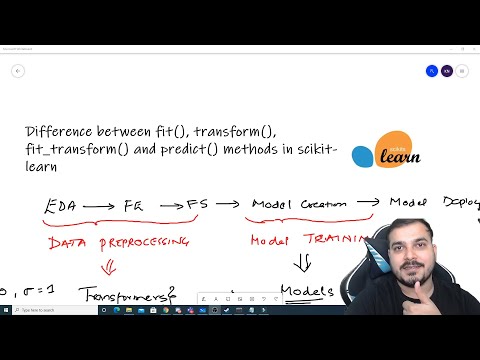
26:03
Difference Between fit(), transform(), fit_transform() and predict() methods in Scikit-Learn
Krish Naik
104.8K views