Search Results for "AI cybersecurity"
Find videos related to your search query. Browse through our collection of videos matching "AI cybersecurity". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "AI cybersecurity"
50 results found

8:56
Ihr habt ein FALSCHES BILD vom Job CYBERSECURITY
The Morpheus Tutorials
76.3K views
0:14
What is the difference between symmetric and asymmetric encryption? #quiz #cybersecurity
Cybersecurity Training
5 views

1:00
Effectualnary Shorts - Cybersecurity Keyword Learning - ES046 Cryptanalysis
Effectualness
22 views

0:59
Asymmetric Cryptography 🔐 #cybersecurity #shorts
TheQuirky-ishTutor
322 views

0:41
Symmetric Encryption Explained - Types of Encryption - Harsh Nagar - Cybersecurity
Harsh Nagar
763 views
34:07
Software Security | Cybersecurity Specialization | Coursera | Week 1 to 6 | Course 2 Quiz Answers
Learning Updates
3.3K views

0:52
Decoding Steganography in Cybersecurity: Unseen Data Threats
TechSavvy Plus
28 views

0:40
Asymmetric vs Symmetric Encryption #encryption #cybersecurity
Communinvest
586 views
42:55
What is Post-Quantum Cryptography? | The Future of Cybersecurity | TripleCyber Tech Talk
TripleCyber
361 views
6:10
CTF Topics to Know for ABSOLUTE Beginners | Cybersecurity Series | Kaity Codes
KT Codes
2.7K views

0:09
What is Authentication? #cybersecurity #learn #terms #cyber #security #tech
IT and Cyber Security Definitions
750 views

14:20
Why Cybersecurity is Recession-Proof // AI Hype vs Reality
TechButMakeItReal
64.6K views

6:42
Careers in Cybersecurity
IBM Technology
530.5K views

0:21
Quantum Computers vs. Encryption: Game Over for Cybersecurity?
Dr. Carmenatty - AI, Cybersecurity & Quantum Comp.
14 views

4:28
How Is Steganography Used In Cybersecurity? - SecurityFirstCorp.com
SecurityFirstCorp
9 views

44:14
CyberSecurity Steganography
Learn & Earn
3 views
![Cybersecurity CLASSROOM [Cohort 4]](/image/i.ytimg.com/vi/4OKF3Ne0qjw/hqdefault.jpg)
1:54:36
Cybersecurity CLASSROOM [Cohort 4]
MyDreamConnect LC
4 views

0:07
Cybersecurity Definition #15 - Brute Force Attack #shorts #short #bruteforce
Ken Underhill - Cybersecurity Training
1.3K views

0:47
How Do Data Breaches Happen? #HIPAA #EDI #cybersecurity #breach #IT #technology #tech #healthcare
HIPAA Vault
82 views
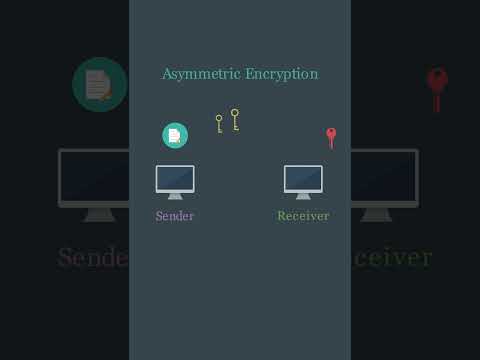
0:44
Asymmetric Encryption Visually Explained #cybersecurity #shortsvideo
ByteQuest
26.4K views
0:39
Asymmetric Encryption is Just a Mailbox #ai #twitch #cybersecurity #security
gdcomplex
650 views

11:08
7 Things I Wish I Knew Before Starting Cybersecurity
Addie LaMarr
74.0K views

1:26
Encryption: Elliptic-Curve Cryptography #cryptography #encryption #cybersecurity #cissp
The Cyber Dojo
211 views
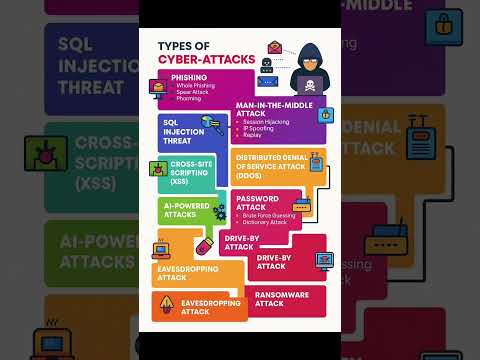
0:16
Types of Cyber-Attacks!!! #ccna #cybersecurity #networking #programming #techshorts #cryptocurrency
Networks Professionals
11 views

1:26
Cybersecurity Shorts: Day 97 - What is HASHING ?
Shiva Ram Tech
1.4K views

8:25
Russia-Ukraine conflict and US cybersecurity | Dig In 2 It
WFMY News 2
18.2K views

3:52
Cryptography University of Maryland,College Park | Cryptography Week 3 |Cybersecurity Specialization
Career4freshers
207 views
0:59
Password vs Passkey #cybersecurity #dev #code #softwareengineer #programming
Beyond Identity
56.5K views

9:34
Cybersecurity Trends and Essential Skills for 2025
Tiff In Tech
9.0K views

0:35
CyberSecurity Definitions | Exploit
Relative Security
503 views

5:02
Cybersecurity and crime | Internet 101 | Computer Science | Khan Academy
Khan Academy
316.2K views
0:51
CISSP Quiz #quiz #cybersecurity
LufSec Cyber Security
115 views

0:43
Encryption Explained: How to Protect Your Data from Hackers #cybersecurity #technology #tech
HackTales
65 views

0:38
Binwalk Image forensic extract information from image #cybersecurity #imageforensic #binwalk #exif
Zodiac
8.1K views

31:15
Cybersecurity Architecture: Who Are You? Identity and Access Management
IBM Technology
369.5K views

1:49
How to Solve CTFs (Capture The Flag) | Complete Beginner’s Guide #ctfchallenge #ctf #cybersecurity
MainEkHacker
3.7K views
1:30
Top Cybersecurity Expert Reveals Best Encryption Techniques
MonkWire
89 views
1:24
Der Vastaamo Fall #informatik #cybersecurity #fakten #wissen
Hood Informatik
11.1K views

59:29
Cybersecurity Basics: Crash Course for Beginners
Coding Bootcamps
6 views

0:59
3 programming Languages to learn in 2023 for cybersecurity #shorts
Cybersecurity Guy
293 views

9:34
(CH7/2) Cryptography - Types of Cybersecurity Attacks Part 2
FENIXSOYA
30 views

1:24
Session Hijacking Explained in less than 90 Seconds #SessionHijacking #Cybersecurity #EthicalHacking
Yaniv Hoffman
5.5K views

3:14
What Is The Difference Between Symmetric And Asymmetric Encryption In Cybersecurity?
Your Engineering Future
1 views

0:58
Revolutionizing Cybersecurity with Quantum Key Distribution
Tech Visionary Insights
0 views

0:39
Best Cybersecurity Jobs of 2024!
Daily CyberConnect
23 views

1:00
What is IoT ? Internet of things: Explained #cybersecurity #shorts
TutorialsFreak
805 views

0:24
CyberSecurity Definitions | Man in the Middle Attack
Relative Security
969 views
0:16
Decrypt Files Instantly with AES-256 🔓 | Python Decryption Tool | Cybersecurity Project
Esraa Codes
1.9K views

1:08
Hybrid Cryptography: Future-Proof Your Security! #shorts #cybersecurity
Your SASE Gateway
405 views
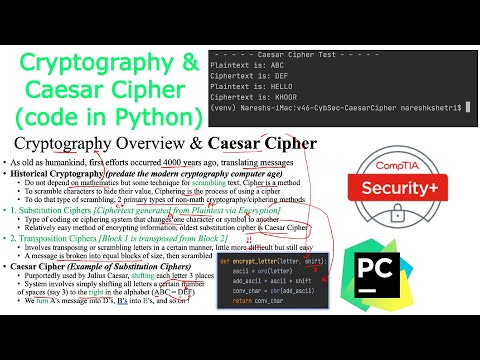
4:52
Cybersecurity | Cryptography | Caesar Cipher
Naresh KSHETRI
104 views