Search Results for "woo and lam proposal in mutual authentication"
Find videos related to your search query. Browse through our collection of videos matching "woo and lam proposal in mutual authentication". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "woo and lam proposal in mutual authentication"
50 results found

3:09
Learn Colors and Shapes with Animals Woo 6
Kzk75716
566 views

0:13
Lisa and Cha Eun woo from Penshoppe to Bvlgari
LuckyCat
2 views

2:33
BTS V And JIN "LOST" TO ASTRO CHA EUN WOO!!!
BTS Latest
66 views

1:53:40
ENG SUBCinderella didn't love CEO anymore, he panicked and brought his son to woo her!#cdrama
Short Viral
491 views

2:06
Bihar Elections 2025: Will Nitish Secure CM Post if JDU Gets Numbers and RJD Attempts to Woo Him?
Asianet News English
18 views

39:03
Covid Cryptography 6: Message Authentication Codes and Authenticated Encryption
MathMesh
122 views

12:48
How Kerberos Authentication Works and Why You Should Use It Detailed Explanation in Telugu
Lucky Tech
7.7K views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

6:23
Secrecy and Authentication using Public-Key/Two-Key Cryptography or Asymmetric Encryption
CSE Adil
86 views

11:28
Kerberos Version 4 | Kerberos Version 4 using Authentication and Ticket Granting Server
Chirag Bhalodia
27.4K views

4:49
Kerberos Authentication Protocol | Cryptography and System Security
Ekeeda
56 views

20:53
MAC in Cryptography || Message Authentication Code in Network Security And Cryptography.
Anas Khan
192 views

1:00:51
CNIT 141: 12. Message Authentication Codes (MACs) and 13. Key Establishment
Sam Bowne
136 views

12:54
Authentication Functions | Cryptography and Network Security
Ekeeda
910 views

1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views

18:07
Lecture 23: Public key cryptography and authentication method Asymmetric Key Requirements
QZ Historia
41 views

6:35
Kerberos - Network Authentication Protocol explained in hindi || Working ,History ,AS ,TGS and AP
Unbeaten Learning
112.9K views

1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views

13:19
18_Public Key Cryptography - Key pair, Secrecy and Authentication
Angayarkanni S A
238 views

2:24
Network Security and Cryptography: Message Authentication Code(MAC)
OnlineTeacher
598 views

1:04:18
Assumptions of Encryption and Authentication (ITS335, L04, Y15)
Steven Gordon
1.2K views

1:04:28
Cryptography and Network Security BCS072 Unit 3 One shot | Message Authentication Codes Unit 3 AKTU
EduShine Classes - Arman Ali
273 views

9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

1:19:10
Authentication with Symmetric Key Crypto and MACs (CSS322, L17, Y14)
Steven Gordon
1.5K views

26:44
Message Integrity and Authentication
Computer Science Learning Videos
336 views

3:24
MAC (Message Authentication Code) | Unit 4 Cryptography and Cyber Security CB3491 | Anna University
CSE IT Exam Preparation
1.1K views

2:46
USER AUTHENTICATION USING CRYPTOGRAPHY AND STEGANOGRAPHY FOR WEB APPLICATIONS
Gagan Suneja
214 views

9:40
Message Authentication Codes: CMAC and HMAC
Cihangir Tezcan
4.8K views

11:49
Network Security - Message Authentication Code (MAC) | Cryptography and Network Security
Lectures by Shreedarshan K
2.5K views

1:18:04
Authentication and Public Key Cryptography (ITS335, Lecture 5, 2013)
Steven Gordon
1.3K views
1:06:48
Camp++ 0x7e2 // Modern cryptographic password and authentication methods by stf
Budapest Hackerspace
168 views

43:20
CCT 074: Management of Identification and Authentication - Future Trends (CISSP Domain 5)
CISSP Cyber Training - Shon Gerber
13 views

0:18
Critical Go Parser Vulnerabilities Enable Authentication Bypass and Data Theft in Production Systems
Secure Thread
122 views

12:09
Lecture 22: Lecture 4 slides- Public key cryptography and authentication method
QZ Historia
42 views

0:59
Passwordless Authentication Using a Combination of Cryptography, Steganography, and Biometrics
Journal Club
14 views
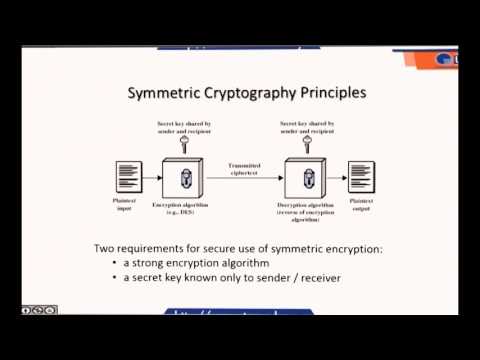
6:05
LECTURE 2- AUTHENTICATION AND BASIC CRYPTOGRAPHY (PART2)
UTeM MOOC
40 views

12:56
60 Multifold Secured Bank Application authentication service using Random Visual Cryptography and Mu
ICMISC
13 views

0:37
Multi-factor Authentication and Modified DNA Cryptography #sciencefather #researchawards
Research Scientist
1.1K views

1:35:00
Entity Authentication and Symmetric Key Establishment - Bart Preneel
secappdev.org
2.5K views

32:24
public key encryption: Key distribution, message Authentication and hash function- part1
Dr. Moonther
384 views

32:59
Message Integrity and Authentication in Cryptography (Bangla)
Jahidul Islam GUB
534 views

29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views

14:41
MAC in Cryptography || Message Authentication Code in Cryptography and network security
Abhishek Sharma
396.9K views

11:16
Authentication Requirements | Cryptography and Network Security
Ekeeda
8.7K views

24:09
Passwordless Authentication Using Steganography, Cryptography And Biometrics - Tunde Oduguwa
BSides Bristol
39 views

10:23
Analysis of Biometric Authentication System – Security Issues and Working using Visual Cryptography
OKOKPROJECTS
114 views

58:47
Kerberos Version 4 & 5 and Remote User Authentication with Asymmetric Encryption -#21is71 VTU 7thsem
VTU padhai
2.3K views

14:37
Digital Signatures, Message Integrity, and Authentication | Computer Networks Ep 8.3 | Kurose & Ross
Epic Networks Lab
7.6K views

1:20:56
COSIC Course 2024: "Cryptographic protocols for entity authentication and..." (Bart Preneel, COSIC)
COSIC - Computer Security and Industrial Cryptography
239 views

5:55
#Authentication Requirements In Cryptography and Network Security #cns #jntuh #conceptclearbydrmvk
Concept Clear
733 views