Search Results for "secure AI"
Find videos related to your search query. Browse through our collection of videos matching "secure AI". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "secure AI"
53 results found

4:18
What Are The Career Paths In Secure Cryptography? - Next LVL Programming
NextLVLProgramming
34 views

12:28
Master Encryption in Just 10 Minutes – Stay Secure Online! | Cyber nanban
Cyber Nanban
11.4K views

5:01
Steganography method to secure patients’ medical report using Wavelet Transform
Raja Sekar J
17 views

14:29
SQL SERVER # 005. Restore from Secure SQL Database Backup File
Midware Cloud
519 views

2:46
What Is Symmetric-key Encryption And How Does It Secure Data? - Emerging Tech Insider
Emerging Tech Insider
1 views
50:30
Cryptography vs. Steganography: Unlocking the Secrets of Secure Communication | Stuintern
Stuintern
97 views

2:47
Locking Down Data: Cryptographic Protocols for Secure Communication Explained
Operational Excellence Mastery
6 views

0:42
🔐 What is SHA-256? | How This Powerful 🔢 Hash Function Keeps Your Data Secure! 🛡️#sha256 #crypto
BitnByte Mining
8.1K views

0:26
Show/Hide samsung secure folder #s25ultra #securefolder
Topical Talks
246.2K views

50:19
Secure Multiparty Computation 1/2
Institut Henri Poincaré
210 views

5:16
Post-Quantum Cryptography Explained: How to Secure Your Business Before the Quantum Era
AGMP
7 views
18:50
SoK: General Purpose Frameworks for Secure Multi-Party Computation
IEEE Symposium on Security and Privacy
2.0K views

3:06
How Does Cryptography Enable Secure Communication? - Tactical Warfare Experts
Tactical Warfare Experts
4 views

0:56
Histogram Shifting-Based Quick Response Steganography Method for Secure Communication
Electrical Engineering
166 views

5:52
Study of Quantum Cryptography Protocols for Secure Quantum Communication by Brian Tey 17142084/1
Brian Tey
29 views

21:34
Quantum Secure Symmetric Key Cryptography Based on Hidden Shifts
IACR
257 views

1:37
Cryptography: Unlocking the secrets of secure communication
Moxso
20 views

0:35
Post-Quantum Adoption. QRL vs Cellframe, A Comparison of Secure Systems
Crypto Dypto
173 views

3:42
How Secure Is Quantum Cryptography Compared to Traditional Methods? - Quantum Tech Explained
Quantum Tech Explained
2 views

0:12
Decrypt messages using Secure Text Keyboard for iPhone
Secure Text Keyboard
3.4K views

0:45
Unleashing the Power of Secure TLS Encryption
Paubox
793 views

0:31
Crypto Quiz Challenge: Guess the Guardian! Discover the Web's Secure Sentinel Algorithm! 🚀🔒
CodingQuizzy
6 views
![Transposition Cipher | Cryptography and Network Security [Secure transmission of message]](/image/i.ytimg.com/vi/kHy9bdUSVig/hqdefault.jpg)
10:16
Transposition Cipher | Cryptography and Network Security [Secure transmission of message]
Lectures by Shreedarshan K
515 views
1:09:14
s-20: Cryptographic Protocols and Secure Computation II
IACR
361 views

1:45
A Secure Image Steganography Based on RSA Algorithm and Hash LSB Technique
InnovationAdsOfIndia
3.9K views
3:34
Cryptographic Algorithms and Secure Hardware
UCLouvain - Université catholique de Louvain
3.1K views

7:13
A SECURE DATA DYNAMICS AND PUBLIC AUDITING SCHEME FOR CLOUD STORAGE | CLOUD COMPUTING
Takeoff Edu Group
523 views
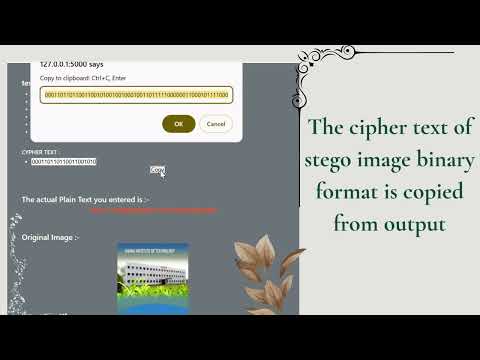
3:15
Crypto with Steganography | Secure Your Data in Images! 🔍🖼️
Anjali
7 views

0:51
Quantum Cryptography: Secure Future of Blockchain
crypto blockchain
10 views

0:28
Secure Your WhatsApp from Hackers! Essential Privacy Tips | Whatsapp Hacking Avoidance
Cybersafe Learning
32.9K views

23:36
22-PGP(Pretty Good Privacy) Explained | E-mail Security | Secure Email Using Public Key Cryptography
Sundeep Saradhi Kanthety
224.4K views

0:10
Secure Communication Technologies Cryptography, Anti-jamming, Stealth
APPSC Notes
33 views

2:17
Secure File Storage On Cloud Using Hybrid Cryptography (part 3)
Awais Akbar
1.1K views
2:39
Secure File Storage Using Hybrid Cryptography
Sheetal M
1.7K views

4:52
Geopolitical Quantum Cryptography Race: Why Bharat Must Act Now to Secure Our Digital Future
Parth Sane
58 views

0:50
Secure Crypto Wallet Essentials #shorts
All-Time High
516 views

5:52
ISRO 2nd Test of Quantum Communication | Future of secure communication technology
Indian Defense Analysis
4.0K views

18:36
How do these curves help the internet be secure? - Elliptic Curve Cryptography
Alice Micheloni
468 views

0:47
The Evolution of Quantum Cryptography in Secure Communications
admn
12 views

0:45
The Secret to Secure Data: Encryption by Ak. Coder
Ak. Coder
37 views
18:06
How secure is the internet against quantum computers?
Dr Waku
949 views
1:00
Post Quantum Cryptography Secure Data in the Quantum Age
Relax Reels shorts
13 views

3:06
What Are Stream Ciphers In Secure Cryptography? - Next LVL Programming
NextLVLProgramming
1 views

1:00
Rise of Decentralized Key Generation & Quantum-Secure #Crypto 🔒
Intu
65 views

3:57
Module 4.2 Applications of Public key cryptosystems|S8 ECE|SECURE COMMUNICATION KTU|ECT434
bushara abdulrahim
2.6K views

2:18
Cryptology: Understanding the Science of Secure Communication
AI.Hacker
11 views

3:22
Can Quantum Cryptography Secure Internet Communication? - Next LVL Programming
NextLVLProgramming
5 views
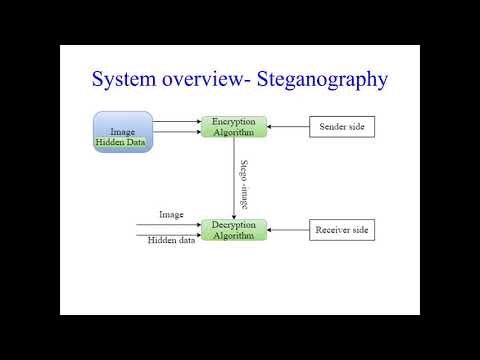
13:14
235_Study of secure data transmission based wavelets using steganography and cryptography techniques
CMRCET CSE
11 views

0:49
The Ultimate Guide to ProtonMail Secure Your Emails Today
Neo
24.2K views

10:52
West Ham vs Newcastle 3-1 Last Minute Goal for Souček Secure the Win for the Hammers & Nuno Santo
PlEYE
2.5K views

1:58
Identifying Secure Websites
Money Making Mastery
260 views

0:54
With AI, jets and police squadrons, Paris is securing the Olympics — and worrying critics
The Manila Times
255 views

4:38
Why AI Must Adopt Blockchain for Greater Security & Democracy 🔒
Yahoo UK
846 views