Search Results for "run scheme"
Find videos related to your search query. Browse through our collection of videos matching "run scheme". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "run scheme"
50 results found

59:51
COSIC seminar "DME, a multivariate post quantum KEM and signature scheme" (Ignacio Luengo)
COSIC - Computer Security and Industrial Cryptography
153 views

23:44
An Existential Unforgeable Signature Scheme based on Multivariate Quadratic Equations
IACR
131 views

25:59
Hiroki Furue: A New Fault Attack on UOV Multivariate Signature Scheme
PQCrypto conference videos
139 views
![Color-Visual-Cryptography-Scheme[www.savevid.com].flv](/image/i.ytimg.com/vi/y5LnDZW1erc/hqdefault.jpg)
0:29
Color-Visual-Cryptography-Scheme[www.savevid.com].flv
Deepak
285 views
1:08
Cryptanalysis of An Identity Based Encryption Scheme with Equality Test and Improvement
IFoxProjects
51 views

1:56
Salted Password Scheme - Applied Cryptography
Udacity
43.0K views
2:21
Cryptanalysis of a generalized ring signature scheme
Naren Projects
383 views
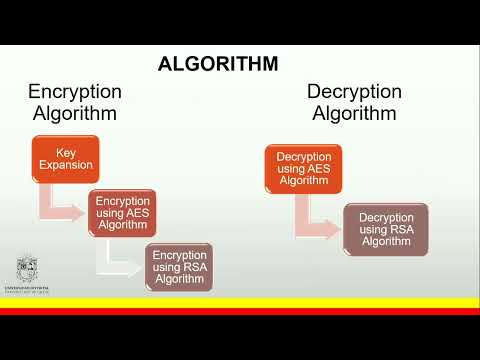
10:37
Performance Measurement of a Hybrid Encryption Scheme on an Embedded System
Computer Science & IT Conference Proceedings
37 views

2:21
Explained: London’s Ulez scheme and how it works
The Independent
3 views

49:40
Design and of Encryption/ Decryption Architectures for BFV Homomorphic Encryption Scheme
Ekalavya Projects
757 views

6:25
V2c: Kyber-PKE (full scheme) (Kyber and Dilithium short course)
Cryptography 101
3.1K views

0:25
Salted Password Scheme Solution - Applied Cryptography
Udacity
3.0K views

0:51
Elliptic Curve Cryptography-Based Scheme for Secure Signaling and Data Exchanges in P... | RTCL.TV
Social RTCL TV
106 views

9:10
Digital Signature Scheme using RSA concept
Abhishek Sharma
170.9K views

3:54
How to establish an encryption key securely with the Quantum Key Distribution scheme ?
satnamo
2.4K views

0:31
A Multilayer Steganographic Method Using Improved Exploiting Modification Directions Scheme
IFox Projects
9 views

2:57
Caesar Clown Become Bege's Sworn Brother in the Scheme of Assasinating Big Mom
DragonGoku
5 views

0:46
Implementation of cycling scheme - cycling map
getonyourbikes
1 views
1:15
Image encryption scheme using DNA and bases probability
sahil
438 views

9:55
Math important questions#KCSE 2014 paper 1 #questions and answers #STEM #marking scheme
Revision questions
0 views

0:53
The Beginner’s Guide to CPF Investment Scheme
The FinLens
4 views

2:37
SP Setia offers differential loan scheme
The Star
13 views

1:54
Expanded number coding scheme in Metro Manila now in effect | News Night
CNN Philippines
386 views

3:34
How does the emission trading scheme work | Kendrick Zale
Kendrick Zale
45 views

1:01
A Secure Payment Scheme with Low Communication and Processing Overhead for Multihop Wireless Networks
JPInfo
25 views

1:17
Shiv Dhara provides key attraction of renewable energy & re-use water supply in their housing scheme
TV9 Gujarati
0 views

6:51
Advantages and disadvantages of Agnipath scheme by VK Dutta
Aaj Tak
3 views

0:18
What is the food security scheme?
ABP NETWORK
0 views
5:29
MEDICAL VIDEO WATERMARKING SCHEME FOR TELEMEDICINE APPLICATIONS | Steganography Projects
Takeoff Edu Group
243 views
3:31
Reversible Data Hiding Scheme for Images Using Gray Code Pixel Optimization | (PSNR) (MSE) (SSIM)
Amodha InfoTech
69 views

12:41
Encrypting your Safex Private Key with Shamir's Secret Sharing Scheme
Safex News
660 views

14:05
Introduction to Cryptography: Feistel Scheme
Wolfram U
400 views

1:47
Enhanced Password Processing Scheme Based on Visual Cryptography and OCR
DHS_IEEE_2018_&_2019_Projects
378 views
5:15
vlsi projects @ Embedded Innovation Lab .Turbo Code-Based Error Correction Scheme
Ashokkumar Krishnan
12 views

9:46
My Korean Jagiya: Sexy secretary Hannah's scheme | RECAP (HD)
GMA Network
17 views
3:22
National Savings Certificate Scheme क्या है, Post Office में निवेश से मिलेगा लाभ | Good Returns
Goodreturns
47 views

10:55
Explained: What Is Centre's Lucrative Agnipath Recruitment Scheme & Its Implications?| Agneepath
HW News English
78 views
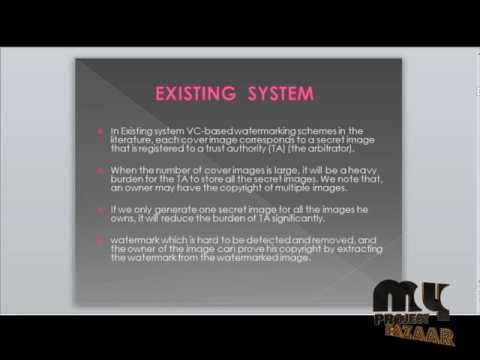
7:01
Robust visual cryptography-based watermarking scheme for multiple cover images and multiple owners
MyProjectBazaar
133 views

1:17:51
Lecture 15: Elgamal Encryption Scheme by Christof Paar
Introduction to Cryptography by Christof Paar
67.2K views
31:12
An Efficient Multi User Searchable Encryption Scheme without Query Transformation Over Outsourced En
1 Crore Projects
626 views

8:34
11th Class English Pairing Scheme 2023 _ 11th Class English Guess Paper 2023 _ 11th English Paper
Royal Tuition Academy
14 views

23:31
Biometrics based cryptographic key generation and binding scheme
Cybersecurity IITD
427 views

11:24
MOD 3- A Hybrid scheme, Public key distribution scenario, Exchange of public key certificates
SAVI
376 views

15:55
4.12 Elgammal Digital Signature Scheme in Tamil
BECAUSE
20.0K views
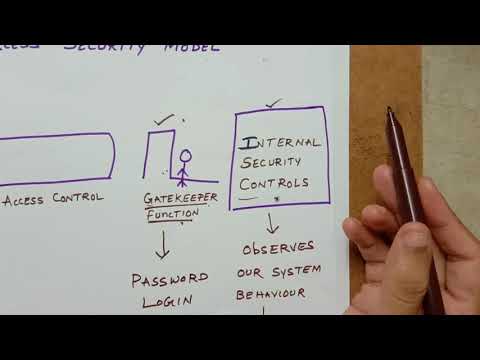
16:09
Network security model and symmetric encryption scheme
Sarvani Anandarao
96 views

1:24
What is a Ponzi Scheme?
jasonsereno
124 views
0:28
Implementation and Performance Evaluation of RNS Variants of the BFV Homomorphic Encryption Scheme
IFoxProjects
62 views
5:19
A New K Out Of N Secret Image Sharing Scheme In Visual Cryptography - 1Crore Projects
1 Crore Projects
634 views

0:17
Recursive Visual Cryptography Scheme
Wolfram Demonstrations Project
220 views
0:17
Traditional Visual Cryptography Scheme
Wolfram Demonstrations Project
729 views