Search Results for "how to compute a hash"
Find videos related to your search query. Browse through our collection of videos matching "how to compute a hash". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "how to compute a hash"
50 results found

10:14
Bitcoin - Cryptographic hash function
Khan Academy
284.5K views

0:51
Hash Functions
Gnana Lakshmi T C
149 views

4:34
DEADLY HASH "Dope Spot" "No Chaser" "Still the Same"#420mix
DeadlyHashTV
30.0K views

9:04
Message Digest and Digital Signature | Cryptographic Hash Function
saurabhschool
16.4K views

57:46
Applied Cryptography: 3. Hash functions and HMAC
Applied Cryptography by University of Tartu
635 views

1:30
شرح الهاشينج ببساطة | Hash Function وطرق حل التصادم
Abdulla Galaby
55 views

13:44
V3a: Hash functions: Fundamental concepts (Applied Cryptography 101)
Cryptography 101
1.0K views

3:40
What Is Hash-Based Cryptography? - CryptoBasics360.com
CryptoBasics360
29 views

8:32
What is a Cryptographic Hash function?
Keifer Kif
1.4K views

46:48
Cryptographic Hash Algorithms
Hunter Johnson
243 views

2:36
What is Hashing? Hash Functions Explained Simply
Lisk
440.5K views

24:54
Understanding and implementing a Hash Table (in C)
Jacob Sorber
412.3K views

10:53
PART 4 | HASH FUNCTION ATHENTICATION TECHNIQUE IN CRYPTOGRAPHY & NETWORK SECURITY (BANGLA)
COMPUTER SCIENCE WITH BHASKAR SIR
229 views
![[CompNetSec] - 13 - Cryptographic Hash Functions](/image/i.ytimg.com/vi/2yxHePuitJc/hqdefault.jpg.pagespeed.ce.bngtY8SLsy.jpg)
1:00:43
[CompNetSec] - 13 - Cryptographic Hash Functions
Hicham Elmongui
7.3K views

4:19
STM32L5 OLT - 26 . Peripheral HASH
STMicroelectronics
132 views

26:57
CH3 Cryptographic Hash Functions 1
د محمود-الحاسبات وتقنية المعلومات
293 views

14:13
#4 Why do we need cryptography hash functions SHA256 for blockchain network?
FuTech
274 views

10:50
Kryptographie #74 - RSA Full Domain Hash
The Morpheus Tutorials
1.1K views
3:41
DEADLY HASH "I GET IT " Feat BIG OMEEZY - DIAMONIQUE
DeadlyHashTV
48.4K views

10:49
what is hash function, types of cryptography algorithm in details notes
sawji gyaan
11 views
1:11:56
Kuliah Kriptografi - Fungsi Hash
Aminudin Aminudin
323 views

56:32
New Approaches for Building Cryptographic Hash Functions
Microsoft Research
114 views

3:48
Double Hash - Applied Cryptography
Udacity
5.5K views

0:49
What is hash in Blockchain by Amit Sir
crackacademy
763 views

10:47
Hash function | S8 ECE | SECURE COMMUNICATION
bushara abdulrahim
3.1K views

12:36
Hashing and Hash Cracking Explained Simply! (2021) | MD5, SHA1, and SHA256
Josh Madakor
22.3K views

6:56
Hash-Based Indexing Explained: Database Storage & Retrieval for Beginners
CodeLucky
75 views

4:28
Part 8 - What is Hash in Blockchain?
Blockholic
1.7K views

0:43
Untangling Cryptographic Hash Functions
cryptoanalysis
6 views
14:00
How the MD5 hash function works (from scratch)
RareSkills
34.9K views

7:17
Privacidade em Risco? Entendendo Criptografia e Algoritmos Hash
Fernanda Kipper | Dev
7.6K views

0:58
What is Hash Function
code with ajmal
59 views
0:21
How to crack sha256 hash using John
Opensky_
4.7K views

1:15:03
Andreas Hüsling - "Hash-Based Signatures" (PQCSA summer school 2025)
COSIC - Computer Security and Industrial Cryptography
46 views

6:39
Hash-Funktionen: SHA &Co. // deutsch
the native web GmbH
8.0K views
0:44
Cryptography - What is a hash function? | Answer the Questions Series #shorts #thm #tryhackme
CyberTodd
561 views

3:45
08. Big Lyrx - Killa P featuring Deadly Hash
BIGLYRXTV
155 views

18:43
PART 1 | Cryptographic Hash Functions
who know me
5 views

0:58
Python Sets vs Lists Understanding Hash Tables and Buckets Explained! #coding #programming #viral
PythonSourceCodeORG
93.6K views

0:56
Cryptographic Hash Functions
Mathematical Minutes
46 views

0:15
Mastering Hash Cracking with John the Ripper: A Guide to Password Security | Pakistani Hacker
Pakistani Hacker
30.3K views
13:25
INS: Unit-5 Application of Cryptographic Hash function
Twinkal Patel
22.2K views

2:50
Understanding "Salted Hash": A Guide to Cryptography Terms
Listen and Learn English
18 views
41:20
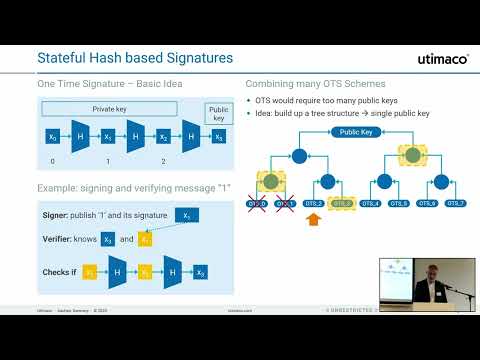
Stateful Hash-Based Signature Schemes
PKI Consortium
1.4K views

0:12
Cryptographic Hash Definition - Word of the Day
Simple Wealth Academy™️
45 views

40:28
Hash Function
Kifayat Ullah
474 views

6:50
Cryptographic Hash Functions (Part 1): Overview
Sourcefire
52.3K views

24:32
C++ Builder - Hash functions, Symmetric + Asymmetric Cryptography, and Digital Signature (LockBox)
VCL Examples
3.1K views
45:47
An Introduction to Cryptographic Hash Function
Ravi Mittal
95 views

16:13
ACISP2020 Tightly Secure Chameleon Hash Functions in the Multi User Setting and Their Applications
Xiangyu Liu
230 views
Previous Page 3