Search Results for "digital signature algorithm in network security"
Find videos related to your search query. Browse through our collection of videos matching "digital signature algorithm in network security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "digital signature algorithm in network security"
50 results found

5:03
Checking the health of Security Network Protection and Security Network IPS sensors
Al Quran
6 views

2:24
Trusted System:Trusted System in network security| cryptography and network security| ICS|CNS |Hindi
Zixplain
15.7K views

1:20
Projects on Network Security and Cryptography | Thesis on Network Security and Cryptography
Phdtopic. com
516 views

18:03
02-Types of Attacks in Network Security | Active vs Passive Attacks | Cryptography &Network Security
Sundeep Saradhi Kanthety
406.7K views

9:26
RSA Algorithm in Cryptography with example | RSA Algorithm by Geeta Chaudhary | RSA Algorithm in net
Short Tricks Learning
86 views

23:17
RSA Algorithm || Rivest Shamir Adleman Public Key Cryptographic Algorithm || RSA Algorithm example
Dr. Riaz Khan
405 views

7:01
Algorithm Vs #Program & Algorithm Vs Pseudocode | Lec 6 | Design & Analysis of Algorithm
CSE Guru
2.9K views

13:18
What Is An Algorithm? | What Exactly Is Algorithm? | Algorithm Basics Explained | Simplilearn
Simplilearn
199.6K views

1:00
Algorithm Vs Pseudocode #cseguru #algorithm #ada #cseguruadavideos #algorithmdesign #daa #algorithm
CSE Guru
25.4K views
0:03
Algorithm types and algorithm examples #algorithm #factorial
Math360
173 views

0:54
What Exactly is An Algorithm? - Algorithm Explained - With Examples #datastructures #algorithm
Hazy Genesis
965 views

9:05
RSA Algorithm | RSA Algorithm Concept | RSA Algorithm with Example | Hindi / Urdu
Ask Faizan
1.8K views

7:34
RSA algorithm example|rsa algorithm encryption and decryption example|rsa example|rsa algorithm
Last Night Study
143.8K views

2:51
What is an Algorithm | How to write ALGORITHMS | Algorithm for Beginners | Introduction to Algorithm
Epic Learning
68.8K views

9:10
RSA Algorithm Example | rsa example | rsa algorithm | rsa algorithm bangla | Zobayer Academy
Zobayer Academy
3.5K views

7:34
Security in Digital Image Processing:Importance of Digital Image Security: Module V,Lecture 5,EC703A
Dr. SANGITA ROY
28 views

9:31
24. #Perceptron network | Architecture, Flowchart | Training algorithm | testing algorithm
Preethi J
67.2K views

2:47
IP Security overview, IP Security architecture, Cryptography and Network Security.
Algorithm Pod
488 views

1:01:28
Cryptography & Network Security | CH1.2 The OSI Security Architecture & 1.3 Security Attacks
Computer & IT lectures
67 views

7:32
CRYPTOGRAPHY AND NETWORK SECURITY(2) Principles of security, Security Services
Algorithm Pod
143 views

8:46
Security Mechanisms | Computer Network Security | Information and Cyber Security |Full Course|Lec-04
Abhideep Online Education
11.7K views

6:31
Network Security vs Cyber Security | What is Security? | Explained in Hindi
Tech Guru Manjit
16.0K views

12:12
#5 Security Mechanisms In Network Security | Information Security |
Trouble- Free
71.0K views

0:06
Read Security+ Guide to Network Security Fundamentals (Cyber Security) PDF Free
Tbestavashvili
1 views

14:40
SECURITY ATTACKS || TYPES || ACTIVE || PASSIVE || OSI SECURITY ARCHITECTURE --NETWORK SECURITY
t v nagaraju Technical
35.3K views

31:47
Philippe Gaborit - RankSign: An Efficient Signature Algorithm Based on the Rank Metric
Institute for Quantum Computing
1.8K views

45:59
01731, Network Steganography / Network Information Hiding, Chapter 7a Network-level Countermeasures)
Steffen Wendzel
812 views

6:33
What Is Network Marketing Network Marketing Explained! What Is Network Marketing Anyways
Most Popular Videos
1 views

11:37
What is Pi Network | Pi Network in Pakistan | Pi Network kya Hai | Pi Cryptocurrency Review in urdu
90s Mentor
25 views

7:54
Network Marketing Nedir, Neden Network Marketing, Network Marketing Gerçeği
musaduman
3 views
0:35
Guess the Algorithm Behind CompTIA Security+ Quiz 33! #shorts #shortsfeed #cybersecurity #algorithm
LearnWithRookie
98 views

22:52
RSA Algorithm,Security,Attack_module3_part2(CST393) Cryptographic Algorithm
Binary Board
15 views

11:12
RSA Algorithm in Information Security | Public Key Cryptography: RSA Encryption Algorithm | RSA
Tech CS&IT
266 views
19:18
Console Locking and Symmetric Cryptography lab: Blowfish algorithm, AES Algorithm :Cyber Security
Satish Tiwary
66 views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views
7:14
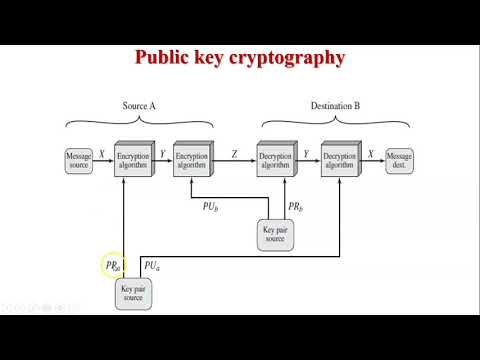
Application of public key cryptography | Authentication | Confidentiality | Digital Signature
Chirag Bhalodia
22.5K views

2:10
How to make Digital Signature | DSC Tutorial | Tutorial Tuesday Ep. 37
Labour Law Advisor
363.3K views

3:37
Digital Signature | Blockchain
Telusko
108.2K views

9:04
Message Digest and Digital Signature | Cryptographic Hash Function
saurabhschool
16.4K views
7:40
10.3 digital signature In Cloud Computing
BANSODE TECH SOLUTION
921 views

7:42
Digital Signature - Asymmetric Key , Why used for Authentication & Non Repudiation (Hindi)
Easy Engineering Classes
177.3K views

1:23
What Is A Digital Signature In Crypto? #crypto #blockchain #digitalsignature
Always Be Winning Crypto & Wealth
77 views

15:55
4.12 Elgammal Digital Signature Scheme in Tamil
BECAUSE
20.0K views
35:06
RSA Digital Signature - Public Key Cryptography + JAVA (Prototype Project 04)
Prototype Project
4.9K views
0:18
How to create a digital signature on an iPhone
TRCMEDIASTUDIES
237.9K views
33:55
Cryptography Lecture 20: Digital Signature, Formal Definition & Structure, Attack Goals
Maths Submarine
30 views

0:54
Essential Roles of Digital Signature Algorithms- History of Cryptography
QRL
152 views

22:00
Digital Signature in Cryptography in Bangla | ডিজিটাল সিগনেচার কি এবং কিভাবে কাজ করে?
content on demand
4.9K views

17:53
Post-Quantum Cryptography: Lattice based Digital Signature Scheme
Elucyda
3.1K views
24:32
C++ Builder - Hash functions, Symmetric + Asymmetric Cryptography, and Digital Signature (LockBox)
VCL Examples
3.1K views
Previous Page 3