Search Results for "anitta used to be"
Find videos related to your search query. Browse through our collection of videos matching "anitta used to be". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "anitta used to be"
50 results found

5:05
The Weeknd, Anitta - Sao Paulo (Live from Sao Paulo / 2024)
TheWeekndVEVO
14.5M views

3:44
Anitta - Goals (Official Music Video)
Anitta
25.2M views

4:04
Black Eyed Peas & Anitta - eXplosion (Official Music Video)
Black Eyed Peas
44.3M views

1:14
Shakira ovaciona Anitta no Billboard Latin Women in Music: 'Rainha do funk'
Billboard Brasil
275 views

12:17
Anitta Breaks Down Her Most Iconic Music Videos
Allure Magazine
341 views

1:59
MC Daniel faz convite especial à Anitta: 'Dinda do ano'
Banda B
515 views

1:12
Anitta faz história e leva funk brasileiro para o palco de premiação internacional
Terra Brasil
3.9K views

7:43
Ensaios da Anitta em Curitiba: cantora fala sobre Carnaval, novo álbum e revela que já realizou todos os sonhos profissionais
Banda B
230 views

3:56
What is Python Used For?
Treehouse
346.0K views
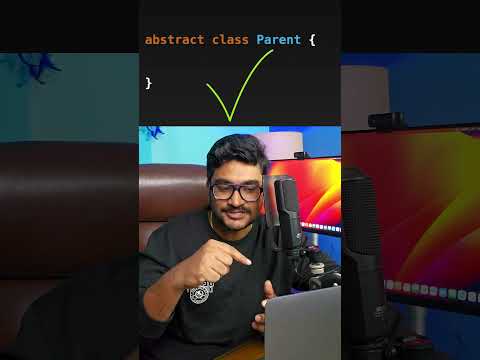
1:00
Java Interview Short 8 - why abstract class is used - No Abstract method use-case | #javainterview
Selenium Express
148.4K views
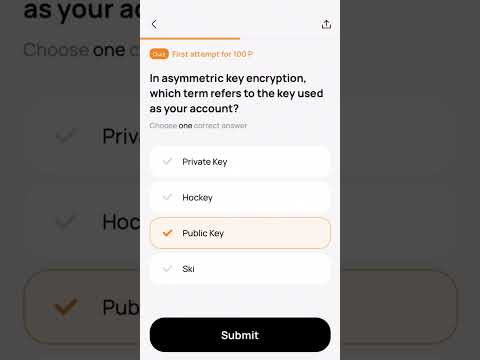
0:10
In asymmetric key encryption, which term refers to the key used as your account?
10 Minutes Crypto
4.1K views

11:19
Rounding and Order of Operations Used in Significant Figures
Melissa Maribel
122.5K views

12:02
Why the Imperial Military Used Outdated Tactics
Generation Tech
274.4K views
0:15
“If Afghan Soil Is Used for Terrorism, We’ll Respond Forcefully” — Khawaja Asif | Breaking News
Geo News
24.1K views

3:45
2 Gang Switch Used as 1 Way Switches Connections Explained - Taking the Feed to the Switch
GSH Electrical
207.5K views
1:56
She used chicks to paint? Auction crowd went crazy!#shorts #drama #cdrama #kdrama #foryou #funny
Jerry Movies
264.6K views

1:00:27
Tools and Methods Used in Cybercrime Part 4 | Dr. Reshma Kadam
Reshma Patil
309 views

3:12
Is Quantum Machine Learning Used in Cryptography Today? - Quantum Tech Explained
Quantum Tech Explained
5 views

2:29
Spike in demand for South Korean used cars in Russia and Middle East | Asia News Week | ABC News
ABC News (Australia)
64.5K views

41:22
Child Discipline Isn't What It Used To Be. Fred Klett - Full Special
Dry Bar Comedy
6.6M views

3:08
What is cryptography used for in crypto?
Luno
1.8K views

1:48
What is a Prime Number? What Are Prime Numbers Used For?
Eye on Tech
98.4K views

0:17
Maruti Zen 🚗 | Used Car Price, Mileage & Review 2025 | Sri Sairam Cars, Gopi #car #shortsfeed
Engine Thagaval
283.4K views

0:16
I Used Superpowers To Save 10 Animals! 🤯#animalrescue #globaltrends #savinglives
Oscar's Sandbox
749 views

58:40
CTF : Steganography | Forensics Challenges - Tools to be used - Walkthrough - English
Tech Enn
10.4K views

0:27
Evaluate the history of cryptography from its origins Analyze how cryptography was used
ESSAYA ORG
0 views
0:11
Which protocol is used to securely transfer files over the internet?
KrofekSecurity
38 views

13:51
what is MAC? why is it used? Applied Cryptography
Rands
159 views

30:14
The Most Destructive Hack Ever Used: NotPetya
Cybernews
3.7M views

0:15
Trying lipstick from Morocco - Aker Fassi 🇲🇦 I used a little too much water…looked like🩸
Erin Parsons Makeup
63.4M views

3:51
What is cryptography? | Main Algorithm used | daily usages | Doorbell DD
The Digital King
1.2K views

3:43
How To Buy A Used ATV
Dirt Trax TV
484.5K views

7:42
Digital Signature - Asymmetric Key , Why used for Authentication & Non Repudiation (Hindi)
Easy Engineering Classes
177.3K views

4:28
How Is Steganography Used In Cybersecurity? - SecurityFirstCorp.com
SecurityFirstCorp
9 views

0:17
Used Maruti Suzuki Omni car for sale # #carforsale
Faizal's View
61.0K views

32:44
JNTUK R16 III CSE SEM2 CYBER SECURITY UNIT 4 INTRODUCTION TO TOOLS & METHODS USED IN CYBER CRIME LEC
RVIT — Autonomous, Guntur
1.8K views

2:47
How Are Qubits Used in Quantum Cryptography? | Quantum Tech Explained News
Quantum Tech Explained
32 views

12:11
They don’t make ‘em like they used to (and they shouldn’t)
The Grumps
306.1K views
4:21
How Is The Vigenere Cipher Used In Cryptography? - SecurityFirstCorp.com
SecurityFirstCorp
9 views

5:05
Intelligence Agencies Used Sports Propaganda in US vs USSR Cold War
D.A.T.A Productions Media
321 views
3:00
How Russia used language to justify its war in Donbas
Kyiv Independent
51.1K views

0:41
Top Secret Encryption Systems Used by Presidents, Diplomats, and VIPs | Unbreakable Security
CRYGMA.COM Encryption
48 views
0:32
EASIEST FX Trading Strategy I’ve ever used (ORB)
Trade with Pat
55.8K views

3:07
Used car demand and prices skyrocketing across the country
FOX 29 Philadelphia
1.5K views

0:56
How I Used $0 to Create 1000+ Videos on Autopilot With This AI Agent System (No Paid API Needed)
Andy Lo
293.3K views

7:23
Cryptography Part 19 :- Algorithms used for generating Pseudorandom Numbers
Tech Lover
286 views

4:37
When Is Steganography Used? - SecurityFirstCorp.com
SecurityFirstCorp
2 views

0:05
What python can do? What python is used for? #coding #python #programming | Developer Shaurya
Developer Shaurya
45.9K views
7:14
Why XOR is used everywhere in Cryptography?
DG
605 views

52:55
Tools and Methods Used in Cybercrime Part 2 | Dr. Reshma Kadam
Reshma Patil
826 views