Search Results for "Secure Key Generation"
Find videos related to your search query. Browse through our collection of videos matching "Secure Key Generation". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Secure Key Generation"
51 results found

15:44
Public Key Distribution in Cryptography | Public Key Distribution | Key Distribution
Chirag Bhalodia
57.3K views

7:56
Key Distribution in Asymmetric Key |Asymmetric key distribution |Network Security Hindi explain
DK Technical Point 2.0
1.1K views

38:43
Public Key Cryptography | Asymmetric Key Cryptography | Components of Public Key Cryptography
Dr. Majid Khan Mathematics Waley
343 views

29:00
Asymmetric Key Encryption (Private key vs public key encryption)
iq pop
48 views

22:19
MODULE 3- Use of key hierarchy, Key distribution scenario, Hierarchial key control.
SAVI
2.9K views

4:09
public key applications in urdu hindi | public key applications lecture | public key tutorial | p 41
IT Expert Rai Jazib
121 views

26:05
symmetric key distribution || urdu hindi | symmetric key distribution lecture |symmetric key |part38
IT Expert Rai Jazib
2.4K views

2:56
Encryption key cryptography type(symmetric key cryptography & asymmetric key cryptography) in HINDI
Shukla Classes
40 views

3:18
Difference Between Key Size, Key Length, and Key Space - CISSP
CISSPrep
2.8K views

6:43
Network & Cyber Security Lecture: Symmetric key Encryption (Private Key) Key Based Cryptography
Sanjay Pathak
1.8K views

5:34
Public-Key Certificate and Public-Key Infrastructure (PKI) - Asymmetric Cryptography and Key
Ton Ha Nhi
11 views
1:05
Windows 8 KEYGEN (activation key,serial key,key generator)
Sornililio
5 views

0:32
PES 14 Serial Key (Key Generator for PC)CD Key
ppsee2014
2 views

0:28
FIFA 14 Serial Key (Key Generator for PC)CD Key
utikjholh
76 views

0:30
FIFA 14 Serial Key (Key Generator for PC)CD Key
jassja
18 views
0:28
FIFA 14 CD Key (Key Generator for PC)Serial Key
jsar
41 views
![Key Remapper Key Gen [key remapper windows]](/image/s1.dmcdn.net/v/8wPMm1e0Gum_TF5WY/x720)
1:35
Key Remapper Key Gen [key remapper windows]
Jeff Butler
47 views

0:06
Download Investigating Psychology: key concepts key studies key approaches PDF Free
Kiriaki Reme
9 views

4:20
What is PUBLIC-KEY CRYPTOGRAPHY? WHat does PUBLIC-KEY CRYPTOGRAPHY mean? PUBLIC-KEY CRYPTOGRAPHY meaning & explanation
The Audiopedia
1 views

11:18
Symmetric Key Cryptography VS Asymmetric Key Cryptography | Private vs Public Key Cryptography
Simple Snippets
8.7K views

1:00
Key Management Systems, Key Box - Key Tracer
Keytracer
1 views

1:02
Windows 7 key, office key, norton key from www.keyyeah.com
neriosamed
370 views

18:04
Symmetric Key and Public Key Encryption | Public key Encryption hindi urdu (IT430)
theITeducation.com
897 views
19:53
Understanding Asymmetric Encryption: The Key to Secure Communication
Visualize Byte Code
9 views
2:36
Provably Secure Three-Party Authenticated Quantum Key Distribution Protocols
projectsnine
861 views

30:43
Swift 4: RSA Asymmetric Public Key Encryption - Secure Your iOS 11 App. How to in Xcode 9!
Swift Almanac
7.6K views
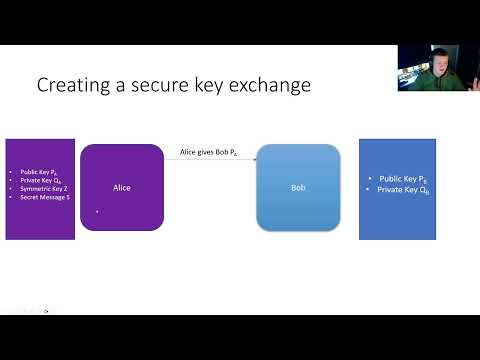
15:54
Cryptography #3 - Asymmetric encryption & a secure key exchange
Ben Folland
28 views

3:22
How to Secure App-Level Encryption Keys with Unbound Key Control (UKC) via REST API
Unbound Security
564 views

20:10
Saber on ARM: CCA secure module lattice based key encapsulation on ARM
IACR
327 views

4:50
Compact and Tightly Selective-Opening Secure Public-key Encryption Schemes
IACR
66 views

5:58
Module 4.9. Distribution of Secret Keys Using Public-Key Cryptography|S8 ECE | SECURE COMMUNICATION
bushara abdulrahim
2.6K views

3:36
Module 4.3 Requirements of Public key cryptosystems|S8 ECE|SECURE COMMUNICATION KTU|ECT434
bushara abdulrahim
2.4K views

6:11
Understanding RSA Algorithm: The Key to Secure Communication
securityconceptsnotes
55 views

0:15
Quantum Cryptography: Unbreakable Encryption and Secure Key Distribution 🔒🔑
Dev Job Seekers
543 views

11:35
Module 4.1 Public key cryptosystems|S8 ECE|SECURE COMMUNICATION KTU|ECT434#engineering #ktutuition
bushara abdulrahim
4.5K views

0:41
🔐 IKE Authentication Explained Secure Cisco VPN | IPsec & Pre Shared Key Step by Step #ccnpsecurity
CoreSah Networks
212 views

0:40
RSA: Secure Key to Modern Cybersecurity #cybersecurity #cryptography #cybersecurityeducation
SimplyCompute
142 views

3:01
Why Is Public-key Cryptography Crucial For Secure Communication? - Emerging Tech Insider
Emerging Tech Insider
0 views

16:06
Quantum Key Distribution (QKD) Explained: Secure Communication Redefined
Encryption Consulting LLC
8.7K views

21:58
Diffie-Hellman Key Exchange Explained – The Foundation of Secure Communication - 041824A01
Back From The Ether
23 views

2:46
What Is Symmetric-key Encryption And How Does It Secure Data? - Emerging Tech Insider
Emerging Tech Insider
1 views

9:04
Secure System & Symmetric key Cryptography
Network Security Wallah
188 views

21:34
Quantum Secure Symmetric Key Cryptography Based on Hidden Shifts
IACR
257 views

23:36
22-PGP(Pretty Good Privacy) Explained | E-mail Security | Secure Email Using Public Key Cryptography
Sundeep Saradhi Kanthety
224.4K views
6:27
🔐 Public-Key Encryption: Unlocking Secure Communication @DatabasePodcasts
Database Podcasts
13 views

3:57
Module 4.2 Applications of Public key cryptosystems|S8 ECE|SECURE COMMUNICATION KTU|ECT434
bushara abdulrahim
2.6K views

1:53
Secure API Keys with a Public-Key Cryptography on Android (Online Course)
Stevdza-San
3.6K views
0:31
Unlock Secure Communication: The Power of Diffie-Hellman Key Exchange
Red Boot LLC
532 views

1:15
Quantum Key Distribution: The Foundation of Secure Quantum Channels
RealityRip
68 views

1:00:34
Cliff Cocks - Public Key Cryptography: How numbers secure the internet
G-Research
974 views

0:48
Elon Musk: Filtronic secures $62.5m order with SpaceX for next generation technology
Yorkshire Post
900 views