Search Results for "Secure Hash Algorithm 256"
Find videos related to your search query. Browse through our collection of videos matching "Secure Hash Algorithm 256". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Secure Hash Algorithm 256"
50 results found

2:05
Secure USB Flash Drive - SanDisk Enterprise Secure ...
John Objet
1 views

4:53
Best browser for privacy 2021 | Iridium Browser | A browser securing your privacy | Most Secure Web Browsers That Protect Your Privacy | most secure browser 2021
FOCUS EXCLUSIVE
13 views

46:18
Roll Your Own Secure Cloud Storage with SSHFS - Secure Shell File System - Hak5
Hak5
5 views

3:39
Medical Coding Services | Secure Medical Coding & Secure Medical Data Handling
PDNSeek .com
5 views

0:25
A Secure Erasure Code-Based Cloud Storage System with Secure Data Forwarding
satish20059
259 views
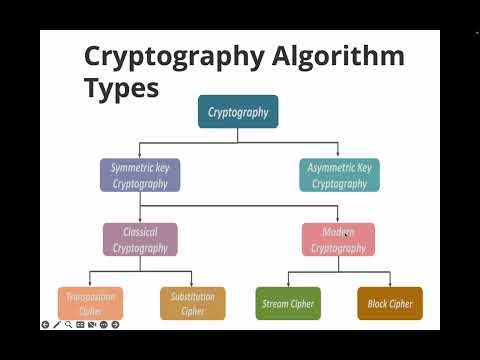
10:49
what is hash function, types of cryptography algorithm in details notes
sawji gyaan
11 views

8:02
hashing Algorithm? password hashing? password and hash function Hindi
Technical Haroon
21.9K views
0:40
What is Hash Algorithm? #nonacademy #web3 #blockchain
NonAcademy
211 views
![[Bangla] Beginner To Advance CTF #DAY-13 -MD5 Algorithm | Solve MD5 Hash Via Python |](/image/i.ytimg.com/vi/qG8T1_Aawrk/hqdefault.jpg)
6:35
[Bangla] Beginner To Advance CTF #DAY-13 -MD5 Algorithm | Solve MD5 Hash Via Python |
InfoSec BD
2.6K views
0:13
Cyber Security Which cryptographic hashing algorithm produces the hash of 512 bits in length
QuizApp learn programming quiz C C++ Python Java
89 views
20:58
16-HMAC Algorithm Explained 🔐 | Hash-Based Message Authentication Code in Network Security
Sundeep Saradhi Kanthety
168.4K views

0:54
Rabin karp Rolling Hash Algorithm and Birthday paradox (with cryptography)
Purrfectly Curious
93 views
4:06
RSA ALGORITHM AND HASH LSB TECHNIQUE FOR IMAGE STEGANOGRAPHY
VERILOG COURSE TEAM-MATLAB PROJECT
497 views
5:36
Cryptography CTF: Decrypting Cipher Text with Rotation and Substitution | Hash Algorithm - 2024
Tshepho
151 views

2:17
A Lightweight Image Encryption Algorithm Based on Secure Key Generation
Takeoff Edu Group
229 views

7:49
Hybrid Algorithm for secure data over Cloud OS
Avin Pasupuleti
1.4K views

13:45
Secure Binary Image Steganography Using F5 algorithm Based on Data Hiding and Diffusion techniques
Jitendra Singh
954 views

6:11
Understanding RSA Algorithm: The Key to Secure Communication
securityconceptsnotes
55 views

3:42
Hybrid Cryptography Algorithm For Secure And Low Cost Communication | IEEE Major Projects | B-Tech
Cloud Technologies
65 views
10:21
SHA: Secure Hashing Algorithm - Computerphile
Computerphile
1.3M views
6:09
AES ALGORITHM BASED SECURE DISCRETE WAVELET TRANSFORM STEGANOGRAPHIC TECHNIQUE FOR THE IMAGES
VERILOG COURSE TEAM
739 views
8:55
Final Year Projects | Secure Data Hiding Algorithm using Encrypted Screte Message
ClickMyProject
2.3K views
5:24
Final Year Projects | A Secure Image Based Steganographic Model Using RSA Algorithm and LSB I
ClickMyProject
7.0K views

3:08
Secure File Storage in Cloud Computing Using Hybrid Cryptography Algorithm, aws cloud technologies
Tech Channel 2
53 views

0:31
Crypto Quiz Challenge: Guess the Guardian! Discover the Web's Secure Sentinel Algorithm! 🚀🔒
CodingQuizzy
6 views

7:51
Highly Secure Image Steganography Algorithm using Curvelet Transform and DCT Encryption
MyProjectBazaar
394 views
9:58
Secure File Storage Using Hybrid Cryptography Algorithm
Shubham Singh
2.2K views
7:49
Highly Secure Image Steganography Algorithm using Curvelet Transform and DCT Encryption
ClickMyProject
1.0K views

1:37
Oracle to Secure TikTok's Algorithm in Trump-Backed Deal
Bloomberg
0 views
18:59
An Advanced Cryptography Algorithm For Secure File Access In Cloud
Devi Devika
636 views
3:29
Secure File Storage in Cloud Computing Using Hybrid Cryptography Algorithm,hybrid cloud networking
Rahul Technology
26 views
3:09
Secure File Storage in Cloud Computing Using Hybrid Cryptography Algorithm,hybrid cloud networking
Facts To Sleep
20 views
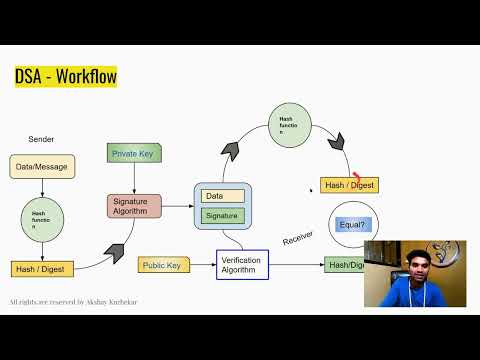
25:20
Asymmetric Key Cryptography & Hashing Explained | RSA, DSA, SHA-256 in Blockchain Part 03 Hindi 2025
Akshay Kurhekar
116 views

6:17
Bitcoin & SHA-256 Explained With Animations
I Explain Crypto
1.1K views

0:11
IPHONE 11 PRO MAX 256 NIGHT GREEN | THE BEST IPHONE YOU CAN BUY | IAMLIKA LI
IAMLIKA LI
694.9K views

28:38
#ክሪፕቶግራፊ How Blockchain Uses SHA-256 for Cryptographic Hashing | Simplified in Amharic
Self Programmers
268 views
1:00
Exploring Cryptography: SHA-256 to Blake3 Transition
Stephen Blum
264 views
0:16
Decrypt Files Instantly with AES-256 🔓 | Python Decryption Tool | Cybersecurity Project
Esraa Codes
1.9K views

32:34
SHA-256 (COMPLETE CONCEPT & DETAILED STEP-BY-STEP EXPLANATION)
Xiuminseokie21
21.7K views

0:57
SHA-256: The Ultimate Weapon Against Hackers – Here’s Why! #sha256 #cybersecurity #programming
Code
2.2K views

1:00
₿ BITCOIN verschlüsselung SHA256 wie gross ist 2 hoch 256 genau?
BtcBrienz
131 views

22:56
Design of a Lightweight Stream Cipher: BOKHARI 256
IJERT
20 views

2:14
Bitcoin Security Explained: The Role of SHA-256 #sha256 #bitcoin #cryptocurrency
Cryptocurrency Guide
39 views

3:10
Omega 256 - This Year (Official Video)
Omega 256
2.6M views
3:21
How to Password Protect a folder in Windows AES-256 Encryption
ourhometech
1.5K views
4:57
Explication de SHA-256 🔑 Blockchain : enjeux et mécanismes cryptographiques
MOOC de l'IMT
5.3K views

0:18
female possess,mindcontrol,hypno,brainwash 256
female possess, mindcontrol, hypnosis, brainwash
7.8K views

0:46
Unlocking SHA-256: The Hunt for the Special Number
Tech Chips
10.8K views
14:04
Cryptography with Python 22: Implementing a P-256 ECDHE in Python
Cyrill Gössi
1.7K views
22:59
How Does SHA-256 Work?
learnmeabitcoin
362.6K views