Search Results for "Phases of a compiler example"
Find videos related to your search query. Browse through our collection of videos matching "Phases of a compiler example". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Phases of a compiler example"
53 results found

12:58
RSA Algorithm with Example | Asymmetric Key Cryptography (Public Key Cryptography)
Simple Snippets
26.4K views
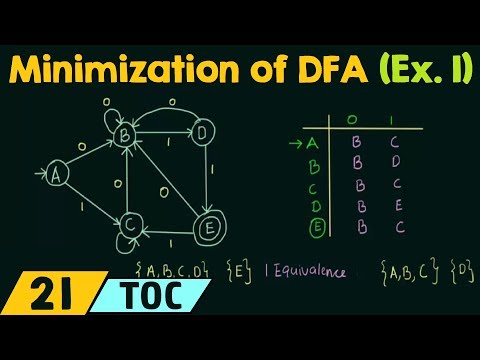
15:56
Minimization of DFA (Example 1)
Neso Academy
2.0M views

3:45
RSA Asymmetric Encryption and Signing with Public Private Keys - Usecases with Example
Techno Saviour
4.7K views

12:59
Caesar Cipher Encryption and Decryption with Solved Example || Substitution Technique
A Z Computing
37.3K views

13:10
Logistic Regression Algorithm in Machine Learning with Solved Numerical Example by Mahesh Huddar
Mahesh Huddar
172.7K views

7:04
Theory OF Computing | Nfa to Dfa Conversion Example 2
BD Top Education
74 views
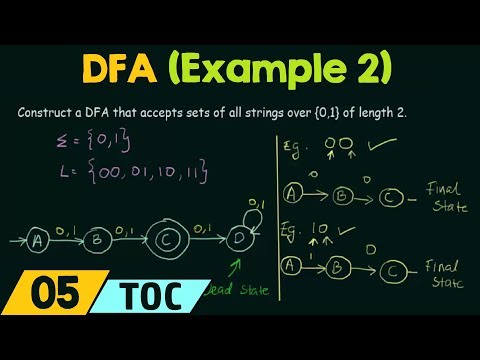
11:21
Deterministic Finite Automata (Example 2)
Neso Academy
1.4M views

11:42
2. Hill Cipher Solved Example 3x3 Key Matrix | Hill Cipher Encryption and Decryption Mahesh Huddar
Mahesh Huddar
27.0K views

2:20
Vigenere cipher|Vigenere cipher encryption and decryption|Vigenere cipher example
Atiya Kazi
684 views

10:05
RSA Example Lecture 1 | p=7, q=11, plaintext=m=9, Find public key (e), private key (d) & ciphertext
TRN CSE Tutorials
2.2K views

6:27
Regular Languages Closed Under Suffix Example
Easy Theory
934 views

44:01
Simplified Data Encryption Standard (DES) Example
Steven Gordon
74.5K views

13:04
Palindrome using Turing Machines | Problems on Turing Machines|Example 5| Theory of Computer Science
Sridhar Iyer
1.8K views

4:23
Affine Cipher Example Cryptanalysis of Monoalphabetic cipher ~xRay Pixy
Ritika xRay Pixy
2.3K views
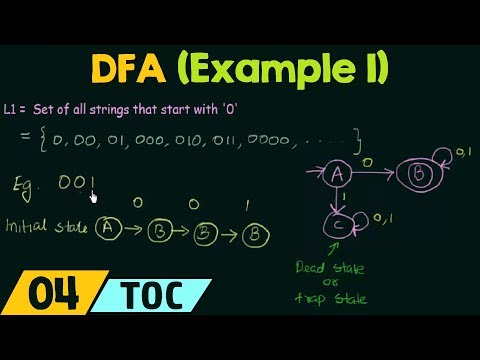
9:48
Deterministic Finite Automata (Example 1)
Neso Academy
2.2M views

14:40
Knapsack Algorithm in Cryptography and Network Security with example
Lab Mug
3.8K views

7:05
Non-Deterministic Finite Automata (Solved Example 1)
Neso Academy
965.0K views

0:34
Write the Mixed Number as a Decimal Example with 5 and 3/10 #shorts
The Math Sorcerer
36.2K views

18:24
RSA ALGORITHM || SECURITY || EXAMPLE || PUBLIC KEY CRYPTOGRAPHY || ASYMMETRIC KEY CRYPTOGRAPHY
t v nagaraju Technical
54.1K views
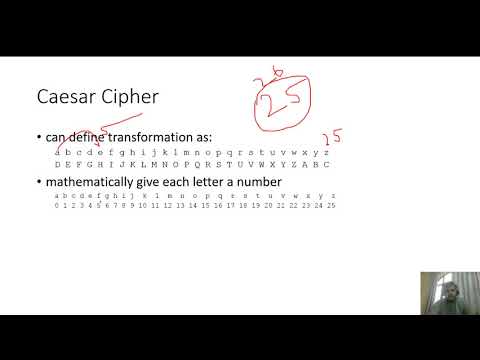
9:43
Caesar Cipher Explained with Solved Example|lec 3|urdu|hindi
ITphile
379 views
8:40
The RSA Encryption Algorithm (1 of 2: Computing an Example)
Eddie Woo
1.2M views

7:56
What is html in hindi ||bilkul basic se html in hindi || full define html with example | part-1
Corporate Wallah
307 views

14:45
Application of Linear Algebra: Encoding and Decoding with Example #encryption #decryption
EE-Vibes (Electrical Engineering Lessons)
7.4K views

2:49
Turing machine example
Himmat Yadav
68.5K views
4:27
Cryptography Project Example
Elizabeth Swanson
609 views

1:00
What is the Twin Paradox Example🤔 Neil deGrasse Tyson explained #science #physics #universe
Sci Explained
17.7M views
17:40
Theory of Computation (TOC) Video 15 : Turing Machine Example 1
VITS GATE COACHING By VITTHAL GUTTE
185 views

5:19
Number Theory | Chinese Remainder Theorem: Example 1
Michael Penn
27.2K views
14:46
Network Security - RSA Algorithm with example
Lectures by Shreedarshan K
1.4K views

1:01
KNN Algorithm Machine Learning Explained in 1 Minute| How KNN works with Example #shorts #shortsfeed
Data University
19.1K views

7:26
NFA Example | Part-1/3 | TOC | Lec-14 | Bhanu Priya
Education 4u
234.8K views

13:13
Converting CFG to CNF | Example | TOC | Lec-71 | Bhanu Priya
Education 4u
780.6K views

13:37
#32 Knapsack Algorithm with Example- Asymmetric key cryptography |CNS|
Trouble- Free
96.3K views

10:18
Accounting Rate of Return (ARR) | Explained with Example
Counttuts
108.0K views
21:12
DFA Minimization Algorithm + Example
Easy Theory
30.0K views

10:12
#34 MD5 Algorithm ( Message Digest 5) Working and Example |CNS|
Trouble- Free
416.8K views

4:39
java rsa encryption decryption example
CodeFix
7 views
0:16
SQL Server Password-Based Encryption & Decryption | Symmetric Key Example #csharp #shorts #sqlserver
Coding Corridor
15 views

5:49
RSA ALGORITHM EXAMPLE 03 | CRYPTOGRAPHY | MACS | BANGLA TUTORIAL
Tanver Likhon
653 views

5:17
RSA Algorithm Example |Cryptography
Last Night Study
39.5K views

18:21
Chinese Remainder Theorem - 2 (Solve Example) Cryptography and Network security in Hindi.
Helping Tutorials
85.1K views
4:25
DFA Example: L ={0 ^ odd Value } | L = {a^3k} | TOC
EduStream
11 views
18:28
Cryptography Lect.-03: Vigenere Cipher and Auto Key Generation with Example (In Hindi)
P Kalika Maths
916 views

17:53
RSA Algorithm in Network Security with Solved Example
A Z Computing
28.0K views

7:13
Proofs in Cryptography Lecture 14 ROM Construction Example RSA FDH Signatures
Science Traveller
217 views

1:42:00
Webinar-2 on "Perceptron Learning in Artificial Neural Network With real time example"
PESMCOE YouTubeChannel
152 views
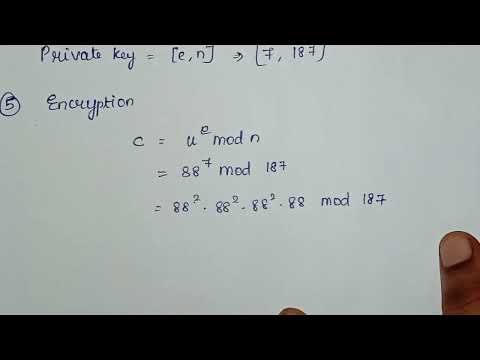
9:57
RSA Algorithm Example 1 Unit 3 Cryptography Anna University
My Study Hour
2.5K views

20:16
Vigenere Cipher - Explained with an Example - Cryptography - Cyber Security - CSE4003
Satish C J
20.7K views
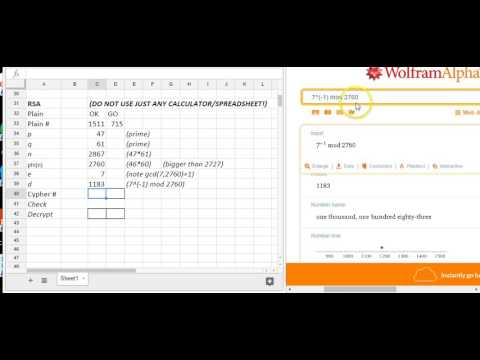
6:10
RSA Encryption/Decryption Example
David Metzler
62.3K views

7:10
Sqare root test example for Primality test in Cryptography
CSE concepts with Parinita
15.3K views

3:02
‘This Is A Five-Alarm Fire’: Ilhan Omar Lists Example After Example Of Trump’s ‘Fascist Takeover’
Forbes Breaking News
2.6K views

1:29
NMC calls China’s ‘seizure’ of Sandy Cay a ‘clear example of disinformation’
Manila Bulletin
251 views

0:51
Example of a clandestine laboratory | September 13, 2024 | Illawarra Mercury
Illawarra Mercury
2.1K views