Search Results for "One-Way Authentication for Email"
Find videos related to your search query. Browse through our collection of videos matching "One-Way Authentication for Email". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "One-Way Authentication for Email"
50 results found

12:55
Types of Message Authentication | Message Encryption | Part 1 | Network Security | Hindi Urdu
Ask Faizan
4.3K views

12:48
How Kerberos Authentication Works and Why You Should Use It Detailed Explanation in Telugu
Lucky Tech
7.7K views
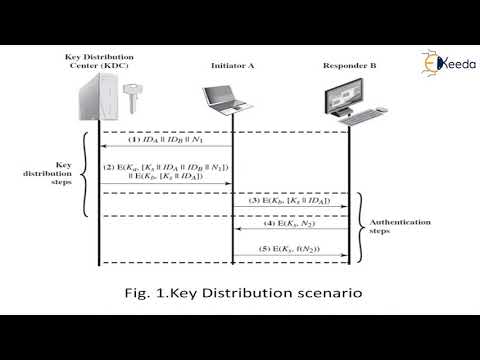
19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

7:01
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
Trouble- Free
304.6K views
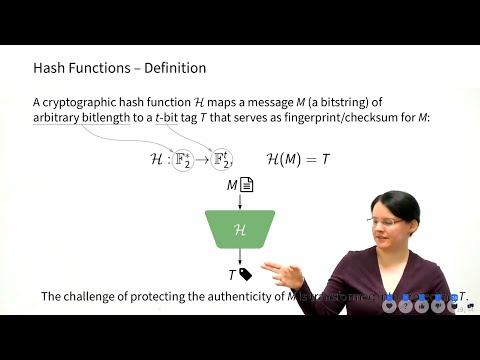
2:16:38
InfoSec L1 - Crypto 1 - Authentication
Maria Eichlseder
4.9K views

0:09
What is Authentication? #cybersecurity #learn #terms #cyber #security #tech
IT and Cyber Security Definitions
750 views

6:23
Secrecy and Authentication using Public-Key/Two-Key Cryptography or Asymmetric Encryption
CSE Adil
86 views

0:26
EKE Authentication - Applied Cryptography
Udacity
1.4K views

7:42
Digital Signature - Asymmetric Key , Why used for Authentication & Non Repudiation (Hindi)
Easy Engineering Classes
177.3K views

8:08
MAC in Hindi - Message Authentication Code Process, Significance, HMAC Concept
Easy Engineering Classes
111.9K views

16:52
Kerberos Authentication Explained | A deep dive
Destination Certification
424.5K views

11:28
Kerberos Version 4 | Kerberos Version 4 using Authentication and Ticket Granting Server
Chirag Bhalodia
27.4K views

4:49
Kerberos Authentication Protocol | Cryptography and System Security
Ekeeda
56 views

10:28
Module 5.2 Message Authentication Functions
bushara abdulrahim
2.9K views

20:53
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views

31:30
AUTHENTICATION REQUIREMENTS_FUNCTIONS_MAC_HASH FUNCTION
IN TECH
333 views
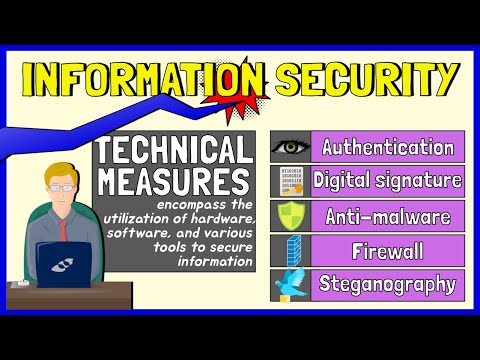
14:09
Information Security Measures (Authentication, Digital Signature, Firewalls, Steganography)
5-Minute Lessons by Victor
973 views

1:01
What is Kerberos ? #cissptraining #cissp #cybersecurity #authentication #itsecurity #securityconcep
IT Tech Insights
5.6K views

0:44
Kerberos Authentication Explained | How Login Tickets Work in Enterprise Security #CISSPFlashcards
Cyber Security Learning
3.2K views

0:49
Message authentication code (MAC)
Real programming
693 views

5:01
Fix the Authentication Required Problem in Netbeans
ULTIMΔTE DOT
19.3K views

7:13
MACs Message Authentication Codes in Network Security
Cihangir Tezcan
145 views
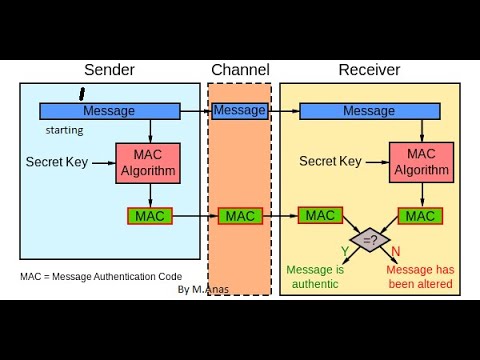
20:53
MAC in Cryptography || Message Authentication Code in Network Security And Cryptography.
Anas Khan
192 views
1:05
Fast Authentication using Chameleon Hashing Key Chain
University of Glasgow Singapore
229 views

1:00:51
CNIT 141: 12. Message Authentication Codes (MACs) and 13. Key Establishment
Sam Bowne
136 views

14:12
Kerberos Authentication
Mervin Pearce
57.5K views

10:48
Module 5.3_Message Authentication Code,Secure communication ktu s8 ec #engineering #ktutuition
bushara abdulrahim
2.3K views
20:25
INS: Unit-9 Remote User-Authentication (Kerberos)
Twinkal Patel
423 views

0:09
#cybersecurity#engineer#cs#cryptography#networking#authentication#securitybreach#shorts#cs#engineer
Laugh_infinity
61 views

12:54
Authentication Functions | Cryptography and Network Security
Ekeeda
910 views

6:26
Types of Message Authentication | MAC | Part 2 | Network Security | Hindi Urdu
Ask Faizan
1.9K views
1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views
2:20
Hash Based Message Authentication
Udacity
59.1K views
16:37
Message Authentication using Hash Functions - Network Security
Lectures by Shreedarshan K
4.3K views

11:14
Authentication Methods - SY0-601 CompTIA Security+ : 2.4
Professor Messer
136.2K views

18:07
Lecture 23: Public key cryptography and authentication method Asymmetric Key Requirements
QZ Historia
41 views

0:20
What is Biometric Authentication? #Cybersecurity #TechEducation #onlinelearning #definitions #short
Keerthan V Suvarna
38 views

0:41
🔐 IKE Authentication Explained Secure Cisco VPN | IPsec & Pre Shared Key Step by Step #ccnpsecurity
CoreSah Networks
212 views

14:13
Chapter 12 - Message Authentication Codes
j neama
1.9K views

6:35
Kerberos - Network Authentication Protocol explained in hindi || Working ,History ,AS ,TGS and AP
Unbeaten Learning
112.9K views

1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views

13:19
18_Public Key Cryptography - Key pair, Secrecy and Authentication
Angayarkanni S A
238 views

2:24
Network Security and Cryptography: Message Authentication Code(MAC)
OnlineTeacher
598 views
1:04:18
Assumptions of Encryption and Authentication (ITS335, L04, Y15)
Steven Gordon
1.2K views

9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

13:16
Public Key vs Private Key | SSH Authentication | DevOps Realtime Interview Questions
DevOps and Cloud with Siva
12.4K views
13:23
Message Authentication Code (CO4: Session-7)
Cyber Security
47 views
8:51
A Secret-Sharing-Based Method for Authentication of Grayscale Document Images via the Use of the PNG
JP INFOTECH PROJECTS
1.6K views

1:19:10
Authentication with Symmetric Key Crypto and MACs (CSS322, L17, Y14)
Steven Gordon
1.5K views

4:33
Authentication fundamentals: The basics | Microsoft Entra ID
Microsoft Azure
253.3K views