Search Results for "Multi-Factor Authentication (MFA)"
Find videos related to your search query. Browse through our collection of videos matching "Multi-Factor Authentication (MFA)". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Multi-Factor Authentication (MFA)"
50 results found
1:06:48
Camp++ 0x7e2 // Modern cryptographic password and authentication methods by stf
Budapest Hackerspace
168 views
4:33
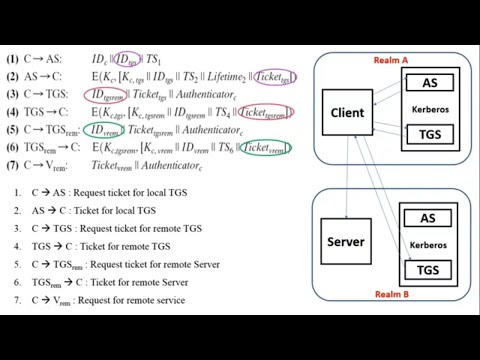
Kerberos Realm | Inter-realm authentication in kerberos Realm
Chirag Bhalodia
14.1K views

0:55
OSPF Authentication Types #ospf #ccna #ccnp #cybersecurity #networking #routingprotocol
IT INDEX
277 views

15:10
4.5 Message Authentication Code(MAC) Part 1 in Tamil
BECAUSE
21.3K views
14:06
Authentication Bangla tutorial 2 : encrypting database
Anisul Islam
5.3K views

22:09
PhotoProof: Cryptographic Image Authentication for Any Set of Permissible Transformations
IEEE Symposium on Security and Privacy
851 views
47:47
Cryptographic Binding Should Not Be Optional: A Formal-Methods Analysis of FIDO UAF Authentication
UCYBR - UMBC Center for Cybersecurity
99 views
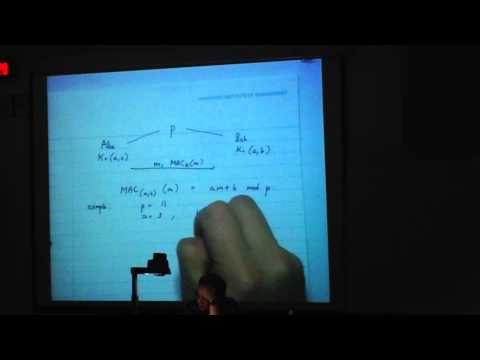
4:01
4. Message Authentication Code (MAC) Part 1
CSCI361 CSCI368
2.2K views

19:58
V4a: Message authentication codes: Fundamental concepts (Applied Cryptography 101)
Cryptography 101
736 views

28:10
Message Authentication Code (MAC)
Learn with Roy
232 views

43:20
CCT 074: Management of Identification and Authentication - Future Trends (CISSP Domain 5)
CISSP Cyber Training - Shon Gerber
13 views

8:32
Hashing Passwords | Node Authentication Tutorial – Part 3
Chris Courses
46.0K views

0:18
Critical Go Parser Vulnerabilities Enable Authentication Bypass and Data Theft in Production Systems
Secure Thread
122 views

6:51
E-Stamp Authentication using visual cryptography | Asp.net, C#.net, Final Year Project
Final Year Projects
412 views

28:39
Symmetric-key cryptography VII - Message authentication codes (MACs)
Tanja Lange: Cryptology
191 views

12:09
Lecture 22: Lecture 4 slides- Public key cryptography and authentication method
QZ Historia
42 views

18:43
Message Authentication Code -16
Cryptography
445 views

0:59
Passwordless Authentication Using a Combination of Cryptography, Steganography, and Biometrics
Journal Club
14 views

5:28
Module 5.1_ Message Authentication requirements
bushara abdulrahim
4.1K views
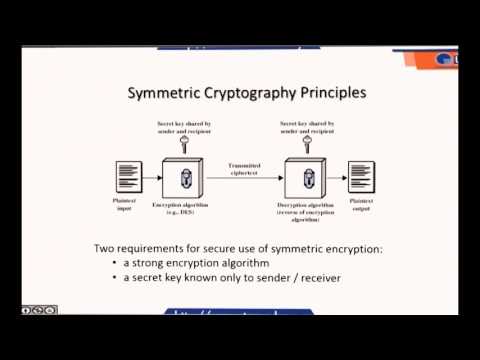
6:05
LECTURE 2- AUTHENTICATION AND BASIC CRYPTOGRAPHY (PART2)
UTeM MOOC
40 views

7:00
Authentication Header in IP Security #youtube #cryptography #ipsecurity #networksecurity #videos
Lab Mug
338 views

12:56
60 Multifold Secured Bank Application authentication service using Random Visual Cryptography and Mu
ICMISC
13 views

4:04
What Is A Message Authentication Code (MAC) In Go? - Emerging Tech Insider
Emerging Tech Insider
2 views
6:33
HMAC explained | keyed hash message authentication code
Jan Goebel
85.3K views

35:06
Authentication with Symmetric Key Encryption (CSS441, L16, Y15)
Steven Gordon
3.0K views

3:32
What Are Message Authentication Codes (MACs)? - SecurityFirstCorp.com
SecurityFirstCorp
5 views

16:07
Kerberos Authentication Server Version-4 by Rajendra Aaseri, Assistant Professor GBC Didwana
Govt. Bangur College, Didwana
76 views
![CS.167 (W'22), Lec 12 [2/10]: Message Authentication Codes (MACs)](/image/i.ytimg.com/vi/ncIIK_kIMhQ/hqdefault.jpg)
1:12:36
CS.167 (W'22), Lec 12 [2/10]: Message Authentication Codes (MACs)
Stanislaw Jarecki
156 views
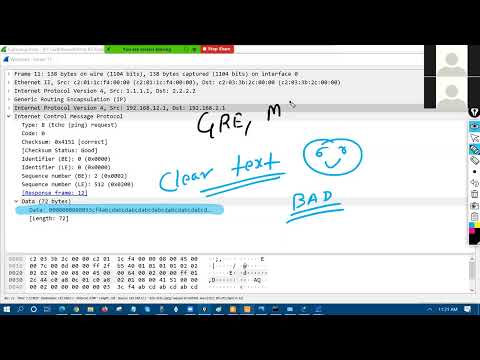
1:27:36
IPsec Day1 Authentication, Encryption, Confidentiality | Substitution Transposition Techniques
Law Sah
142 views
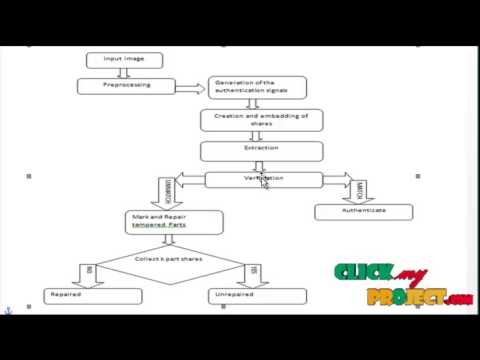
6:38
Final Year Projects | A Secret-Sharing-Based Method for Authentication of Grayscal
ClickMyProject
107 views
2:21
Distributed Programming Fullstack 2021 | S3P7 | Security | JWT Use Authentication schema package
Lars Bilde
135 views

2:31
MAC (message authentication code ) in cryptography network system
kysupportdev
7.0K views
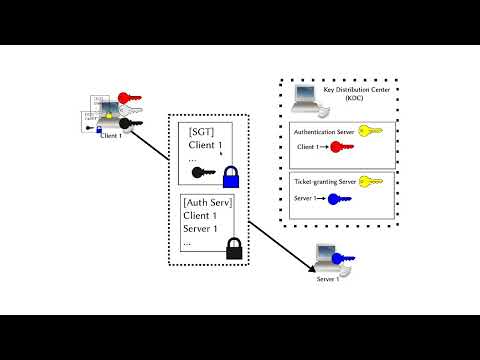
14:24
The Kerberos Authentication Protocol Explained
Suckless Programmer
306 views

1:35:00
Entity Authentication and Symmetric Key Establishment - Bart Preneel
secappdev.org
2.5K views

32:24
public key encryption: Key distribution, message Authentication and hash function- part1
Dr. Moonther
384 views
3:15
One Way Authentication ( SYMMETRIC VS ASYMMETRIC KEY)
TokTokTokTokDong
1.6K views
0:34
Public Key Authentication #remoteaccess #pki #sdntechforum #networksecurity #sshd
SDN TechForum
232 views

32:59
Message Integrity and Authentication in Cryptography (Bangla)
Jahidul Islam GUB
534 views
29:42
Message Authentication Code (MAC) and HMAC - Cryptography - Cyber Security CSE4003
Satish C J
37.3K views
14:41
MAC in Cryptography || Message Authentication Code in Cryptography and network security
Abhishek Sharma
396.9K views

6:43
Kerberos Authentication Protocol 🔥🔥
Perfect Computer Engineer
198.5K views

0:18
What is a MAC (Message Authentication Code)?
Intelligence Gateway
690 views

8:37
Remote user authentication using symmetric encryption
Anand Pashupatimath
4.6K views

4:27
Introduction to User Authentication - CompTIA Network+ N10-005: 5.3
Professor Messer
15.0K views

39:35
19-Learn Kerberos in Network Security 🔐 | How Kerberos Works? | Authentication Protocol Made Simple
Sundeep Saradhi Kanthety
184.1K views

11:16
Authentication Requirements | Cryptography and Network Security
Ekeeda
8.7K views

4:48
Message Encryption A type of authentication
Abisha D
292 views

14:23
Cybersecurity project on image authentication using visual cryptography.
Chaitanya sai
661 views

24:09
Passwordless Authentication Using Steganography, Cryptography And Biometrics - Tunde Oduguwa
BSides Bristol
39 views

12:55
INS: Unit: 6 Message Authentication Code(MAC)
Twinkal Patel
3.6K views