Search Results for "Key Explained"
Find videos related to your search query. Browse through our collection of videos matching "Key Explained". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Key Explained"
50 results found

20:52
How to Encrypt and Decrypt in Python (Symmetric Key And Asymmetric Key)
Halogenius Ideas
480 views

8:02
Diffie Hellman Key Exchange Algorithm | Key Agreement | Cryptography & Network Security |SKIT JAIPUR
CompAcademy
635 views

1:01
What’s the difference between a public key and a private key? #web3 #blockchain #crypto #nft
Dr. Brook Sheehan
484 views

10:05
RSA Example Lecture 1 | p=7, q=11, plaintext=m=9, Find public key (e), private key (d) & ciphertext
TRN CSE Tutorials
2.2K views
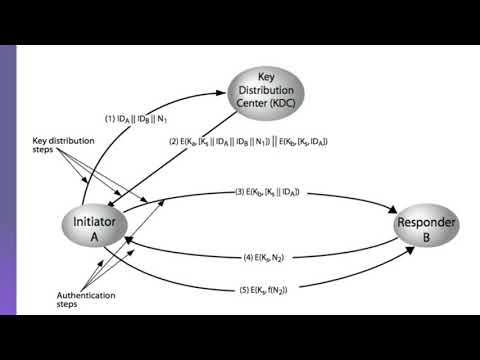
17:37
Key distribution in Cryptography | Key Hierarchy | Traffic Analysis
Computer Science Lectures
94 views

36:21
DES-Key Generation(64-BIT) "Cracking the Code" 🔓The Secrets of DES Key Generation"
The Builders
45 views

0:54
the difference between symmetric key cryptography and asymmetric key cryptography | IS | INS | CS
Pooja Patel
8 views

6:23
Secrecy and Authentication using Public-Key/Two-Key Cryptography or Asymmetric Encryption
CSE Adil
86 views

2:34:59
Encryption & Decryption Techniques for Symmetric Key Cryptography | Private Key Cryptography
Shiv Yog Classes
4 views

2:03
Difference between private key cryptography and public key cryptography
Note creation
39 views

18:24
RSA ALGORITHM || SECURITY || EXAMPLE || PUBLIC KEY CRYPTOGRAPHY || ASYMMETRIC KEY CRYPTOGRAPHY
t v nagaraju Technical
54.1K views

3:56
How to get cipher text | problem based on cipher text | Cryptography | Public key and Private key
Student Globe
205 views

6:06
#31 Key Distribution in Asymmetric key cryptography |CNS|
Trouble- Free
124.1K views
9:35
What is Asymmetric Key Cryptography | Elements of Asymmetric key cryptography | Asymmetric cipher
Chirag Bhalodia
9.0K views
1:08:41
Discussion on symmetric key and asymmetric key
Centre For Cyber Security SPUP
25 views

38:20
SSL/TLS Part-3 : SSL Handshake/Master Key/Session Key (Hindi)
Bhairave Maulekhi
1.7K views
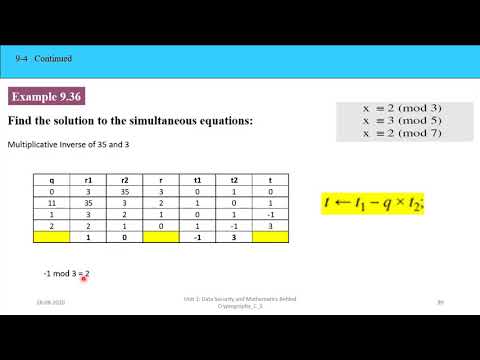
25:34
Review of Symmetric key and Asymmetric key cryptography
Kapil Gavali
92 views

2:12
ECC Elliptic Curve Cryptography Song (Asymmetric-key Algorithms) (Public-key Encryption)
Grannie Geek
17 views
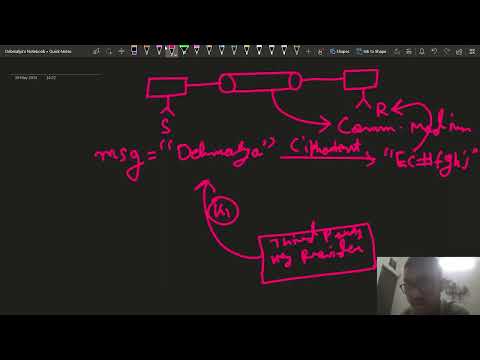
11:28
Symmetric Key & Asymmetric Key Cryptography
Let's Decode The CSE Fundamentals
118 views

4:23
1.3-Asymmetric key or public key cryptography(Hindi)
OVERNIGHT ENGINEERING
17 views

12:43
Lec-03:Asymmetric Key Or Public Key | CRYPTOGRAPHY AND NETWORK SECURITY
webSak
45 views

3:43
1.7-Key size in cryptography | Key Range || Hindi
OVERNIGHT ENGINEERING
2.2K views

39:48
The Math Club Ep10 - Key Ideas: Cryptography and the Diffie-Hellman Key Exchange
The Math Club Podcast
12 views

12:22
How to do Key Expansion in AES Algorithm Key Part 1
Raamaley tube
5.0K views

5:06
Public Key Encryption (Asymmetric Key Encryption)
Sunny Classroom
182.1K views

6:18
SUB KEY GENERATION IN DATA ENCRYPTION STANDARD TAMIL DES key generation cryptography
Dhanush Prabhu S
323 views

5:48
Introduction to Cryptography, Secret key algorithm, public key algorithm
Learning Computer Networks at Pallotti
7.2K views
2:14
How to Create Public Key and Private Key - Full Guide
Penrose Learning
0 views

6:34
Asymmetric Key: Public Key |Cyber Security |Encryption |Cryptography
Sanjay Pathak
1.3K views

6:42
What is symmetric key and asymmetric key.
Sabyasachi Pramanik
22 views

9:11
What Is Public Key & Private Key | Blockchain Demo Part 2 | Hindi
info nodearts
902 views

20:08
On the Wrong Key Randomisation and Key Equivalence Hypotheses in Matsui's Algorithm 2
IACR
267 views

2:56
Diffie Hellman Cryptography Song (Asymmetric-key Algorithms) (Public-key Encryption)
Grannie Geek
22 views

0:42
Public Key VS Private Key #shorts #shortsfeed
Moneyy Plant Capital Services
594 views

3:10
Public key Encryption (Asymmetric Key Encryption)
Myexamnote
40 views

20:08
Public key cryptography principles of public key cryptosystems
Ekeeda
407 views
11:12
controlling key usage, Symmetric key distribution using asymmetric encryption
Veera Veera
90 views

5:22
Network Security || Symmetric key Vs Asymmetric key Encryption
Tameshwar Sahu
71 views

20:12
Encryption in Python | Cryptography In Python | Symmetric-key and Asymmetric-key
IamPython
13.2K views

12:56
Key Range & Key Size
backbenchers academy (BBA)
5.8K views

6:05
Public-Key Cryptography | Two-Key Cryptography | Asymmetric Encryption
CSE Adil
7 views
55:00
Encryption, Key Management & PKI Key Lifecycle Management Webinar
Medcrypt
349 views

20:02
ELLIPTIC CURVE CRYPTOGRAPHY & DIFFIE HELMAN KEY EXCHANGE ||ASYMMETRIC KEY CRYPTOGRAPHY
t v nagaraju Technical
47.6K views

23:19
ECC - Why Is Public Key Secure? How Do We Determine Public Key? How We Encrypt?
Bill Buchanan OBE
1.1K views
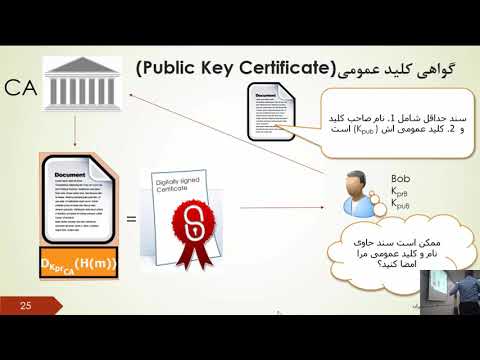
42:44
Network Security, Session 9: Public Key Infrastructure ( PKI ) and Public Key Distribution
ANSLAB
237 views

21:20
What is symmetric key cryptography and asymmetric key cryptography?
Zzzzzzz
41 views
31:18
Achieve public key cryptography using AWS KMS Asymmetric key pair and OpenSSL.
Apar Vaidyanathan
1.0K views
4:46
Asymmetric Key Encryption | Public Key Cryptography
AB Labs
75 views

1:00
What is the difference between public key and private key encryption
Sigma Cyber Security
515 views

5:41
What is Cryptography in Sinhala | Symmetric Key Encryption and Asymmetric Key Encryption- Tearn
Tearn
154 views