Search Results for "Decryption Key"
Find videos related to your search query. Browse through our collection of videos matching "Decryption Key". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Decryption Key"
50 results found
5:38
What is Encryption , Decryption & Public Key Encryption ? | Tamil Tech Explained
Tamil Tech - MrTT
184.6K views
12:33
1. Hill Cipher Solved Example 2x2 Key Matrix | Hill Cipher Encryption and Decryption Mahesh Huddar
Mahesh Huddar
74.1K views

3:17
Vigenere Cipher - Decryption (Known Key)
Theoretically
101.1K views

5:25
Auto Key Cipher : Type of Encryption Decryption Method | Poly-alphabetic Substitution Cryptography
Quick Trixx
43.9K views
0:59
Example of Symmetric and Asymmetric Cryptography key Generation Encryption and Decryption
Cryptography & Cyber Security Solutions
63 views
12:47
vigenere cipher encryption and decryption || vigenere cipher decoder with key
Hamza Learning
8.8K views

10:18
vigenere cipher decryption part 1 , vigenere cipher with key, cryptography ||#mscoder
ms coder
109 views
9:48
Key Scheduling and Decryption in DES
Neso Academy
130.4K views

30:49
Data Encryption Standard (DES) in Tamil | DES key Schedule| DES Decryption | Do not memorize Part 2
Let's Learn - Kelvi
583 views

15:14
Asymmetric Encryption and Decryption in Node.js using RSA Public/Private Key Pairs
Techno Saviour
27.3K views

54:46
RSA Algorithm (Rivest–Shamir–Adleman) | public-key cryptosystem | Encryption | Decryption
ATT ArabTechTeam
89 views
9:31
Information Security | Vigenere cipher Solved example | Encryption | Decryption | How we Find key ?
NextGen Learners
13 views
3:59
NTFS EFS Decryption 04 - Decrypting EFEK to get FEK (File Encryption Key)
diyinfosec
758 views
2:32
Matlab Code for Key Based AES Image Encryption Decryption Using Matlab Project Code
IP INFOTECH PROJECTS
59 views
6:12
OpenSSL Tutorials #4: RSA key Creation and Encryption/Decryption
Openssl
8.0K views
0:35
Breaking Down RSA (Private Key & Decryption) #cybersecurity #linux #encryption #security
Black Bat Terminal
2.5K views

0:06
Asymmetric Key and Encryption, Decryption
SUKANYA BASU
77 views

10:52
TAMIL Explanation: Public Key Infrastructure - Encryption and Decryption flow with Example
Connect Cloud with Sakthi
9.5K views

1:01
Private Key vs Public key in Block Chain 👍🏻 #viral #youtubeshorts #blockchain #privatekey#difference
𝐔𝐣𝐣𝐰𝐚𝐥 𝐏𝐮𝐬𝐩
258 views

13:47
Key management- Symmetric key distribution using Symmetric Encryption
Computer Science Lectures
4.3K views

3:42
cryptography ( Symmetric key and Asymmetric key cryptography )
COMPUTER EDUCATION
16 views
0:10
In asymmetric key encryption, which term refers to the key used as your account?
10 Minutes Crypto
4.1K views

7:03
🔥WHAT IS SYMMETRIC CRYPTOGRAPHY AND ASYMMETRIC CRYPTOGRAPHY || WHAT IS PRIVATE KEY AND PUBLIC KEY?
Crypto Insaan
12 views

3:49
Hard To Say I'm Sorry (Karaoke) Chicago Woman/ Female key D# Low key/ No Vocal/ Minus one
Dafik Music Channel
150.9K views
13:39
PRINCIPLES OF PUBLIC KEY CRYPTOGRAPHY || ASYMMETRIC KEY ENCRYPTION -- NETWORK SECURITY
t v nagaraju Technical
83.3K views
0:52
How to Get Delta Executor Key | Bypass Delta Executor Key
RoExecutor
571.6K views

0:59
#shorts #crypto #wallet Public key vs Private key
Inside D'App
80 views

12:58
RSA Algorithm with Example | Asymmetric Key Cryptography (Public Key Cryptography)
Simple Snippets
26.4K views

7:50
Key Expansion in AES | Round Constant and g function in Key Expansion in AES
Chirag Bhalodia
40.9K views

8:02
Symmetric Key Encryption | Symmetric Key Cryptography
Perfect Computer Engineer
21.0K views

7:12
INTRODUCTION TO SYMMETRIC KEY CRYPTOGRAPHY ||SYMMETRIC KEY CRYPTOGRAPHY IN NETWORK SECURITY IN HINDI
CoverWorld99
192 views

19:02
Asymmetric Encryption With OpenSSL (Private Key & Public Key)
NeuralNine
15.7K views

32:28
17-How Public Key Distribution Works? 💡 | Secure Key Sharing in Network Security
Sundeep Saradhi Kanthety
107.5K views

14:53
Principles Of Public key Cryptography or Asymmetric Key Cryptography with example #cns #jntuh #feed
Concept Clear
191 views
21:10
OLevel M4 R5.1 | What is Cryptography ? | Symmetric vs Asymmetric key | Public VS Private key
Olevel Guruji
316 views

20:52
How to Encrypt and Decrypt in Python (Symmetric Key And Asymmetric Key)
Halogenius Ideas
480 views

8:25
Asymmetric Key Cryptography (Public Key Cryptography) Explained !
Success Wings
54 views

8:02
Diffie Hellman Key Exchange Algorithm | Key Agreement | Cryptography & Network Security |SKIT JAIPUR
CompAcademy
635 views

1:01
What’s the difference between a public key and a private key? #web3 #blockchain #crypto #nft
Dr. Brook Sheehan
484 views

10:05
RSA Example Lecture 1 | p=7, q=11, plaintext=m=9, Find public key (e), private key (d) & ciphertext
TRN CSE Tutorials
2.2K views
17:37
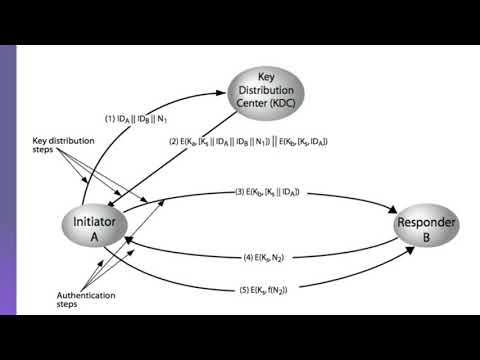
Key distribution in Cryptography | Key Hierarchy | Traffic Analysis
Computer Science Lectures
94 views

36:21
DES-Key Generation(64-BIT) "Cracking the Code" 🔓The Secrets of DES Key Generation"
The Builders
45 views

5:11
Private Key vs. Public Key Encryption Explained | CyberArk
CyberArk, Machine Identity Security Hub
6.2K views

0:54
the difference between symmetric key cryptography and asymmetric key cryptography | IS | INS | CS
Pooja Patel
8 views

6:23
Secrecy and Authentication using Public-Key/Two-Key Cryptography or Asymmetric Encryption
CSE Adil
86 views

2:03
Difference between private key cryptography and public key cryptography
Note creation
39 views

18:24
RSA ALGORITHM || SECURITY || EXAMPLE || PUBLIC KEY CRYPTOGRAPHY || ASYMMETRIC KEY CRYPTOGRAPHY
t v nagaraju Technical
54.1K views

3:56
How to get cipher text | problem based on cipher text | Cryptography | Public key and Private key
Student Globe
205 views

6:06
#31 Key Distribution in Asymmetric key cryptography |CNS|
Trouble- Free
124.1K views
9:35
What is Asymmetric Key Cryptography | Elements of Asymmetric key cryptography | Asymmetric cipher
Chirag Bhalodia
9.0K views
Previous Page 3