Search Results for "Data Security Measures"
Find videos related to your search query. Browse through our collection of videos matching "Data Security Measures". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Data Security Measures"
50 results found

7:32
CRYPTOGRAPHY AND NETWORK SECURITY(2) Principles of security, Security Services
Algorithm Pod
143 views

5:10:06
Cloud Security Full Course | Cloud Security Fundamentals | Cloud Security Training | Intellipaat
Intellipaat
80.6K views

7:07
What Is Cyber Security | How It Works? | Cyber Security In 7 Minutes | Cyber Security | Simplilearn
Simplilearn
4.8M views

18:38
Information Security- Part 3 - Wireless Security, Cryptography, Application/Host Security, and Logs
Russ Esposito
85 views

6:02
Introduction to cryptography and network security|network security|computers security
SCS VAJRA TUTORIALS
35 views

13:10
Types of security policies, www policy, email security policy, cyber security lecture series
Gaurav Khatri
9.3K views

8:46
Security Mechanisms | Computer Network Security | Information and Cyber Security |Full Course|Lec-04
Abhideep Online Education
11.7K views

23:56
What Is Network Security? | Introduction To Network Security | Network Security Tutorial|Simplilearn
Simplilearn
124.2K views

10:19
#2 Security Approaches and Principles or Goals of Security- Cryptography |Information Security|
Trouble- Free
99.1K views

6:06
Need for Security | Network Security | Cryptography and Network Security
Bikki Mahato
405 views

6:31
Network Security vs Cyber Security | What is Security? | Explained in Hindi
Tech Guru Manjit
16.0K views

3:57
Security Mechanisms | Network Security | Cryptography and Network Security
Bikki Mahato
184 views

7:31:09
Cloud Security Course | Cloud Security Training | Cloud Security Tutorial | Intellipaat
Intellipaat
16.2K views

12:12
#5 Security Mechanisms In Network Security | Information Security |
Trouble- Free
71.0K views

2:34
Top 5 Cyber Security Tools | Tools For Cyber Security | Top Cyber Security Tools | Intellipaat
Intellipaat
10.2M views

9:23
MIME protocol in Cryptography and Network Security | Email security in Network Security
Abhishek Sharma
119.7K views

6:48
Top 5 Android Security Apps|Security Apps for Android|Android Security App|App Android
TechTips
7 views

3:42
GuardMe Security - Home Security Systems & Commercial Security Systems
Craig Metzger
5 views

1:55
Retina Network Security Scanner - Conficker Worm Serial - Retina Network Security Scanner - Conficker Wormretina network security scanner conficker worm (2015)
Jose Sanchez
2 views

0:06
Read Security+ Guide to Network Security Fundamentals (Cyber Security) PDF Free
Tbestavashvili
1 views

4:53
Cyber Security in hindi | Cyber security | What is cyber security
hackploit
18 views

3:01
What is SECURITY AWARENESS? What does SECURITY AWARENESS mean? SECURITY AWARENESS meaning
tophoto
1 views

13:41
What Is PSDB Security ? ASSD Security . Security Guard Life in Uae .
Naresh Aryal
3 views

1:02
Best Security Guard Company in Kolkata|Darks Security|Security Services in Kolkata
Darks Security
11 views

5:30
What is security , information security and cyber security
Noor_khan official
3 views

1:00
security system (security system) "security system"
localvideotv
5 views

9:43
Information Security (IS) Vs Cyber Security (CS) || Security Goals
Simple & Effective Learning
735 views

14:40
SECURITY ATTACKS || TYPES || ACTIVE || PASSIVE || OSI SECURITY ARCHITECTURE --NETWORK SECURITY
t v nagaraju Technical
35.3K views

0:33
Data Security Revolution: AI and Blockchain Enhance Security in Forensic Engineering! Part 7 #ai
TEKTHRILL
20 views

0:44
Cryptography and information security: encryption algorithms and methods for ensuring data security.
Superpupt
75 views

15:50
🔐Cryptography - PART 2 - ENCRYPTION - Symmetric & Asymmetric | Data Security | HINDI | PhD Security
PhD Security
66 views

10:16
05-2 Cyber security || Data Security||Steganography || arabic
Mohamed hosseny
512 views

4:07
05-1-Cyber security || Data Security||Cryptography || arabic :
Mohamed hosseny
186 views

38:09
🔐Cryptography - PART 1 - ENCRYPTION - Symmetric & Asymmetric | Data Security | HINDI | PhD Security
PhD Security
94 views

0:08
Read Security for Computer Networks: An Introduction to Data Security in Teleprocessing and
Mlexer
3 views

0:23
Download Applications of Data Mining in Computer Security (Advances in Information Security)
Griffiths Anna
1 views

0:28
Read Network Security with Netflow and IPFIX: Big Data Analytics for Information Security
AdriaCoons
2 views

6:28
Data Security – looking beyond technical security to ...
cloudcor
28 views

5:50
Introduction to Wi-Fi Security from Network Data Security Experts
Network Data Security Experts
5 views

1:11
Audio and Video Steganography, Stenographer, data hiding, security, video data hiding, media
ArihantTechnoSolutions ATS
419 views

0:57
End-to-End Encryption Explained in a Minute | Data Encryption | Data Privacy and Security | #shorts
SCALER
23.7K views

0:43
Why is Data Encryption essential for Cloud Security? #cloudsecurity #cybersecurity #data #encryption
SecGaps
206 views

1:31
What is Data Encryption? Explained Simply | How Encryption Works & Protects Your Data cyber Security
CoreClass Education
239 views
4:42
How to Hide Data inside Image | Data Hiding Technique | Steganography ? #hack #security #tech
Abhishek Nishad Tech
39 views
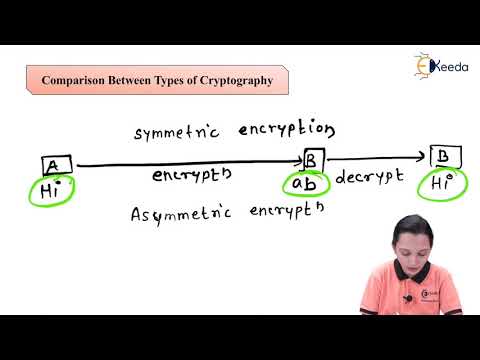
15:25
Comparison Between Types of Cryptography - Data Security - Data Compression and Encryption
Ekeeda
64 views

0:41
Cirrustar - Experts in Networking, Data Centres and Data Security
Jonathon Stillwell
19 views

0:07
Read Data Warehousing and Data Mining Techniques for Cyber Security (Advances in Information
Zakariadze Mariam
0 views

0:08
Read Data Warehousing and Data Mining Techniques for Cyber Security (Advances in Information
Farajian
0 views
![[PDF] Data Warehousing and Data Mining Techniques for Cyber Security (Advances in Information](/image/s2.dmcdn.net/v/Fk8QY1clXV9fVZCMS/x720)
0:08
[PDF] Data Warehousing and Data Mining Techniques for Cyber Security (Advances in Information
AikiraHarrell
4 views

0:22
Download Data Warehousing and Data Mining Techniques for Cyber Security (Advances in Information
Gsetty
3 views