Search Results for "AI prompting techniques"
Find videos related to your search query. Browse through our collection of videos matching "AI prompting techniques". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "AI prompting techniques"
50 results found

7:33
Cryptography lecture/tutorial: Substitution techniques for transforming plain text to cipher text
Sanjay Pathak
3.7K views

6:53
Transposition Techniques | Prof. Priyanka Sorte | PHCASC
MES e-Learning
142 views
24:21
Data Exfiltration Techniques with Metasploit and ICMP | TryHackMe
Motasem Hamdan
6.6K views

0:15
Types Of Cryptographic Techniques
EduAllinOne
3 views

43:20
Encryption Techniques From Traditional To Modern Encryption Technique - Devconf2025
DevConf
61 views
4:05
Classical encryptiin techniques, substitution technique, transposition technique
Gaurav Khatri
498 views
13:16
TOO MANY EMAILS? Use THESE Proven Techniques | Outlook tips included
Leila Gharani
3.4M views

25:30
IT314_Chpater 3.3_Substitution Techniques (Encryption)
Teacher Len
543 views

0:09
Dribbling techniques ⚽⭐ skills Tutorial # #soccer #football #footballskills #soccerskills
Neymerjr10_official
14.4M views

6:11
Symptoms Based Disease Prediction Using Machine Learning Techniques | IEEE Projects Hyderabad
Cloud Technologies
409 views
1:30
Top Cybersecurity Expert Reveals Best Encryption Techniques
MonkWire
89 views

0:23
Crypto Techniques | Crypto With Technology #meme #engineering v=FE3kjHEP5UY
Tech With FR
77 views

31:37
Classical Encryption Techniques - Substitution Cipher
Princy Ann Thomas
242 views

27:51
08_Cyber Security Techniques
Vijith Nambiar
35 views

1:32:08
Invisible Flirting Techniques That Create INSTANT Attraction
Matthew Hussey
84.8K views

13:46
Problem Solving Techniques in Programming - Algorithm, Pseudocode and Flowchart - Coding With Clicks
Coding With Clicks
200 views

0:06
best feeding techniques for hen automatic 😱😱😱
natureloby
1.4M views

5:04
One Time Pad | Vernam Cipher| Substitution Cipher Techniques| Introduction in Hindi | CSS
Gyanpur
86 views

59:23
Cyber security techniques II
Computing for All
412 views
9:37
cryptography and network security: Introduction, security goals, attacks,services and techniques
Pravisha candideyes
145 views
5:42
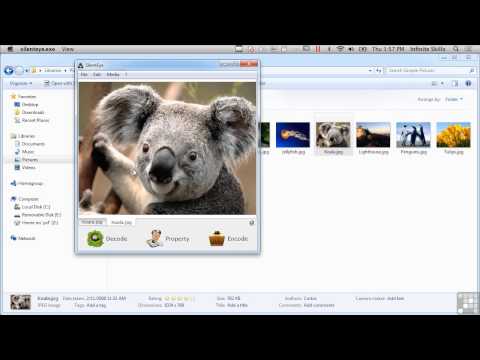
Learning Computer Forensics Tutorial | Steganography Techniques: Images And Video
O'Reilly - Video Training
11.6K views
18:16
IT314_Chpater3_Encryption Techniques Defined
Teacher Len
583 views

19:05
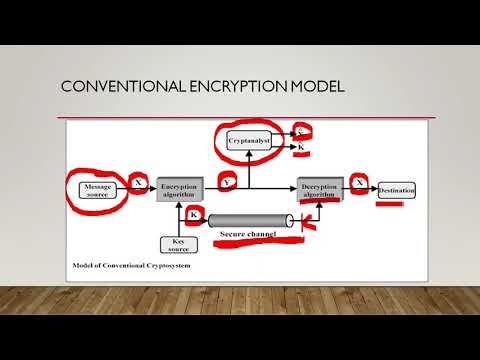
CSE571-11-02: Classical Encryption Techniques
Raj Jain
12.7K views

29:36
Transposition Cipher Techniques & Steganography
Learning Hub for IT Engineering
45 views

5:54
Vernam Cipher | One Time Pad | Substitution Techniques | Part 6 | Information Security
eVeda
110 views

0:19
Substring Returns: Mastering String Slicing Techniques #shorts
Durga Software Solutions
695 views

0:57
Classical Encryption Techniques
CoreCSE
230 views

24:37
IT P04 M-02. Symmetric cipher model, substitution techniques - Ceasar cipher
e-content:Engineering & Technology
72 views

10:41
Classical symmetric encryption techniques // Network Security
Global Exploration Knowledge Hub 2.0
49 views

7:03
Steganography Techniques: How to Encode and Decode Hidden Messages
Techinsights
59 views

18:19
10 Underrated Motion Design Techniques I LOVE
Ben Marriott
135.5K views
7:59
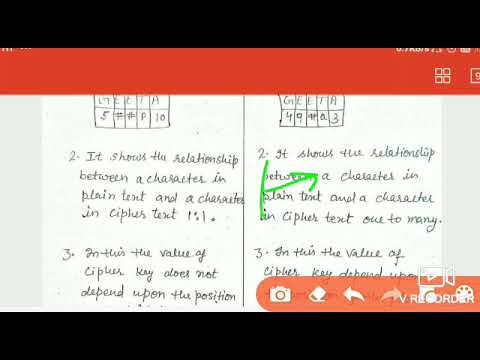
Monoalphabetic cipher and Polyalphabetic cipher |substitution techniques in Hindi by geeta Chaudhary
Short Tricks Learning
781 views
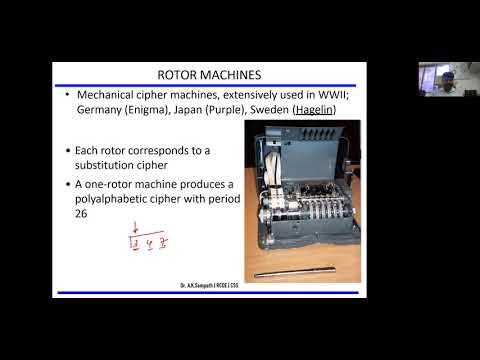
37:26
Rotor Machine, Steganography techniques
Prof. sampath
571 views

28:17
Négociation : 10 techniques d'Expert et leurs parades (source: Harvard, FBI, GIGN)
Quentin Despas - Vente SaaS B2B
27.2K views

7:28
#Substitution Techniques Caesar Cipher in Cryptography & Network Security L-10 #encryptionTechniques
Concept Clear
275 views

2:38
13 Cryptographic Techniques ISACA CISM DOMAIN 3 INFORMATION SECURITY PROGRAM
TUTORIAL
315 views
0:41
Cryptography Techniques #networksecurity #cryptography #encryption #networkengineer #hashing
Team IPwithease
173 views

5:21
Error Recovery Techniques in compiler Design explained step by step | Lexical Analysis
Nimish Munishwar
3.0K views

6:58
Secure Cloud Computing Access via Hybrid Encryption Techniques
U.K.K Sandeepa
149 views

23:41
TY BSc-IT - NS Unit 1 - Lec 4 - CRYPTOGRAPHY TECHNIQUES, Substitution, Transposition, Ceasar Cipher
Tirup Parmar
887 views
5:57
classical encryption techniques||urdu||hindi||lec3
ITphile
713 views

46:54
Encryption Techniques || Substitution and Transposition ||Caesar, Atbash, Polybius, Pigpen, Playfair
Kifayat Ullah
408 views
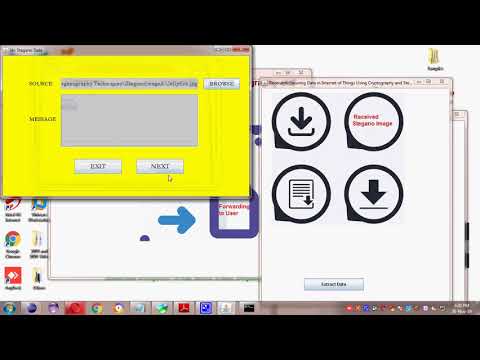
6:26
Securing Data in Internet of Things Using Cryptography and Steganography Techniques
Manjunath IEEE Projects
2.2K views

11:25
Transposition techniques & Stenography | Computer and Network Security | 3350704 | Darshana T. Patel
VPMP POLYTECHNIC
62 views
7:19
Data Hiding of Gray Scale Images using LSB Techniques
1 Crore Projects
30 views

0:20
With technology anything is possible, canalization cleanup techniques and technology #innovation
KSSE Structural Engineers
25.3M views

0:30
VerdaCrypt Ransomware: Exploring Its Unique Philosophy and PowerShell Encryption Techniques
Hacked dAily
14 views

26:58
Module 4: Overview of Cryptographic Techniques
USF Crypto Center
397 views

24:30
Encryption and Cryptographic Techniques
Professor K
194 views

3:41
How To Protect Yourself?!👊| 10 Amazing Self Defense Techniques
Elhusseiny Wageh | The 1%
587.1K views