Search Results for "yubikey security key"
Find videos related to your search query. Browse through our collection of videos matching "yubikey security key". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "yubikey security key"
50 results found

8:02
Diffie Hellman Key Exchange Algorithm | Key Agreement | Cryptography & Network Security |SKIT JAIPUR
CompAcademy
635 views

18:24
RSA ALGORITHM || SECURITY || EXAMPLE || PUBLIC KEY CRYPTOGRAPHY || ASYMMETRIC KEY CRYPTOGRAPHY
t v nagaraju Technical
54.1K views

12:43
Lec-03:Asymmetric Key Or Public Key | CRYPTOGRAPHY AND NETWORK SECURITY
webSak
45 views

6:34
Asymmetric Key: Public Key |Cyber Security |Encryption |Cryptography
Sanjay Pathak
1.3K views

5:22
Network Security || Symmetric key Vs Asymmetric key Encryption
Tameshwar Sahu
71 views
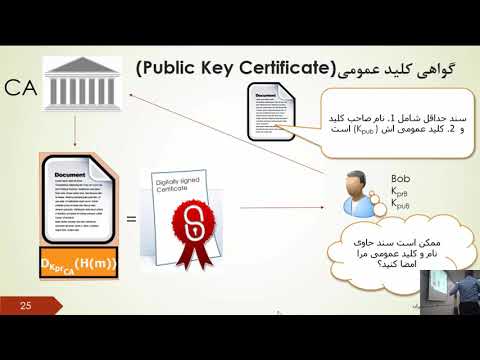
42:44
Network Security, Session 9: Public Key Infrastructure ( PKI ) and Public Key Distribution
ANSLAB
237 views

50:02
Cryptanalysis of Symmetric Key Cryptography | Private Key Cryptography | Information Security
Shiv Yog Classes
8 views

3:08
symmetric key vs asymmetric key (hindi/urdu) | cryptography and network security || #mscoder
ms coder
346 views

8:22
ASYMMETRIC KEY CRYPTOGRAPHY ||NETWORK SECURITY ||ASYMMETRIC KEY CRYPTOGRAPHY SIMPLY EXPLAINED|| NET
CoverWorld99
210 views

1:33
Private Key vs. Public Key: Crypto Security Explained
Hipo
120.2K views
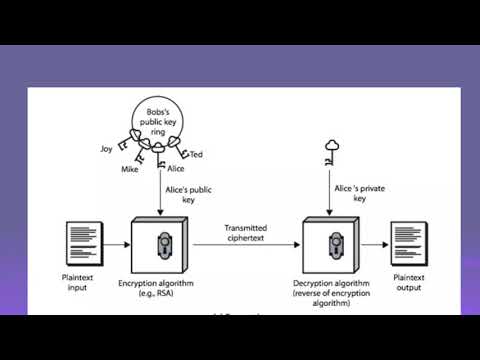
15:32
PUBLIC KEY CRYPTOGRAPHY || ASYMMETRIC KEY ENCRYPTION -- NETWORK SECURITY
Computer Science Lectures
28 views
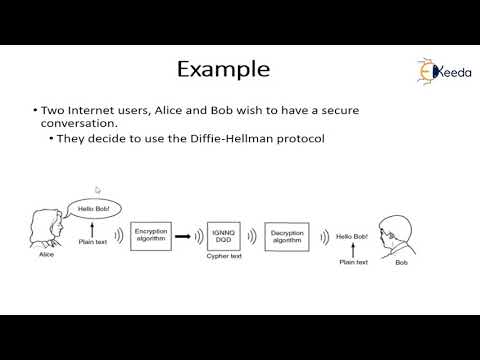
16:38
Key Management Diffie Hellman key Exchange | Cryptography and Network Security
Ekeeda
68 views

12:09
Diffie Hellman Key Exchange Algorithm | Secret Key Exchange | Network Security Tutorial | Edureka
edureka!
65.4K views

6:57
Computer Network Security Public Key Encryption / Asymmetric Key Encryption in Hindi
DrMonika Varshney
758 views

6:00
Key range and Key size in Cryptography and Network Security | Lec-17 | #cryptography #keysize #cns
Concept Clear
2.2K views

5:26
Asymmetric key Cryptography |Public key Cryptography| Network Security..
DK Technical Point 2.0
261 views

5:37
What is Cryptography? Network Security| Block Cipher |Stream Cipher | Symmetric Key | Asymmetric Key
IT Academy
123 views

4:10
What is symmetric key & asymmetric key ?(Network SECURITY)
technical information
39 views

5:05
Public key Cryptography full explain in hindi-Asymmetric key Cryptography,Computer Network Security
Unbeaten Learning
41.4K views

3:40
Computer Network Security Q&A Series 2/15 Difference Between Secret Key And Public Key
Study With Harshit
6.4K views

0:47
Unlocking Unbreakable Security: Quantum Key Distribution Explained #viral #shorts #ai #quantum #key
lOOK to the FUTURE
29 views

17:14
Model for network security & one key, two key Cryptography by P Kalyan Chakravarthy
kalyan chakravarthy
97 views

5:34
SYMMETRIC KEY CRYPTOGRAPHY VS ASYMMETRIC KEY CRYPTOGRAPHY IN NETWORK SECURITY
MCA PLUS
121 views

22:03
Cyber security # Unit 1# Private and Public Key Cryptography # Symmetric and Asymmetric key crypto
Guptasmartclasses
95 views

9:05
CRYPTOGRAPHY || SYMMETRIC KEY & ASYMMETRIC KEY || NETWORK SECURITY PART - 11
Aakash Kumar
19 views
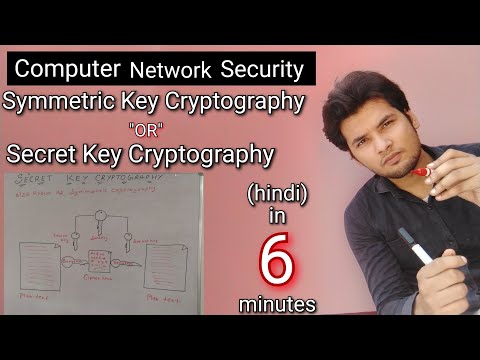
6:03
Symmetric Key Cryptography explained in Hindi || Secret key cryptography ,Computer Network Security
Unbeaten Learning
28.6K views

0:21
The difference between symmetric key & asymmetric key cryptography | information security
Pooja Patel
8 views
9:05
Key Management and Distribution in Cryptography and Network Security #security #cryptography #cse
Lab Mug
3.7K views

25:14
Internet Security (IP) Protocol - Security Assosiations & IKE ( Internet Key Exchange)- #21is71 #cns
VTU padhai
2.3K views

0:51
Why Bitcoin's Use of Public Key Cryptography Revolutionizes Security #Coinscrum #Bitcoin #Security
Coinscrum - Bitcoin & Web3 Community
649 views

9:25
Principles of Public key cryptography in Network Security || Cryptography and Network Security
Lab Mug
7.1K views

0:29
Key Concept Of Cyber Security | Types OF Cyber Security #short #definition #MCQS
L430 Wala
6 views

36:16
Security of Quantum Key Distribution 9: Security Definition
Ramona Wolf
1.7K views

24:37
Information Security Lec 05: Low, Moderate & High Security Levels | Computer Security Challenges
Tech CS&IT
2.2K views

6:02
Network Security Model | Network security model in cryptography | Network Security
Chirag Bhalodia
22.5K views

8:36
Network Security Model| Model of Network Security | Information and Cyber Security
T N V S PRAVEEN
292 views

14:06
CRYPTOGRAPHY AND NETWORK SECURITY NOTES | NETWORK SECURITY NOTES | NETWORK SECURITY
DIVVELA SRINIVASA RAO
382 views

8:25
Cryptography and Network Security Unit 1- Part 5 | Network Security & Network Access Security Models
TN55 RLE
442 views

44:58
Computer Security | What Is Computer Security | Cyber Security Tutorial | Simplilearn
Simplilearn
95.6K views

12:04
Approaches of web security in urdu hindi | approaches of web security lecture | web security | p 49
IT Expert Rai Jazib
1.3K views

2:47
IP Security overview, IP Security architecture, Cryptography and Network Security.
Algorithm Pod
488 views

44:53
Networks Security | Security Services | Security Goals | Cryptography | Steganography | Attacks | IA
Bhavishya Coaching SGNR
929 views

3:44
Cyber security क्या है? | What is Cyber Security in Hindi? | Why Cyber Security is Important?
Deepak TechTimes
59.8K views

9:13
What is Security and security attacks, security services in CNS
Lab Mug
13.4K views

1:01:28
Cryptography & Network Security | CH1.2 The OSI Security Architecture & 1.3 Security Attacks
Computer & IT lectures
67 views

7:32
CRYPTOGRAPHY AND NETWORK SECURITY(2) Principles of security, Security Services
Algorithm Pod
143 views

5:10:06
Cloud Security Full Course | Cloud Security Fundamentals | Cloud Security Training | Intellipaat
Intellipaat
80.6K views

7:07
What Is Cyber Security | How It Works? | Cyber Security In 7 Minutes | Cyber Security | Simplilearn
Simplilearn
4.8M views

18:38
Information Security- Part 3 - Wireless Security, Cryptography, Application/Host Security, and Logs
Russ Esposito
85 views

6:02
Introduction to cryptography and network security|network security|computers security
SCS VAJRA TUTORIALS
35 views
Previous Page 2