Search Results for "woo and lam authentication protocol"
Find videos related to your search query. Browse through our collection of videos matching "woo and lam authentication protocol". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "woo and lam authentication protocol"
50 results found

2:05
Ed Protocol Ingredients || Erectile Dysfunction Protocol
Helenaghv
8 views

9:59
Alpha Protocol Walkthrough - Infiltrate Alpha Protocol ...
MahaloGames
1 views

1:32
Massive protocol PM Abbasi Protocol in Karachi
MTV
49 views

1:24
IMAM E KABA PROTOCOL IN PAKISTANIMAM E KABA PROTOCOL IN PAKISTAN
All In one
1 views

2:33
Ed Protocol Review || Erectile Dysfunction Protocol Review
Vernitaw0z
1 views

0:06
Encryption Protocol. #cybersecurity #cyberpunk #viral #protocol #sslcertificate
Infintysec
179 views

1:27
people Bushing Sharif Brothers Because of protocol In jinah hospital because of protocol
harpal.pk
16 views

1:45
erase herpes protocol review - erase herpes protocol
Get rid of hives
24 views

14:31
Network Protocol Explained | Types Of Network Protocol | Fundamentals Of Networking | Simplilearn
Simplilearn
1.4K views

0:08
Read Multimedia Encryption and Authentication Techniques and Applications (Internet and Communications)
Reimold
0 views

10:56
CS409(Mod4_1): Message Authentication and requirements - Module 4 -Cryptography and network security
Greeshma G S
11.7K views

2:31
Cryptography And Network Security :-Authentication And key Agreement
Bharati Kale
496 views
0:11
#hrb Fredo and #harlemspartans SD react to retaliation for #hrb Big Woo🤯🤯
ASM Media
48.4K views

0:15
Head Over Heels Kdrama BTS | Choo Young woo and Cho yi hyun #choyihyun #chooyoungwoo #headoverheels
Drama shorts
2.6M views

0:11
Lil Dotz and Hrb the day before his brother Stutz/Woo dies
6ix9ine Instagram Live
21.3K views

0:10
Cha eun woo and moon ga young (2020-2025) journey..🤍 #chaeunwoo #moongayoung #celestialdramatales
𝓒𝓮𝓵𝓮𝓼𝓽𝓲𝓪𝓵 𝓭𝓻𝓪𝓶𝓪 𝓽𝓪𝓵𝓮𝓼 ♥︎
807.6K views

2:55
FREE By Arden Cho and Cha Eun-woo | KPop Demon Hunters | Netflix
Still Watching Netflix
7.3M views

0:13
Lisa and Cha Eun woo from Penshoppe to Bvlgari
LuckyCat
2 views

2:33
BTS V And JIN "LOST" TO ASTRO CHA EUN WOO!!!
BTS Latest
66 views

2:06
Bihar Elections 2025: Will Nitish Secure CM Post if JDU Gets Numbers and RJD Attempts to Woo Him?
Asianet News English
18 views

0:18
Jin Woo and Kaisel 🛐🥶#shorts#sololeveling#edit#anime#manhwa#trending#manga#manhua#webtoon#fyp#amv
Edit_chan_
1.9M views

3:09
Learn Colors and Shapes with Animals Woo 6
Kzk75716
566 views

1:53:40
ENG SUBCinderella didn't love CEO anymore, he panicked and brought his son to woo her!#cdrama
Short Viral
491 views

39:03
Covid Cryptography 6: Message Authentication Codes and Authenticated Encryption
MathMesh
122 views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views

12:54
Authentication Functions | Cryptography and Network Security
Ekeeda
910 views

1:04:39
Message authentication and hash functions (part-1)
Keerthi Humsika K
58 views

18:07
Lecture 23: Public key cryptography and authentication method Asymmetric Key Requirements
QZ Historia
41 views

1:15:07
Lecture 25: MAC (Message Authentication Codes) and HMAC by Christof Paar
Introduction to Cryptography by Christof Paar
63.8K views

1:04:18
Assumptions of Encryption and Authentication (ITS335, L04, Y15)
Steven Gordon
1.2K views

1:04:28
Cryptography and Network Security BCS072 Unit 3 One shot | Message Authentication Codes Unit 3 AKTU
EduShine Classes - Arman Ali
273 views

9:11
Security goals of Cryptography (Authentication, Integrity, confidentiality and, Repudiation) Hindi.
Helping Tutorials
12.1K views

1:19:10
Authentication with Symmetric Key Crypto and MACs (CSS322, L17, Y14)
Steven Gordon
1.5K views

2:46
USER AUTHENTICATION USING CRYPTOGRAPHY AND STEGANOGRAPHY FOR WEB APPLICATIONS
Gagan Suneja
214 views
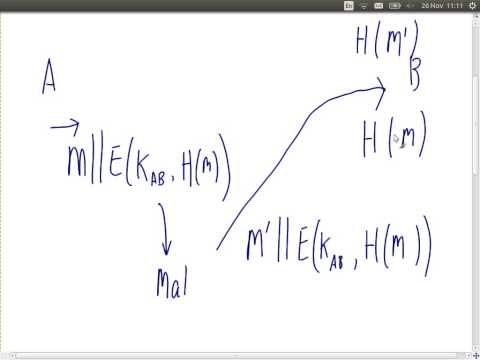
1:18:04
Authentication and Public Key Cryptography (ITS335, Lecture 5, 2013)
Steven Gordon
1.3K views

12:09
Lecture 22: Lecture 4 slides- Public key cryptography and authentication method
QZ Historia
42 views

0:59
Passwordless Authentication Using a Combination of Cryptography, Steganography, and Biometrics
Journal Club
14 views
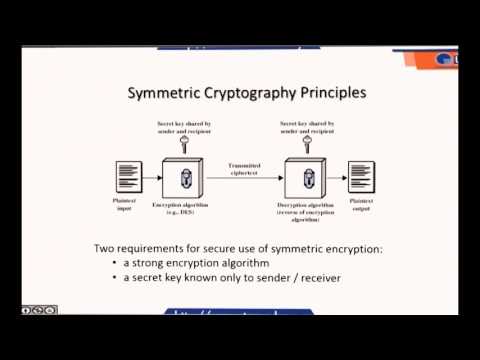
6:05
LECTURE 2- AUTHENTICATION AND BASIC CRYPTOGRAPHY (PART2)
UTeM MOOC
40 views

12:56
60 Multifold Secured Bank Application authentication service using Random Visual Cryptography and Mu
ICMISC
13 views
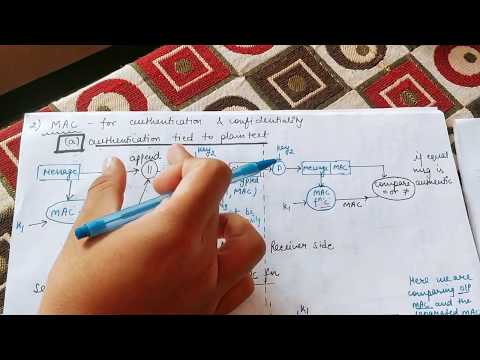
14:41
MAC in Cryptography || Message Authentication Code in Cryptography and network security
Abhishek Sharma
396.9K views

24:09
Passwordless Authentication Using Steganography, Cryptography And Biometrics - Tunde Oduguwa
BSides Bristol
39 views
10:23
Analysis of Biometric Authentication System – Security Issues and Working using Visual Cryptography
OKOKPROJECTS
114 views
1:20:56
COSIC Course 2024: "Cryptographic protocols for entity authentication and..." (Bart Preneel, COSIC)
COSIC - Computer Security and Industrial Cryptography
239 views

0:05
Read Access Control Authentication And Public Key Infrastructure (Information Systems Security
Tuuli Mark
1 views

0:05
Download Access Control Authentication And Public Key Infrastructure (Information Systems Security
Maisi Baker
2 views
![[Read PDF] Mobile Authentication: Problems and Solutions (SpringerBriefs in Computer Science)](/image/s2.dmcdn.net/v/Gz4Gl1e0GalIcGrjm/x720)
0:24
[Read PDF] Mobile Authentication: Problems and Solutions (SpringerBriefs in Computer Science)
Aron Davonte
1 views

1:08
Client authentication: Systems that are more and more secure
Orange
71 views

0:30
About For Books Mechanics of User Identification and Authentication: Fundamentals of Identity
dm_09d226e7605f9f5a1a3a6425e52120d4
0 views

7:13
#35 MAC ( Message Authentication Code ) - Working and Significance |CNS|
Trouble- Free
223.0K views

9:30
AAA and Authentication - CompTIA Security+ SY0-501 - 4.1
Professor Messer
117.2K views
Previous Page 2