Search Results for "user security"
Find videos related to your search query. Browse through our collection of videos matching "user security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "user security"
53 results found
5:30
What is security , information security and cyber security
Noor_khan official
3 views

1:00
security system (security system) "security system"
localvideotv
5 views

9:43
Information Security (IS) Vs Cyber Security (CS) || Security Goals
Simple & Effective Learning
735 views

14:40
SECURITY ATTACKS || TYPES || ACTIVE || PASSIVE || OSI SECURITY ARCHITECTURE --NETWORK SECURITY
t v nagaraju Technical
35.3K views

2:30
Briefly describe on characteristics of the UDP(User datagram protocol)
Informative Tutorials
159 views
1:01
Windows 10 user good news for you 🥳 #shorts #windows10 #securityupdate
Prince Shah
587.1K views

3:43
CybersecurityComplianceFramework&SystemAdministration|WEEK 3 Server&User Administration Quiz Answers
Anand Ranjit Kumar Mukkala
2.5K views

10:30
15. Encrypting User Data with EFS in Active Directory
MSFT WebCast
18.2K views
![How to Create Multi User Login Form in java using MySQL Database ? [With Source Code]](/image/i.ytimg.com/vi/4IFvc7JOqtA/hqdefault.jpg)
18:55
How to Create Multi User Login Form in java using MySQL Database ? [With Source Code]
RunCodes
125.4K views
9:05
How To Conduct User Interviews Like A Pro (UX Design)
CareerFoundry
162.7K views
20:53
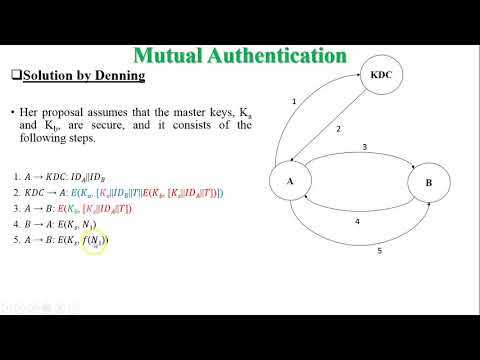
Remote User Authentication Using Symmetric Encryption | Needham Shcroeder Protocol
Chirag Bhalodia
33.5K views
0:42
Best i videos downloader app for iphone user #viral #shortvideo
Jacobabado Shazii
466.0K views

10:18
The Biggest Women A*user of Bollywood | Exposed
Absolute Aryann
215.7K views

16:13
ACISP2020 Tightly Secure Chameleon Hash Functions in the Multi User Setting and Their Applications
Xiangyu Liu
230 views
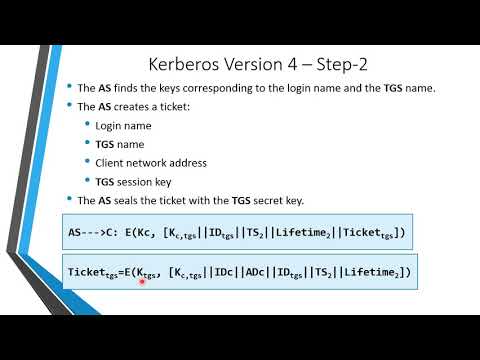
20:25
INS: Unit-9 Remote User-Authentication (Kerberos)
Twinkal Patel
423 views

0:43
Quickly organise lengthy user research with ChatGPT & Figjam | UIUX Design
yourdesignbestie | UX Design & Lifestyle
12.5K views

11:34
Advantage of Cryptography Tools & Securing End User Equipment
Ziauddin Zia
40 views

2:46
USER AUTHENTICATION USING CRYPTOGRAPHY AND STEGANOGRAPHY FOR WEB APPLICATIONS
Gagan Suneja
214 views

11:52
Data Cleaning in Excel | 8 Tricks to Make You a Pro User
Kenji Explains
137.5K views

17:06
Create User Registration Form in Java with MySQL || Swing and JDBC
CS CORNER Sunita Rai
47.8K views

0:25
Fastest way to design a user flow diagram #ux #uxdesigner #ui #uidesign
Jan Mraz UX
99.1K views

1:09:38
CSE571-11-15B: User Authentication Protocols (Part 2 of 3)
Raj Jain
1.8K views
0:18
User Interface Animation Demo - UX/UI Student - Careerfoundry
M. Hunter Armstrong
64 views

20:54
Can You Be a Functioning Heroin User? | High Society
VICE
5.2M views
0:20
How to search your Roblox user ID on web #roblox #findthemarkers #userID
IS
439.1K views

8:02
Caesar Cipher: Encryption and Decryption In Python (Hindi) | User Improvement | #YouTube
AffiSoftPro
100 views

28:12
Deutschrock mix von User Kübi
Deutschrock-Radio
159.2K views

17:06
Magnet User Summit - Capture The Flag - May 2023 - Cipher
BlueMonkey 4n6
364 views

13:30
Encrypt & Decrypt user credentials | Crypto-JS | Playwright Tutorial - Part 89
LetCode with Koushik
31.9K views
0:12
how to lock this computer# how to switch user# log off# how to change a password# ctrl+Alt+Delete
Habib online shoes LLC
1.4M views

1:01
How to use masterpassword to login #enter thin client pc user settings #shorts
Nefe Blog Tech
2.6K views
1:00
Reset a user's password in Active Directory (GUI)
vCloudBitsBytes
34.4K views
12:32
Encrypting User Data with EFS in Windows Server 2016
microsoft lab
10.3K views

8:53
10 Powerful Tips Every Audacity User Should Know
Mike Russell
92.8K views

8:37
Remote user authentication using symmetric encryption
Anand Pashupatimath
4.6K views

4:27
Introduction to User Authentication - CompTIA Network+ N10-005: 5.3
Professor Messer
15.0K views
31:12
An Efficient Multi User Searchable Encryption Scheme without Query Transformation Over Outsourced En
1 Crore Projects
626 views
0:36
how to start kali liux in nethunter in termux Hindi | switch to root user in termux in Hindi |
Gureja Cyber
89.0K views
10:01
Preserving a user’s anonymity with cryptographic protocols | BeWater DevCon II
BeWater Community
257 views
0:14
Creating new user account, microsoft windows 10. using compmgmt.msc
IThelp9
234.0K views

0:27
Change a user to an Administrator Account | Short Tips
Simple Tech Tips
507.4K views

58:47
Kerberos Version 4 & 5 and Remote User Authentication with Asymmetric Encryption -#21is71 VTU 7thsem
VTU padhai
2.3K views
0:13
Windows 11- How to set password existing user OR admin using CMD
IThelp9
251.5K views

0:20
"user first" #techstartup #softwaredevelopment #corporatehumour
tl;dv - meeting assistant
38.5K views
15:53
Arattai App Kya Hai❓Use Kaise Kare❓WhatsApp Alternative❓How to Create Arattai Account, User ID, Bugs
Sikhe All In Hindi
82.5K views

13:10
Step-by-step user research guide I use at Google as a UX designer
Justeen15
11.9K views
13:31
Build Node.js User Authentication - Password Login
Web Dev Simplified
565.0K views

21:42
Remote User Authentication: Principles & Techniques | Cryptography- #21is71 #cryptography #vtupadhai
VTU padhai
4.0K views
15:03
Decrypt EFS protected files by recreating the missing user certificate
Simpan
5.6K views

13:50
Solutions Architect Interview - Limiting User Access (with Salesforce SA)
Exponent
5.0K views

0:58
Apple Introduces Fast 'Security Responses' for iPhone, Mac, and iPad 🔒
Veuer
20.6K views
1:20
Economy Ministry swiftly fixes security loophole in Padu, thanks user for highlighting issue
The Star
2.5K views

1:00
Millions of Google Chrome users urged to check this setting over security threat
OhMyMag UK
21.2K views