Search Results for "used utv"
Find videos related to your search query. Browse through our collection of videos matching "used utv". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "used utv"
50 results found

1:48
What is a Prime Number? What Are Prime Numbers Used For?
Eye on Tech
98.4K views

0:16
I Used Superpowers To Save 10 Animals! 🤯#animalrescue #globaltrends #savinglives
Oscar's Sandbox
749 views
58:40
CTF : Steganography | Forensics Challenges - Tools to be used - Walkthrough - English
Tech Enn
10.4K views

0:46
Delhi Bomb Blast News | Eyewitness Describes The Car Used In Delhi Blast Near Red Fort
NDTV
487.1K views

0:27
Evaluate the history of cryptography from its origins Analyze how cryptography was used
ESSAYA ORG
0 views

13:51
what is MAC? why is it used? Applied Cryptography
Rands
159 views

30:14
The Most Destructive Hack Ever Used: NotPetya
Cybernews
3.7M views

3:51
What is cryptography? | Main Algorithm used | daily usages | Doorbell DD
The Digital King
1.2K views

3:43
How To Buy A Used ATV
Dirt Trax TV
484.5K views

7:42
Digital Signature - Asymmetric Key , Why used for Authentication & Non Repudiation (Hindi)
Easy Engineering Classes
177.3K views

4:28
How Is Steganography Used In Cybersecurity? - SecurityFirstCorp.com
SecurityFirstCorp
9 views

32:44
JNTUK R16 III CSE SEM2 CYBER SECURITY UNIT 4 INTRODUCTION TO TOOLS & METHODS USED IN CYBER CRIME LEC
RVIT — Autonomous, Guntur
1.8K views

2:47
How Are Qubits Used in Quantum Cryptography? | Quantum Tech Explained News
Quantum Tech Explained
32 views

12:11
They don’t make ‘em like they used to (and they shouldn’t)
The Grumps
306.1K views
4:21
How Is The Vigenere Cipher Used In Cryptography? - SecurityFirstCorp.com
SecurityFirstCorp
9 views

5:05
Intelligence Agencies Used Sports Propaganda in US vs USSR Cold War
D.A.T.A Productions Media
321 views
3:00
How Russia used language to justify its war in Donbas
Kyiv Independent
51.1K views

0:41
Top Secret Encryption Systems Used by Presidents, Diplomats, and VIPs | Unbreakable Security
CRYGMA.COM Encryption
48 views
0:32
EASIEST FX Trading Strategy I’ve ever used (ORB)
Trade with Pat
55.8K views

3:07
Used car demand and prices skyrocketing across the country
FOX 29 Philadelphia
1.5K views
0:56
How I Used $0 to Create 1000+ Videos on Autopilot With This AI Agent System (No Paid API Needed)
Andy Lo
293.3K views

7:23
Cryptography Part 19 :- Algorithms used for generating Pseudorandom Numbers
Tech Lover
286 views

4:37
When Is Steganography Used? - SecurityFirstCorp.com
SecurityFirstCorp
2 views
0:05
What python can do? What python is used for? #coding #python #programming | Developer Shaurya
Developer Shaurya
45.9K views
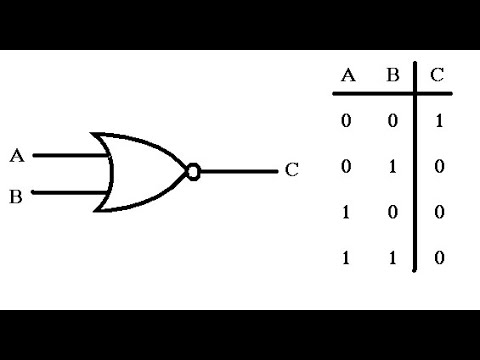
7:14
Why XOR is used everywhere in Cryptography?
DG
605 views

52:55
Tools and Methods Used in Cybercrime Part 2 | Dr. Reshma Kadam
Reshma Patil
826 views

0:30
What is Dot Matrix Printer ✨ How Dot Matrix Printer Works ✨ Where Dot Matrix Printer Used #dotmatrix
Variety Next
15.4K views

2:13
Pakistan NSA claims Afghan soil still being used against Pakistan, IEA denies
Ariana News
1.4K views
0:09
What is Ctrl-Alt-Delete, and what’s it used for? #shorts #youtubeshorts #shortcutkeys
KNOWLEDGEmania 9T4
2.2M views
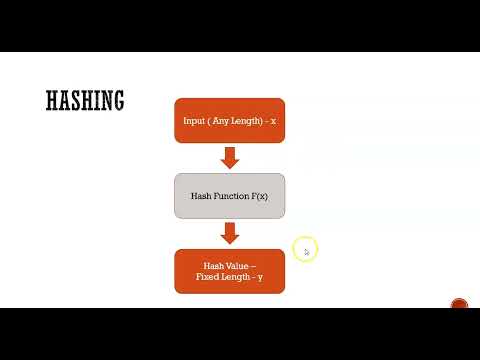
9:13
What is Hashing? How it is used in Blockchain? | #7 Blockchain Course
Hema's Desk
75 views

11:04
Top 10 Blockchain Terminology - A glossary for beginners | Top 10 Commonly used Crypto Terms
BharatiDWConsultancy
362 views
49:53
I Used $300 of Cloud Credits to Train an AI Stock Trading Bot
Ryan O'Connell, CFA, FRM
2.9K views

0:48
When “Us” Turned Into “Used To Be” 💔💭 #ainishq #onelove #KızılcıkŞerbeti | UD3R
Husn Beparwah (Beauty Inside) by DRM
1.4K views

0:42
Grossest Way SPOT'S Powers were used in Comics😨| #spiderman #spot #daredevil #marvel #comics #comic
Nerdak Comics
11.5M views
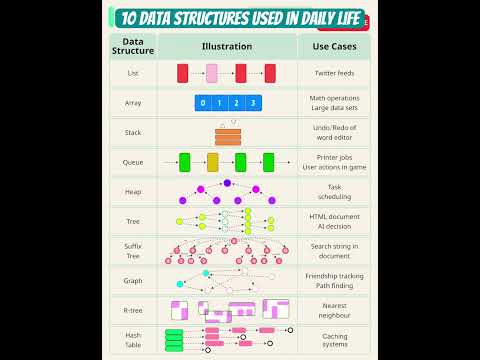
0:03
10 Data Structures Used in Daily Life #datastructures #developer #softwaredevelopment
Don Hash
37 views
3:12
Is Data Augmentation Used In Machine Learning? - The Friendly Statistician
The Friendly Statistician
21 views
7:08
Blockchains: how can they be used? (Use cases for Blockchains)
Simply Explained
478.8K views
9:34
An Update on the Used Car Market
Aubrey Janik
33.7K views
0:43
Afghan Soil Used for Te**orism is Unacceptable — Gen. Asim Munir | Breaking News
News One
18 views

0:28
The Mathematics Used By Quant Trading Firms #investing #trading #shorts
Investorys
229.5K views
4:54
Hands-On Cryptography with Java : Symmetric Ciphers and Where They Are Used | packtpub.com
Packt
128 views

0:11
Enfield P14 used in WW1 and WW2
Canadian Classics
1.3M views

25:10
Cognitive Load Just KILLED Active Recall (How I Used ENCODING At Medical School)
Dr Alex Young
93.8K views

3:29
How Is Steganography Used In Malware? - SecurityFirstCorp.com
SecurityFirstCorp
56 views
2:57
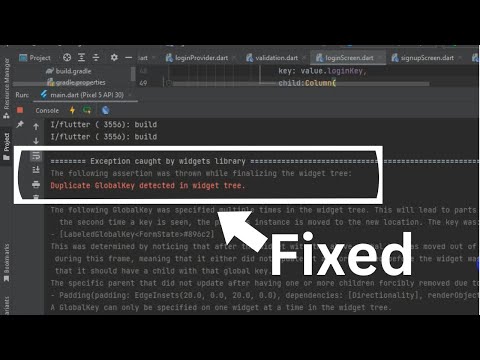
Duplicate GlobalKey detected in widget tree | Saurav Roy | Multiple widgets used the same GlobalKey.
Saurav Roy
461 views

3:53
How Is Steganography Used With Videos? - SecurityFirstCorp.com
SecurityFirstCorp
13 views

0:58
Rust being used in Ransomware
Apna College
886.0K views

3:25
What Tools Are Used For Steganography? - SecurityFirstCorp.com
SecurityFirstCorp
51 views
0:44
Can a Katana Be Used as a Baseball Bat? ⚾⚔️ ✅
Mini Katana
18.2M views
0:09
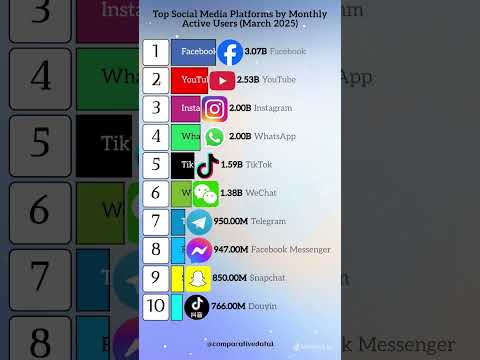
🌍 Top 10 Most Used Social Media Apps in 2025 🔥 | Facebook vs TikTok vs Instagram 💥
Comparative Data
3.9K views