Search Results for "types of cryptography functions"
Find videos related to your search query. Browse through our collection of videos matching "types of cryptography functions". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "types of cryptography functions"
50 results found

6:38
Granulocytes- Types and Functions
Noise Education TV
2 views
3:17
Types of Functions
learnscart
0 views

5:33
Computer Ports and Connectors on Front and Back side of CPU Uses and Functions | Ports Types |
Tech Support Helper
323 views

5:22
Types of Flowgorithm Functions
TestingDocs
3 views

5:23
Gears - Types And Functions
Edu-Primes
13 views

6:28
Structures -Types - Examples -Functions
Edu-Primes
15 views

7:38
Types Of Blood Vessels And Their Functions
Edu-Primes
18 views
16:08
Computer Keyboard Full Guide – Types, Functions aur Use Kaise Karein | In Urdu/Hindi/Hinglish
IbnGhufran.com
5 views

8:11
What is Ransomware | Types of Ransomware | Cryptovirology and Cryptography | Malware and its Types
World Walk
264 views

0:13
Types of Cryptography | Types of Cryptographic
Maths With Bushra
5 views

22:03
TYPES OF FIREWALL IN CRYPTOGRAPHY AND NETWORK SECURITY EXPLAINED IN TELUGU#telugu#firewall#types#cns
Chinni Educationalclub
1.8K views

42:41
Cryptography Lecture 04: Cryptanalysis, Types of Attackers, Types of Attacks, Security Norms
Maths Submarine
35 views

15:25
Types Of Security Attacks #Active & #Passive Attacks and their Types | Cryptography Network Security
Concept Clear
355 views

3:40
What is Cryptography? | Explain Cryptography | How Cryptography Works? | Cryptography Information
Crypto & Blockchain News (CBN)
4 views
![[Cryptography] What is Cryptography? | Introduction To Cryptography | Cryptography Tutorial in Hindi](/image/i.ytimg.com/vi/8are73H9oUQ/xhqdefault.jpg.pagespeed.ic.GWwooXAHkM.jpg)
19:28
[Cryptography] What is Cryptography? | Introduction To Cryptography | Cryptography Tutorial in Hindi
Cyber Odisha
97 views

8:20
Cryptography|Cryptography in computer network | Cryptography in Matrices|Cryptography linear Algebra
Smart Studies Academy
35 views

1:15
Cryptography Projects | Cryptography Thesis | Cryptography Experts | Cryptography Projects Ideas
MatlabSimulation. Com
416 views

4:40
Cryptography|What is cryptography|Cryptography tutorial|Cryptography and network security lecture
Last Night Study
287 views

0:21
Cryptography | Definition of Cryptography | What is Cryptography? | Define Cryptography
Maths With Bushra
16 views

8:37
Cryptography||Symmetric Key cryptography||Asymmetric Key Cryptography||Cryptography Notes
PPC Learning
2.3K views

4:03
cryptography, cryptography introduction, cryptography definition, cryptography example
Ahmad Hassan
7 views

49:40
Low-Complexity Cryptography and Simple Hard-to-Learn Functions
Simons Institute for the Theory of Computing
436 views
![[Chapter 2a] Cryptography II + Hash Functions & Wordlists](/image/i.ytimg.com/vi/-lCGZIPeExI/xhqdefault.jpg.pagespeed.ic.QXc4mtbpKC.jpg)
2:16:21
[Chapter 2a] Cryptography II + Hash Functions & Wordlists
Avocado
5.9K views

10:03
Cryptography Hashing functions SHA and specificaly SHA1 hashing
Alon Lalezari - אלון ללזרי
11 views
57:46
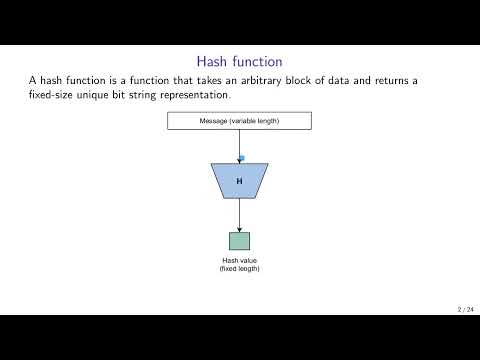
Applied Cryptography: 3. Hash functions and HMAC
Applied Cryptography by University of Tartu
635 views

13:44
V3a: Hash functions: Fundamental concepts (Applied Cryptography 101)
Cryptography 101
1.0K views
14:13
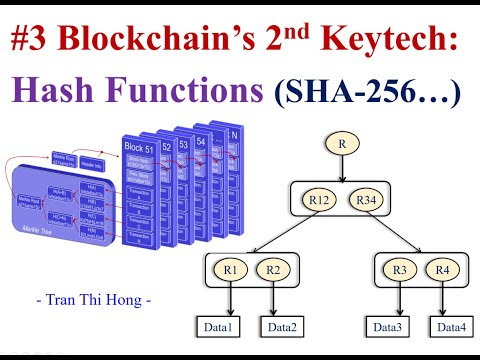
#4 Why do we need cryptography hash functions SHA256 for blockchain network?
FuTech
274 views

6:12
#33 Message Authentication & Authentication Functions in Cryptography |CNS|
Trouble- Free
193.2K views

42:13
Cryptography Mathematics | Lecture 1 | One way functions | RSA Encryption #Hindi
Mathsmerizing
1.6K views
24:32
C++ Builder - Hash functions, Symmetric + Asymmetric Cryptography, and Digital Signature (LockBox)
VCL Examples
3.1K views

12:54
Authentication Functions | Cryptography and Network Security
Ekeeda
910 views
39:09
Cryptography Hash Functions (CSS322, L18, Y14)
Steven Gordon
1.1K views

9:50
Cryptography Explained. Symmetric and Asymmetric Encryption. Hash functions. Digital signatures.
Encyclopedia
136 views
1:36:49
Winter School on Cryptography Symmetric Encryption: Cryptanalysis of Hash Functions - Eli Biham
Bar-Ilan University - אוניברסיטת בר-אילן
632 views

40:57
13-Message Authentication in Cryptography 🔐 | MAC vs Hash Functions vs Encryption
Sundeep Saradhi Kanthety
234.7K views

22:14
V3d: Iterated hash functions (Applied Cryptography 101)
Cryptography 101
639 views
16:59
Hash Functions in Cryptography
Abhishek Sharma
544.2K views

7:20
CRYPTOGRAPHY | HASH Functions
Irsa Khan
137 views
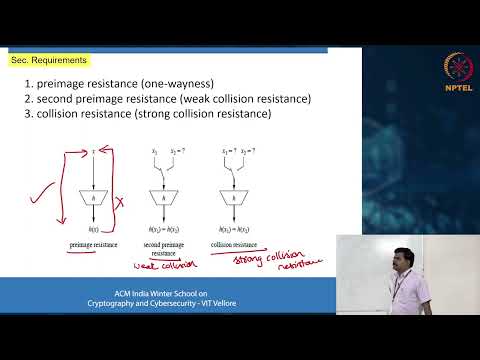
1:19:45
Hash Functions, Digital Signatures and Quantum Cryptography
Aswani Kumar Cherukuri
165 views

1:22:01
21. Cryptography: Hash Functions
MIT OpenCourseWare
190.7K views
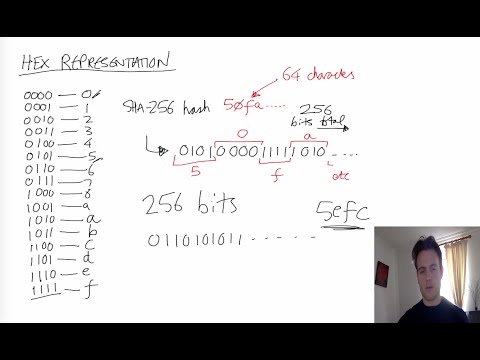
28:25
Cryptography/SSL 101 #2: Cryptographic hash functions
Matt Thomas
15.6K views

4:33
SSMRV Video Lectures-Cryptography and Network security-Hash Functions
SSMRV College
211 views

15:34
Symmetric and Asymmetric Key Cryptography, Hash Functions
Information Security Awareness
192 views

6:06
Cryptography Basics: Securing Blockchain | Hash Functions, Public Keys & Digital Signatures
CodeLucky
6 views

1:04:22
Cryptography Primer Session 3 – Integral Asymmetric Functions
Microsoft Research
192 views

5:48
Introduction to Cryptography: Hash Functions
Wolfram U
200 views
33:19
Introduction to Quantum Cryptography Without One-Way Functions
Simons Institute for the Theory of Computing
427 views
7:36
Mathematical cryptography - Trapdoor functions
Math And Tea
2.2K views

22:07
Basics of Cryptology – Part 13 (Modern Cryptography – Cryptographic Hash Functions)
Cryptography for Everybody
2.9K views

55:26
Tomoyuki Morimae - Quantum cryptography without one-way functions
Quantum Information @ RUB
236 views
Previous Page 2