Search Results for "transposition cipher techniques"
Find videos related to your search query. Browse through our collection of videos matching "transposition cipher techniques". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "transposition cipher techniques"
50 results found

44:36
TanjaCrypt 16 November 2017 part 1: column transposition cipher, Hill cipher and more.
TanjaCrypt
35 views

43:22
TanjaCrypt 16 November 2017 part 2: column transposition cipher, Hill cipher and more.
TanjaCrypt
13 views

5:57
Columnar Transposition Cipher Technique | Encrypt Plain Text Message | Cipher & Decipher
Arihant Online Academy
27.4K views
4:42
Cipher 04- Columnar Transposition Cipher
Asher Dupre
10.0K views

0:56
Gold Refining Techniques Traditional Techniques vs. Modern Techniques
K-jhil Scientific
3 views

1:34
work study techniques - study techniques for students - innovative study techniques
villaelisa5000z
1 views

10:20
Block Cipher and Stream Cipher | Explain with animation | Block cipher vs Stream cipher
Chirag Bhalodia
38.3K views

6:31
Shift Cipher/Caesar Cipher | Monoalphabetic Cipher | Substitution Cipher
Study Table
10.6K views

7:12
An Indecipherable Cipher | Vigenère cipher | Vigenere Cipher | Polyalphabetic Cipher | Cryptography
Muhammed Mustaqim
144 views

10:35
Hill cipher|Hill cipher encryption and decryption|Hill cipher example|Hill cipher in cryptography
Last Night Study
39.7K views

13:51
Affine cipher|Affine cipher encryption and decryption|Affine cipher example|Affine cipher decryption
Last Night Study
113.1K views

6:37
caesar cipher | atbash cipher | keyword cipher| pigpen cipher|cryptography types and applications
Sir Huzaifa Sabir
46 views

6:13
Imran Khan Pr Ciphar Case Batna Hi Nahi | The cipher case of Imran Khan is not being made.. The cipher case is being dragged unnecessarily... The day the cipher was waved?... The cipher case is not a crime... This crime has been added. ... Aitzaz Ahsan
Update Pakistan News
6 views

11:42
Feistel cipher|Feistel block cipher|Feistel cipher structure|Feistel cipher example|cryptography
Last Night Study
18.2K views
3:31
Difference Between Block Cipher and Stream Cipher | Block Cipher VS Stream Cipher |Network security
DK Technical Point 2.0
532 views

2:41
Difference between Block cipher and stream cipher / Block cipher vs stream cipher
ms coder
5.3K views

1:05
Vernam cipher || Cipher || Will cipher || Verum rex || bill cipher || airbnb
CryptobyQB
21 views

5:45
CRYPTOGRAPHY & NETWORK SECURITY(7) Cryptography Techniques substitution techniques, Hill Cipher
Algorithm Pod
72 views

7:47
CRYPTOGRAPHY & NETWORK SECURITY(6) Cryptography Techniques substitution techniques, Playfair Cipher
Algorithm Pod
67 views

6:50
CRYPTOGRAPHY & NETWORK SECURITY(4) Cryptography Techniques substitution techniques, Ceaser Cipher
Algorithm Pod
88 views

6:27
Substitution vs transposition ciphers | classical encryption techniques | Cryptography | Urdu/Hindi
Fawad Speaks
129 views
4:05
Classical encryptiin techniques, substitution technique, transposition technique
Gaurav Khatri
498 views

11:29
Substitution and transposition techniques | Monoalphabetic and polyalphabetic substitution ciphers
Abhishek Sharma
570.4K views

9:44
Encryption techniques Substitution and Transposition in telugu #telugu#encryption#substitution#telug
Chinni Educationalclub
5.6K views
12:47
Transposition Techniques & Steganography Network Security & Cryptography Dipti Prasad MCA Sem4 MCR R
M.C.A Department Marwari College, Ranchi
43 views

4:20
Encryption Techniques (substitution and transposition) Cryptography and Network security in HINDI.
Helping Tutorials
9.9K views

11:29
Substitution and transposition techniques Monoalphabetic and polyalphabetic substitution ciphers
The viral zone
3 views

3:53
Transposition techniques in Cryptography and cyber security tamil||CCS||Anna university reg-2021.
Murugan Tech World
2.0K views

8:37
#14 Rail Fence & Columnar Transposition With Example-Encryption Techniques|Information Security|
Trouble- Free
44.6K views
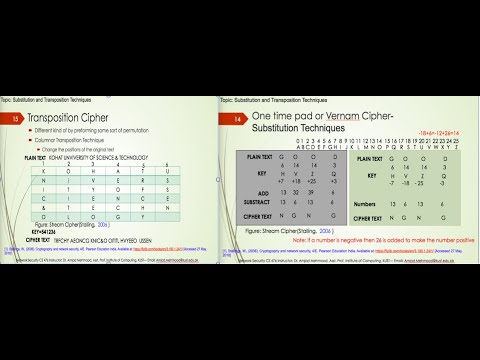
23:33
FACULTY047 CS476 KUST2020 L8 V1 Substitution and Transposition Techniques
Dr. Amjad Mehmood
41 views
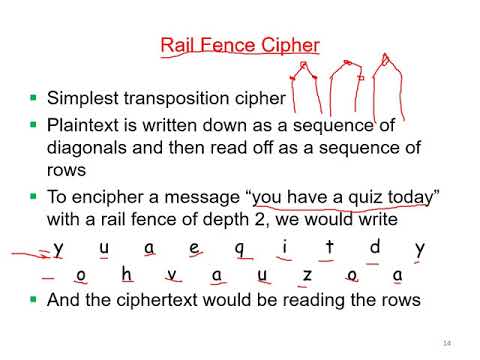
12:13
10 - Cryptography for E-Security - Transposition Techniques
Lectures
174 views

3:50
classical encryption techniques|| substitution|| Transposition
IT Academy
20 views

5:20
Transposition Techniques || Rail Fence technique in cryptography and network security
Lab Mug
11.6K views
1:27:36
IPsec Day1 Authentication, Encryption, Confidentiality | Substitution Transposition Techniques
Law Sah
142 views

46:54
Encryption Techniques || Substitution and Transposition ||Caesar, Atbash, Polybius, Pigpen, Playfair
Kifayat Ullah
408 views
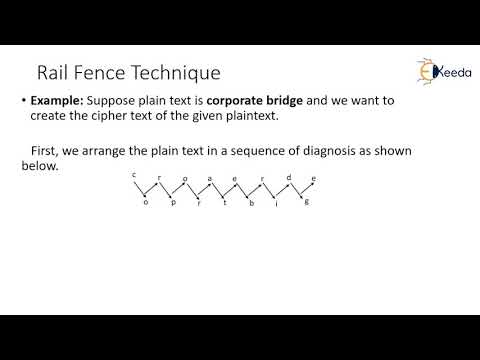
9:44
Transposition Techniques | Cryptography and Network Security
Ekeeda
304 views

12:54
Key and Keyless transposition techniques | Cryptography and Network Security
Ekeeda
282 views

6:53
Transposition Techniques | Prof. Priyanka Sorte | PHCASC
MES e-Learning
142 views

5:44
CRYPTOGRAPHY & NETWORK SECURITY(8) Cryptography Techniques Transposition Technique
Algorithm Pod
66 views

3:58
Cryptography - Transposition Techniques
IT DEPATRMENT PSGCAS
5 views

21:50
Transposition Techniques /CS 409 Cryptography and Network Security - Part 5
Renisha's CS Eduworld
249 views

15:05
CNS- Cryptography and Network Security-BE IT- Transposition Techniques
CSE-IT-AI-DS Department GHRIBM, Jalgaon JALGAON
38 views

5:15
Transposition Techniques
WorthWatching
201 views

11:25
Transposition techniques & Stenography | Computer and Network Security | 3350704 | Darshana T. Patel
VPMP POLYTECHNIC
62 views

16:06
Substitution Techniques | Caesar Cipher | Monoalphabetic Cipher | Part 1 | Information Security
eVeda
79 views

5:04
One Time Pad | Vernam Cipher| Substitution Cipher Techniques| Introduction in Hindi | CSS
Gyanpur
86 views

24:37
IT P04 M-02. Symmetric cipher model, substitution techniques - Ceasar cipher
e-content:Engineering & Technology
72 views

7:59
Monoalphabetic cipher and Polyalphabetic cipher |substitution techniques in Hindi by geeta Chaudhary
Short Tricks Learning
781 views

25:07
Substitution Techniques: Caesar Cipher &Monoalphabetic Cipher-Cryptography & Network Security#21is71
VTU padhai
3.7K views

15:32
Cryptography | Classical Cipher | Substitution Cipher Techniques
MathPod
8.9K views