Search Results for "techniques in cryptography"
Find videos related to your search query. Browse through our collection of videos matching "techniques in cryptography". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "techniques in cryptography"
50 results found

21:42
Remote User Authentication: Principles & Techniques | Cryptography- #21is71 #cryptography #vtupadhai
VTU padhai
4.0K views

16:57
Cryptography, Cryptographic Security Controls & Cryptography Security Techniques Explained
Luv Johar Free IT Training Videos
1.8K views

5:44
CRYPTOGRAPHY & NETWORK SECURITY(8) Cryptography Techniques Transposition Technique
Algorithm Pod
66 views

3:40
What is Cryptography? | Explain Cryptography | How Cryptography Works? | Cryptography Information
Crypto & Blockchain News (CBN)
4 views
![[Cryptography] What is Cryptography? | Introduction To Cryptography | Cryptography Tutorial in Hindi](/image/i.ytimg.com/vi/8are73H9oUQ/xhqdefault.jpg.pagespeed.ic.GWwooXAHkM.jpg)
19:28
[Cryptography] What is Cryptography? | Introduction To Cryptography | Cryptography Tutorial in Hindi
Cyber Odisha
97 views

8:20
Cryptography|Cryptography in computer network | Cryptography in Matrices|Cryptography linear Algebra
Smart Studies Academy
35 views

1:15
Cryptography Projects | Cryptography Thesis | Cryptography Experts | Cryptography Projects Ideas
MatlabSimulation. Com
416 views

4:40
Cryptography|What is cryptography|Cryptography tutorial|Cryptography and network security lecture
Last Night Study
287 views

4:35
Cryptography Explained - What is Cryptography | History Of Cryptography | Types of Cryptography
Encryption Consulting LLC
404 views

0:21
Cryptography | Definition of Cryptography | What is Cryptography? | Define Cryptography
Maths With Bushra
16 views

8:37
Cryptography||Symmetric Key cryptography||Asymmetric Key Cryptography||Cryptography Notes
PPC Learning
2.3K views

4:03
cryptography, cryptography introduction, cryptography definition, cryptography example
Ahmad Hassan
7 views

2:34
Cryptography - Substitution Cipher Explained: From Basics to Advanced Techniques
securityconceptsnotes
404 views

17:19
L-6 || PlayFair Substitution Techniques with Example || Network Security and Cryptography
Simply Studies With Chealsha
32 views

6:44
Substitution Techniques in Cryptography
SmartTech Classroom
11 views

3:20
classical cryptography techniques
Pavithra
5 views

0:57
Cryptography and encryption techniques🧐😱 #computersecurity #cybersecurity #crypto #tech #shorts
CYBER HEAL
431 views

15:05
CNS- Cryptography and Network Security-BE IT- Transposition Techniques
CSE-IT-AI-DS Department GHRIBM, Jalgaon JALGAON
38 views

18:24
Types of Security Techniques | Cryptography | Steganography
chandu's smart class
72 views

21:18
Cryptography & Network Security||Basic Cipher Techniques|| DSE-2@DU
AV Maths School
11 views
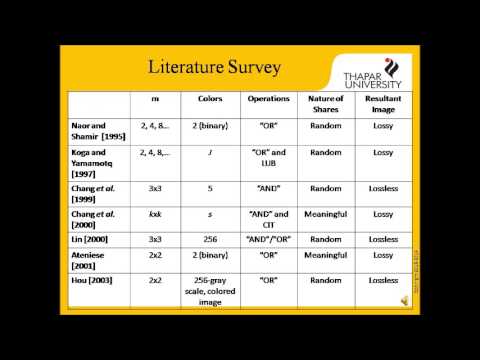
24:53
Extended Visual Cryptography Techniques for True RGB Images
Kirti Dhiman
1.3K views

8:22
Learning Symmetric Cryptography: Substitution Techniques
Lead GATE - ME,XE,PI
23 views

29:30
Substitution Techniques in Cryptography Explained | Caesar,Mono &Poly Alphabetic,Playfair Made Easy!
Prof Antony Vijay
155 views

21:50
Transposition Techniques /CS 409 Cryptography and Network Security - Part 5
Renisha's CS Eduworld
249 views

0:11
Cryptography techniques || Substitutional technique || Transpositional technique || UNIT 01
Online Learning
5.0K views

6:27
Substitution vs transposition ciphers | classical encryption techniques | Cryptography | Urdu/Hindi
Fawad Speaks
129 views

7:33
Cryptography lecture/tutorial: Substitution techniques for transforming plain text to cipher text
Sanjay Pathak
3.7K views
9:37
cryptography and network security: Introduction, security goals, attacks,services and techniques
Pravisha candideyes
145 views

7:28
#Substitution Techniques Caesar Cipher in Cryptography & Network Security L-10 #encryptionTechniques
Concept Clear
275 views

23:41
TY BSc-IT - NS Unit 1 - Lec 4 - CRYPTOGRAPHY TECHNIQUES, Substitution, Transposition, Ceasar Cipher
Tirup Parmar
887 views
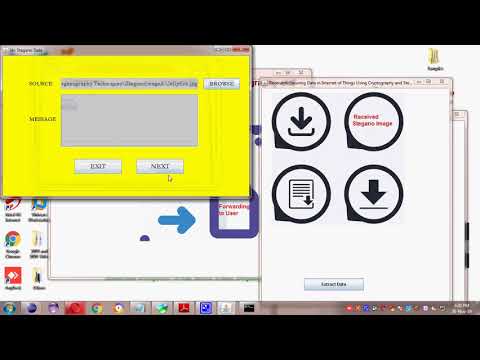
6:26
Securing Data in Internet of Things Using Cryptography and Steganography Techniques
Manjunath IEEE Projects
2.2K views

13:35
Cryptography & Network Security - Substitution Techniques Part I
ATHIRA B.KAIMAL
174 views
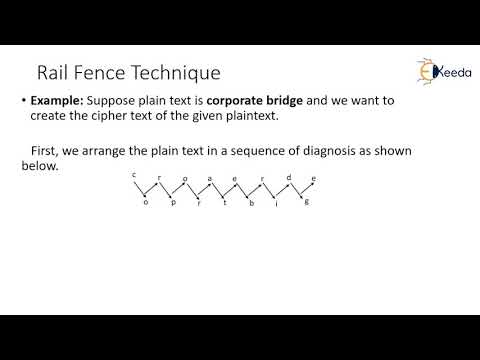
9:44
Transposition Techniques | Cryptography and Network Security
Ekeeda
304 views

25:07
Substitution Techniques: Caesar Cipher &Monoalphabetic Cipher-Cryptography & Network Security#21is71
VTU padhai
3.7K views
54:43
Classical Encryption Techniques in Tamil | Cryptography and Cyber Security in Tamil | Unit 1 CB3491
4G Silver Academy தமிழ்
61.8K views

35:25
EXIT Exam Preparation Questions on Cryptography - Cipher Techniques | Cyber security.
CS Mastery with Azeze
96 views

15:32
Cryptography | Classical Cipher | Substitution Cipher Techniques
MathPod
8.9K views
19:25
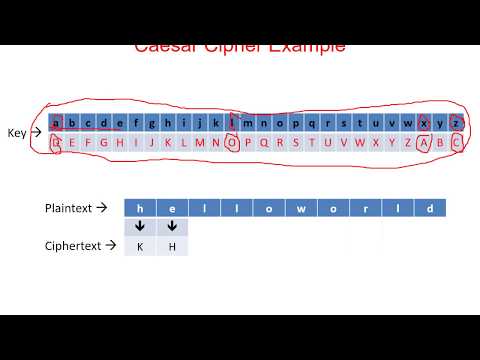
09 - Cryptography for E-Security - Substitution Techniques
Lectures
193 views

55:09
25 ANCIENT Encryption Techniques That Were SHOCKINGLY Complex | History of Cryptography
Echoes of the Unknown
136 views
3:01
Securing Data in Internet of Things (IoT) Using Cryptography and Steganography Techniques | C#.net
JP INFOTECH PROJECTS
1.9K views
11:02
Symmetric Key Cryptography: Cryptographic Techniques
Computer Science Lessons
4.4K views

10:12
Hybrid cipher|Hybrid Transportation Cipher|Transposition techniques in cryptography|Network Security
Last Night Study
1.2K views

15:52
Substitution Cipher Techniques |1st Ceaser Cipher | Cryptography and System Security
learn with inspiration
96 views

6:20
Substitution Techniques|| Cryptography and Network Security|| Lecture Series|| A.Catherine
Catherine SNS
1 views

11:21
Classical encryption techniques | Cryptography and System Security (Reshoot)
Ekeeda
290 views

3:31
The Cryptographic Protocol - what are the techniques of cryptography?
BitCoin XTreme
692 views

8:34
Caesar cipher | substitution techniques in cryptography and network security by Babita Verma
ITCS classes
614 views

5:05
Substitution Cipher Techniques | Cryptography and System Security | Introduction in Hindi
Gyanpur
711 views

1:28
Substitution Techniques in Cryptography in Hindi / Urdu - Network Security 9 - Substitution Cipher
RaxsCorp
1.7K views

10:31
Caesar cipher in cryptography substitution techniques
CodeMind
2 views
Previous Page 2