Search Results for "strengthening techniques"
Find videos related to your search query. Browse through our collection of videos matching "strengthening techniques". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "strengthening techniques"
50 results found

13:00
Woodworking Decorative Inlay Techniques - Finishing and Advanced Techniques
Tutorials Arena
120 views

0:57
SOME BEST TECHNIQUES|Techniques
Rizwan Malik
2 views

1:02
Law of Attraction in Hindi Law of Attraction Techniques LOA Techniques
Adhyatmik Vikas Mission
0 views

0:10
Tree Grafting Techniques #tree #grafting #techniques
MakeMagic
13 views

6:23
Scissor Techniques: Learn scissor cutting techniques ...
Grant Sharp
11 views

3:35
Persuasion Techniques: 9 Effective Persuasive Techniques
The China Gadgets
2 views

4:49
CRYPTOGRAPHY & NETWORK SECURITY(5) Cryptography Techniques substitution techniques
Algorithm Pod
57 views
6:50
CRYPTOGRAPHY & NETWORK SECURITY(4) Cryptography Techniques substitution techniques, Ceaser Cipher
Algorithm Pod
88 views

2:34
Cryptography - Substitution Cipher Explained: From Basics to Advanced Techniques
securityconceptsnotes
404 views

17:19
L-6 || PlayFair Substitution Techniques with Example || Network Security and Cryptography
Simply Studies With Chealsha
32 views
14:33
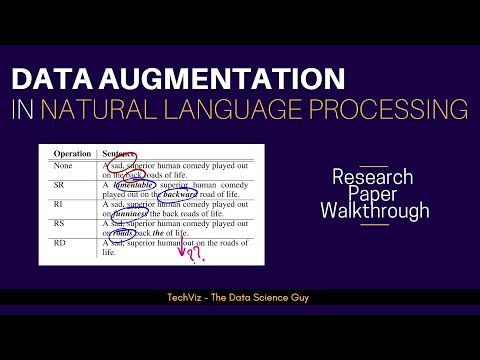
Data Augmentation Techniques for Text Classification in NLP (Research Paper Walkthrough)
TechViz - The Data Science Guy
3.5K views

22:50
Classical Encryption Techniques - 1
Varsha's EduWorld
719 views

6:44
Substitution Techniques in Cryptography
SmartTech Classroom
11 views

7:54
Débuter les soustractions (avec le signe -) : sens et techniques CP - Cycle 2 - Maths
Maître Lucas
128.1K views

17:51
How To Read A Book - Speed Reading Techniques - Mathematics of Reading
Book Buddy
113.0K views

9:06
Basic of Steganography Techniques Part 1
Selflearning
39 views
![[[OSINT]] Photo Metadata, Geolocation & Stenography Techniques](/image/i.ytimg.com/vi/-rgoYn-beMI/xhqdefault.jpg.pagespeed.ic.fzk3TbOXU2.jpg)
8:35
[[OSINT]] Photo Metadata, Geolocation & Stenography Techniques
Ian
189 views

0:42
Unlocking Secrets Steganography Techniques Explained!
Cyber Guardians
668 views

16:25
Collision Resolution Techniques in Hashing - Separate Chaining Hash Table - Coding With Clicks
Coding With Clicks
667 views

3:20
classical cryptography techniques
Pavithra
5 views

0:57
Cryptography and encryption techniques🧐😱 #computersecurity #cybersecurity #crypto #tech #shorts
CYBER HEAL
431 views

15:05
CNS- Cryptography and Network Security-BE IT- Transposition Techniques
CSE-IT-AI-DS Department GHRIBM, Jalgaon JALGAON
38 views

18:24
Types of Security Techniques | Cryptography | Steganography
chandu's smart class
72 views
0:10
Speak like a ceo using these 3 techniques
Yasir Khan Shorts
117.7K views
15:43
Data Exfiltration Techniques | TCP Socket | TryHackMe Data Exfiltration
Motasem Hamdan
4.6K views

6:19
Interview Techniques - STAR Method
Jason Jordan
1.1M views
4:17
Using Design Techniques for Clear and Appealing Data Visualization
nullQueries
81.2K views

30:58
A Review on Clouds Security Based Encryption and Decryption Techniques
IJERT
27 views

0:34
Drama Techniques: Narration
PBSDramaDepartment
45.4K views

5:15
Transposition Techniques
WorthWatching
201 views

1:02
Techniques for Secure Data Aggregation #ai #artificialintelligence #machinelearning #aiagent
NextGen AI Explorer
6 views

3:46
European Parliament Privacy Platform: Encryption Techniques and Surveillance (summary clip)
James Heather
151 views
1:39
HTML Injection Trick to Download any Video from Website + Many Other Techniques in Comments
Ziv
258.4K views

21:18
Cryptography & Network Security||Basic Cipher Techniques|| DSE-2@DU
AV Maths School
11 views

0:44
Unlocking Data Privacy with Functional Encryption Techniques #ethdenver #gensyn #encryption #web3
ETHDenver
568 views
24:53
Extended Visual Cryptography Techniques for True RGB Images
Kirti Dhiman
1.3K views

16:35
NIS-3.4 Cryptography Techniques (Symmetric key cryptography) Part-1
rathod_sir
141 views

16:06
Substitution Techniques | Caesar Cipher | Monoalphabetic Cipher | Part 1 | Information Security
eVeda
79 views

0:35
World War 2 Codebreaking Techniques Enigma Machines & Beyond Unlocking the Mysteries of WWII Codebre
The Red Edge Of War
1.2K views

8:22
Learning Symmetric Cryptography: Substitution Techniques
Lead GATE - ME,XE,PI
23 views

0:20
Adaptive Active Power Sharing Techniques for DC and AC Voltage Control in a Hybrid DC AC-2019-20
MATLAB ASSIGNMENTS AND PROJECTS
18 views

28:41
Attacking RSA with lattice reduction techniques (LLL)
David Wong
20.5K views

0:44
Revolutionizing Digital Privacy with Advanced Cryptographic Techniques
Tech-Pulse-7
27 views
![[CompNetSec] - 03 - Classical Encryption Techniques](/image/i.ytimg.com/vi/3kNbuz9aIHs/hqdefault.jpg)
1:20:02
[CompNetSec] - 03 - Classical Encryption Techniques
Hicham Elmongui
14.6K views

12:06
TRANSPOSITION TECHNIQUES || RAIL FENCE TECHNIQUE || COLUMNAR TRANSPOSITION -- NETWORK SECURITY
t v nagaraju Technical
11.8K views

13:45
Secure Binary Image Steganography Using F5 algorithm Based on Data Hiding and Diffusion techniques
Jitendra Singh
954 views

1:18:47
2. Classical Encryption Techniques
Pritesh Prajapati
2.5K views

29:30
Substitution Techniques in Cryptography Explained | Caesar,Mono &Poly Alphabetic,Playfair Made Easy!
Prof Antony Vijay
155 views

21:50
Transposition Techniques /CS 409 Cryptography and Network Security - Part 5
Renisha's CS Eduworld
249 views

0:11
Cryptography techniques || Substitutional technique || Transpositional technique || UNIT 01
Online Learning
5.0K views