Search Results for "sp:ti:away=LEC"
Find videos related to your search query. Browse through our collection of videos matching "sp:ti:away=LEC". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "sp:ti:away=LEC"
50 results found
36:02
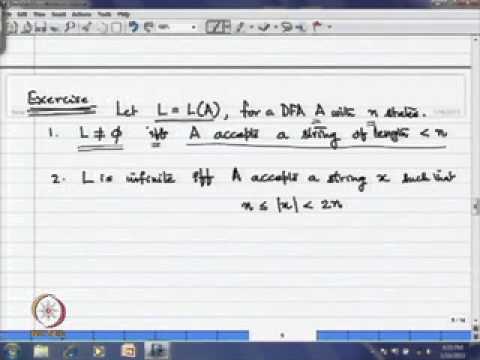
Mod-13 Lec-01 Decidability
nptelhrd
1.8K views
9:43
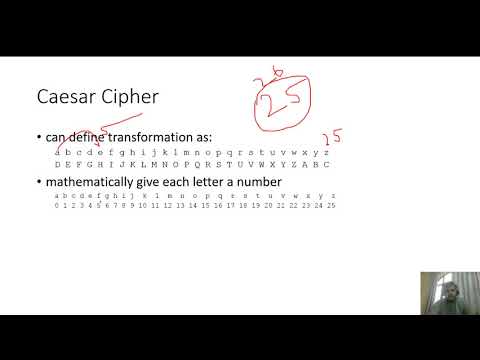
Caesar Cipher Explained with Solved Example|lec 3|urdu|hindi
ITphile
379 views

1:01:04
Mod-01 Lec-02 Introduction to finite automaton.
nptelhrd
93.0K views

50:50
Lec 5: Parametric equations for lines and curves | MIT 18.02 Multivariable Calculus, Fall 2007
MIT OpenCourseWare
315.7K views
54:31
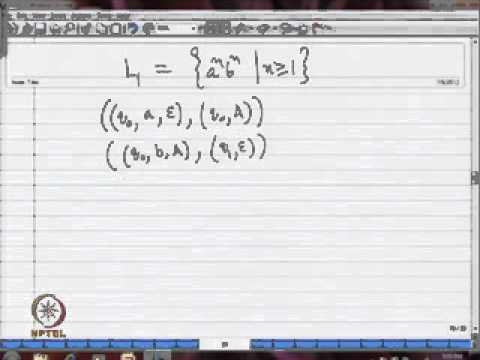
Mod-10 Lec-01 Pushdown Automata
nptelhrd
1.7K views

50:03
Cryptography & Network Security | Unit-3 | Lec-2 | One Shot | KCS-074 | Aktu Exams| PYQ Solutions
Multi Atoms
11.8K views

16:58
Deterministic Finite Automata|LEC-7|Formal Languages andAutomata Theory, VTU syllabus module - 1
Vijaya Prasad Lectures
2.6K views

11:08
Lec-5: What is Grammar in TOC | Must Watch
Gate Smashers
1.3M views

12:42
Lec-29: Cyclic Redundancy Check(CRC) for Error Detection and Correction | Computer Networks
Gate Smashers
1.9M views

6:43
Turing machine ( TM) | Introduction | Part-1/2 | TOC | Lec-85 | Bhanu Priya
Education 4u
290.9K views

7:43
Convert Regular Expression to Finite Automata | Examples | TOC | Lec-43 | Bhanu Priya
Education 4u
202.2K views

12:20
Lec-21: Propositional Logic in Artificial Intelligence | Knowledge Representation | All Imp Points
Gate Smashers
1.1M views
6:14
Lec-81: Symmetric Key Cryptography in Network Security with examples
Gate Smashers
663.8K views

55:49
Mod-01 Lec-20 Introduction to context free languages (cfls)
nptelhrd
40.0K views
1:16:15
Functions & Its Types | Lec 3 | Discrete Maths | GATE Computer Science
Unacademy Computer Science
2.3K views

15:52
what is cryptography lec 2
#tech
1 views

4:37
Lec-57: What is LBA(Linear Bounded Automata) | All Points Covered | Theory of Automata
Gate Smashers
368.7K views

7:26
NFA Example | Part-1/3 | TOC | Lec-14 | Bhanu Priya
Education 4u
234.8K views

4:03
Lec-46: CFL and CFG Introduction and Syllabus discussion
Gate Smashers
410.0K views

12:43
Lec-03:Asymmetric Key Or Public Key | CRYPTOGRAPHY AND NETWORK SECURITY
webSak
45 views
26:05
Lec 20 Perfectly-Secure Message Transmission
NPTEL - Indian Institute of Science, Bengaluru
528 views

50:09
Lec 11: Differentials; chain rule | MIT 18.02 Multivariable Calculus, Fall 2007
MIT OpenCourseWare
226.4K views

13:13
Converting CFG to CNF | Example | TOC | Lec-71 | Bhanu Priya
Education 4u
780.6K views

10:58
Lec-50: What is Pushdown Automata in TOC | Definition & Explanation in Hindi
Gate Smashers
1.3M views

10:30
Introduction to cryptography and network security lec-1
John dance master
17 views

56:02
Mod-01 Lec-31 Introduction to pushdown automata (pda).
nptelhrd
31.7K views
7:55
Lec-06 Basics of Steganography || Types of Steganography Explained in Hindi
spyknown
1.4K views

4:26
Finite Automata | FA | TOC | Lec-06 | Bhanu Priya
Education 4u
454.3K views

45:43
Mod-03 Lec-20 PUSHDOWN AUTOMATA
nptelhrd
88.0K views

8:01
CCS | Unit-2 | Lec-10 | DES Subkey Generation Algorithm
s kalaivani
257 views
57:36
Mod-11 Lec-01 Turing Machines Definitions and Examples
nptelhrd
2.7K views

2:06
#50 Arden's theorem in Automata Theory and computability I TOC I ATC I lec 50
Preeti Education center
69 views

13:20
Lec 14 | How to Convert NFA to DFA Part 2
Techeducation 4u
157 views
5:19
Theory of Automata | Regular Expression | TOC | Lec-40 | Bhanu Priya
Education 4u
217.0K views
52:51
Lec 2: Determinants; cross product | MIT 18.02 Multivariable Calculus, Fall 2007
MIT OpenCourseWare
566.0K views

7:01
Algorithm Vs #Program & Algorithm Vs Pseudocode | Lec 6 | Design & Analysis of Algorithm
CSE Guru
2.9K views
10:33
Lec-15: Binary Search in Data Structure by #Naina Mam
Gate Smashers
435.1K views

49:27
Mod-01 Lec-03 GRAMMARS AND LANGUAGES GENERATED (Contd)
nptelhrd
61.6K views

8:15
Finite Automata | Finite State Machine | Formal Languages Automata Theory | Lec-3 | #finiteautomata
s2learningedu
164 views

17:36
Lec-26: Minimization of DFA in Hindi with example | TOC
Gate Smashers
1.6M views
32:35
Lec 50 Discrete Cosine Transform-4
NPTEL - Indian Institute of Science, Bengaluru
675 views

21:18
Lec 4 | Cryptography from 1800 to World War2 | Edgar Allan |Vernam | cipher machine | Modern Crypto
Qasim Ali
223 views

51:52
Mod-01 Lec-01 What is theory of computation?
nptelhrd
297.5K views

5:18
Lec-3: What is Automata in TOC | Theory of Computation
Gate Smashers
1.3M views

0:53
Rekkles: I go to war with Oscarinin. I believe in him. #fnatic #leagueoflegends #rekkles #lec
FNATIC
677.0K views

16:47
Space Complexity | DAA | Design & Analysis of Algorithms | Lec-02 | Bhanu Priya
Education 4u
402.0K views

23:41
TY BSc-IT - NS Unit 1 - Lec 4 - CRYPTOGRAPHY TECHNIQUES, Substitution, Transposition, Ceasar Cipher
Tirup Parmar
887 views

11:18
Lec-59: Turing Machine for a^nb^nc^n | Design Turing Machine
Gate Smashers
723.8K views

55:11
Mod-01 Lec-06 REMOVAL OF UNIT PRODUCTIONS , CHOMSKY NORMAL FORM FOR CFG
nptelhrd
48.7K views

58:25
Mod-04 Lec-23 PUSHDOWN AUTOMATA PDA TO CFG
nptelhrd
60.3K views