Search Results for "sha vs md5"
Find videos related to your search query. Browse through our collection of videos matching "sha vs md5". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "sha vs md5"
50 results found

7:31
VERIFY MD5 / SHA256 Hash or Checksum on Windows 11
SavvyNik
28.3K views

28:17
Parte 1 - Introdução ao Algoritmo SHA 256 - Secure Hash Algorithm SHA256
Laboratório de Inutilidade Pública
7.2K views

37:17
How we created the first SHA-1 collision and what it means for hash security - Defcon 25
Elie Bursztein
9.2K views
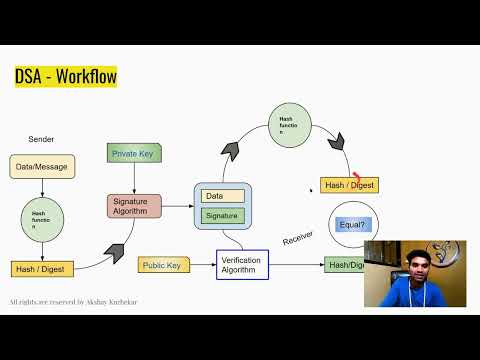
25:20
Asymmetric Key Cryptography & Hashing Explained | RSA, DSA, SHA-256 in Blockchain Part 03 Hindi 2025
Akshay Kurhekar
116 views

0:35
Cracking The Code - Exploring Secure Hash Algorithms - SHA Short #cybersecurity #hashing
Technically U
1.1K views
6:09
cryptography and network security sha 3 keccak and ripemd 160
CodeMade
14 views

6:17
Bitcoin & SHA-256 Explained With Animations
I Explain Crypto
1.1K views

10:03
Cryptography Hashing functions SHA and specificaly SHA1 hashing
Alon Lalezari - אלון ללזרי
11 views

28:38
#ክሪፕቶግራፊ How Blockchain Uses SHA-256 for Cryptographic Hashing | Simplified in Amharic
Self Programmers
268 views

17:40
AES RSA PGP GPG SHA - Qu'est-ce que c'est ?
Paf LeGeek
34.0K views

1:00
Exploring Cryptography: SHA-256 to Blake3 Transition
Stephen Blum
264 views

4:20
SHA function in Cryptography and cyber security tamil||CCS||Anna university reg-2021.
Murugan Tech World
5.5K views
0:37
How SHA 3 processes cryptographic data with just 2
Cyber Freedom 2025
742 views

6:39
Hash-Funktionen: SHA &Co. // deutsch
the native web GmbH
8.0K views
0:14
Sha'Carri Richardson American Athlete #shorts
Strong Mind Set
143.7M views

32:34
SHA-256 (COMPLETE CONCEPT & DETAILED STEP-BY-STEP EXPLANATION)
Xiuminseokie21
21.7K views

0:57
SHA-256: The Ultimate Weapon Against Hackers – Here’s Why! #sha256 #cybersecurity #programming
Code
2.2K views

2:14
Bitcoin Security Explained: The Role of SHA-256 #sha256 #bitcoin #cryptocurrency
Cryptocurrency Guide
39 views
4:57
Explication de SHA-256 🔑 Blockchain : enjeux et mécanismes cryptographiques
MOOC de l'IMT
5.3K views

0:25
CyberSecurity Definitions | Secure Hash Algorithm (SHA)
Relative Security
3.2K views

2:44
What Is The SHA Family? - SecurityFirstCorp.com
SecurityFirstCorp
16 views

10:54
Secure Hash Algorithm (SHA) in Cryptography and Network Security #cryptography #networking #security
Lab Mug
11.2K views

0:46
Unlocking SHA-256: The Hunt for the Special Number
Tech Chips
10.8K views

10:21
SHA: Secure Hashing Algorithm - Computerphile
Computerphile
1.3M views

3:24
Kala Sha Kala - Full | OM | Aditya Roy K, Elnaaz , Sanjana S | Enbee,Amjad Nadeem,Raahi,Dev N,Kumaar
Zee Music Company
80.0M views
22:59
How Does SHA-256 Work?
learnmeabitcoin
362.6K views

11:03
Learn the ART of CRYPTOGRAPHY - SHA-1 HMAC Hashing Explained (Urdu/Hindi)
Cybersecurity Academy - CertificationHUB
184 views

0:42
🔐 What is SHA-256? | How This Powerful 🔢 Hash Function Keeps Your Data Secure! 🛡️#sha256 #crypto
BitnByte Mining
8.1K views

0:57
What is SHA-256 ?
Ai Hilarious
21.2K views

1:18:35
Lecture 21: SHA-1 Hash Function by Christof Paar
Introduction to Cryptography by Christof Paar
58.4K views

1:38:17
Lecture 22: SHA-3 Hash Function by Christof Paar
Introduction to Cryptography by Christof Paar
69.6K views

1:54
What is a Bitcoin hash and SHA-256
99Bitcoins
25.0K views

49:53
Cryptography for Beginners - Full Python Course (SHA-256, AES, RSA, Passwords)
freeCodeCamp.org
1.9K views
17:51
SHA 1 | Cryptography and Network Security
Ekeeda
2.7K views

0:15
Sha'Carri Richardson on fire in Nairobi 🔥 #athletics #usa #shacarririchardson #sprint #running
World Athletics
17.7M views

2:00
MAC vs SHA | CRYPTOGRAPHY
NotesNaka
130 views

0:08
Crypto Fact #338 SHA-256
April Token
77 views

0:59
The Protector of Bitcoin--Intro to the SHA-256 Algorithm
BullsEye Investing
460 views

13:01
SHA-256 | COMPLETE Step-By-Step Explanation (W/ Example)
RedBlockBlue
182.9K views

19:24
How does SHA-256 work? (full explanation)
Boot dev
38.7K views

0:57
USA vs Jamaica - Sha'Carri Richardson vs. Shericka Jackson - 4x100 M race #4x100m #athlete #race
Sports FIR
264.6K views

17:43
Does The NSA Control Bitcoin (SHA-256)?
Bitcoin University
64.6K views

0:54
Elon Musk’s XChat SHA 256 BITCOINSTYLE ENCRYPTION ELLIPTIC CURVE CRYPTOGRAPHY
Ai Daily News
222 views
5:40
SHA-256 Explained Simply: How Hashing Works! 🔐💡
CSwithBen
1.9K views

0:31
Sha'Carri making it look EASY 🏃♀️
NBC Sports
207.0M views

10:50
Secure Image Storage Application with Owner Alerts using AES and SHA-256 | SUBJECT: CSA33303
Adam Mirza
98 views

10:52
SHA-1 (Secure Hash Algorithm - 1) Part-1 Working Explained in Hindi
5 Minutes Engineering
269.3K views

55:46
Secure Hash Algorithm (SHA): A Comprehensive Analysis-Foundations, Evolution, Applications, and P...
Hello InfoSec
16 views

13:18
Introduction to Cryptographic Hash Function| Merkel Damgard Scheme | SHA-256 | Secure Hash Algorithm
Muhammed Mustaqim
607 views

8:51
SHA-1 Algorithm ( Cryptography & Network Security)
ponjesly cse
49.1K views