Search Results for "security through obscurity"
Find videos related to your search query. Browse through our collection of videos matching "security through obscurity". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "security through obscurity"
50 results found

44:58
Webinar: Advancing image security and compliance through Container Image Encryption!
CNCF [Cloud Native Computing Foundation]
1.2K views

58:50
CSS Webinar Series 2024 : Information Security Through Steganography
Cyber Security & Systems
11 views

58:36
Security Conferences Through a Covid Lens: Past, Present, and Future
Bace Cybersecurity Institute
16 views

2:20:34
Building Energy Security Through Innovation
The Manila Times
814 views

36:55
Brainstorm Tech 2024: How To Build Trust Through Security
Fortune
5 views

4:17
Transforming Social Security through Social Reforms_SSPF_Azerbaijan
Mirsadig Sadikhzade
303 views

0:42
5 Easy Ways to Protect Your Online Privacy and Security #onlineprivacy #techorbit #security
Tech Orbit
202 views

13:02
Cryptography and Network Security | Unit 1 - Security Services
Harshitha's StudyVerse
48 views

31:22
23-IP Security (IPSec) Part 1 🔐 | Authentication Header Explained | Network Security
Sundeep Saradhi Kanthety
204.7K views
![VTU COMPUTER NETWORKS AND SECURITY (18CS52) [Security Methods, Cryptography] (M4 L2)](/image/i.ytimg.com/vi/-TKiDUSDoqk/xhqdefault.jpg.pagespeed.ic.4MvFQi-c68.jpg)
28:04
VTU COMPUTER NETWORKS AND SECURITY (18CS52) [Security Methods, Cryptography] (M4 L2)
Canara Engineering College Mangalore
7.0K views
3:59
Security Attacks |Cryptography |Network Security
Last Night Study
431 views

34:32
Steganography For Cyber Security Day 01 || Sonargaon University Cyber Security Batch 01
BinaryGuardians
112 views

21:38
What are Threats | Threat categories | Security Attacks| Types of Attacks | Network Security
T N V S PRAVEEN
249 views

1:27
Steganography in Cyber Security | Steganography in Cyber Security Projects
NetworkSimulationTools
75 views

5:57
Trojan horse in cyber security | trojan in cyber security | Lecture 30
Simply Made
55.9K views

2:36
CRYPTOGRAPHY AND NETWORK SECURITY 1ST TOPIC INTRODUCTION AND NEED OF SECURITY
keep it simple
34 views

0:59
How to Become a Cyber Security Analyst in 2024? | Cyber Security | Intellipaat #Shorts
Intellipaat
130.3K views

1:28
C# : System.Security.Cryptography vs. Windows.Security.Cryptography
Hey Delphi
117 views

1:00
Cryptography And Network Security Course by The Security Buddy #shorts #thesecuritybuddy
The Security Buddy
815 views

0:33
Data Security Revolution: AI and Blockchain Enhance Security in Forensic Engineering! Part 7 #ai
TEKTHRILL
20 views

6:48
AURA Security Review 2025 - the BEST Online Security package or just hype? 🤔
VPNpro
9.4K views
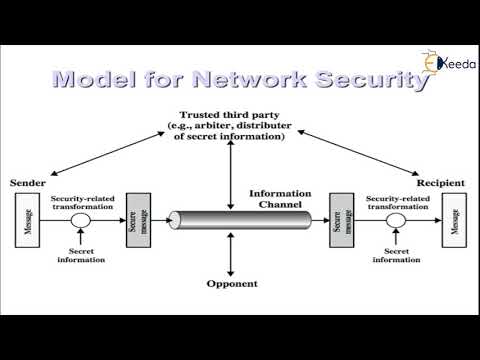
7:33
Network Security Basics | Cryptography and System Security
Ekeeda
84 views

43:15
cryptography and network security || cryptography and network security bangla tutorial.
Online_learning_tube
229 views

18:06
Security Attack | Cryptography and System Security
learn with inspiration
54 views

7:34
Security in Digital Image Processing:Importance of Digital Image Security: Module V,Lecture 5,EC703A
Dr. SANGITA ROY
28 views

10:41
1.1 OSI Security Architecture Model | Cryptography & Cyber Security CB3491 | Anna University R2021
PK Educational Institute
4.9K views

5:19
What Is Cryptology & Cyber Security? What Is The Main Concept Of Cryptology & Cyber Security?🎭📂🖥️
Technical Supradip
302 views

38:05
Network Security Tutorial | Introduction to Network Security
CRAW SECURITY
1.1K views

17:54
LEC04| Cryptography & Network Security |OSI Security Architecture& Steganography by Ms. M . Saranya
MLID - MLR Institute of Technology
70 views

9:15
1.0: Security Goals and attacks- Cryptography and System Security
Ishita Lalan
12 views

11:18
Quantum Cryptography | Network Security in tamil,#sscomputerstudies,#quantum,#cryptography,#security
SS Computer Studies
1.7K views

1:09:37
CompTIA Security+ Full Course for Beginners - Module 1 - Fundamental Security Concepts
BurningIceTech
31.3K views

11:14:05
Cyber Security Full Course FREE | Cyber Security Course 2026 | Intellipaat
Intellipaat
10.3K views

4:27
||What is Stenography In Cyber Security?||Types Of Steganography||Cyber Security|| By-@cyberwire09
CYBERJET
206 views

0:46
Parliament security breach major security setback for us.
The Daily Brief
2.5K views
9:37
cryptography and network security: Introduction, security goals, attacks,services and techniques
Pravisha candideyes
145 views

1:11
Top 10 Cyber Security Tools You Must Use in 2025 | Best Cyber Security Tools | Intellipaat #Shorts
Intellipaat
9.9K views

0:44
Cryptography and information security: encryption algorithms and methods for ensuring data security.
Superpupt
75 views

12:14
How I Would Learn Cloud Security as a Complete Beginner | FULL Cloud Security Analyst Roadmap 2025
With Sandra
19.0K views

1:08
Security on distributed systems Cloud security versus traditional IT
IFox Projects
49 views

12:03
VIGENERE CIPHER LESSON 7 |Polyalphabetic cipher|Cryptography& network security| Information security
Shashi KS
94 views

11:25
Coursera : Usable Security Week 1 HCI Basics Quiz Answers | University of Maryland Cyber Security
Codeshala
2.6K views

42:46
RSA Algorithm in Cryptography and Network Security - UGC NET PYQs | NETWORK SECURITY - RSA ALGORITHM
Unify Study
4.6K views

15:50
🔐Cryptography - PART 2 - ENCRYPTION - Symmetric & Asymmetric | Data Security | HINDI | PhD Security
PhD Security
66 views

12:52
USENIX Security '23 - Security Analysis of MongoDB Queryable Encryption
USENIX
298 views

6:58
Vigenere cipher in easy | huzu's tution | Information Security | cyber security #education #cipher
Cyber Geek
148 views

12:35
Security Goals | Cryptography and System Security
learn with inspiration
136 views

0:16
A Day in the Life of Cyber Security | SOC Analyst | Penetration Tester | Cyber Security Training
Mike Miller - Break in Cyber
1.6M views

7:50
Security Attacks in Tamil | Cryptography and Cyber Security in Tamil | Unit 1 | CB3491
4G Silver Academy தமிழ்
23.8K views

3:04
Application-Aware Security Devices - CompTIA Security+ SY0-401: 1.1
Professor Messer
152.2K views