Search Results for "security attacks on cryptographic hash function"
Find videos related to your search query. Browse through our collection of videos matching "security attacks on cryptographic hash function". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "security attacks on cryptographic hash function"
51 results found

6:38
security attacks || urdu hindi | passive attacks in urdu | active attacks in urdu | types | part 6
IT Expert Rai Jazib
201 views

35:45
Networks Security | Attacks | Active Attacks | Passive Attacks | Cryptography | Steganography | IA
Bhavishya Coaching SGNR
771 views
![CSS #3 - [PART-1] Security Attacks | Passive attacks | Active attacks | Be The Best | BTB](/image/i.ytimg.com/vi/_HLKp9wvbkM/xhqdefault.jpg.pagespeed.ic.hZE19l_P6j.jpg)
5:16
CSS #3 - [PART-1] Security Attacks | Passive attacks | Active attacks | Be The Best | BTB
Be The Best
416 views

31:03
Password Attacks and their Countermeasures | Password Attacks | Cyber Security Attacks
CyberPlatter
2.0K views

14:25
#3 Types Of Security Attacks- Active & Passive Attacks and their Types |Information Security|
Trouble- Free
105.8K views

0:14
security attacks ||types of attacks in information security||
Notice Point
6.7K views

5:55
Attacks : Types of attacks in Network Security | Cryptography | Security Goals in Cryptography
Quick Trixx
23.3K views

18:03
02-Types of Attacks in Network Security | Active vs Passive Attacks | Cryptography &Network Security
Sundeep Saradhi Kanthety
406.7K views

15:25
Types Of Security Attacks #Active & #Passive Attacks and their Types | Cryptography Network Security
Concept Clear
355 views

21:38
What are Threats | Threat categories | Security Attacks| Types of Attacks | Network Security
T N V S PRAVEEN
249 views

4:01
Cryptographic Attacks Explained | Common Attacks & How They Work
Cyberconnect
454 views

10:26
Cryptography & Network Security | Meaning | Types | Encryption| Decryption | Hash Function (Hindi)
lets understand stop cramming
84 views

9:01
Message Authentication Code (MAC) in Cryptography Hash Function || Network Security in Telugu
Lab Mug
14.3K views

9:00
HMAC and CMAC in Cryptography Hash Function || Network Security in Telugu
Lab Mug
10.9K views
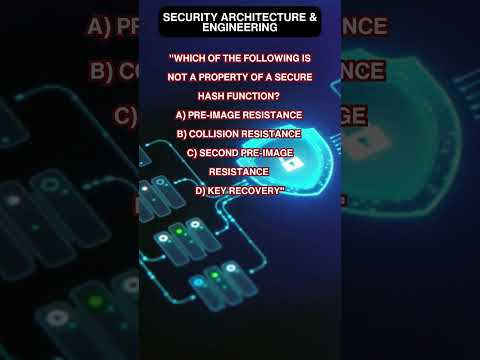
0:11
Hash Function Security: Core Properties
KD Sec n Tech
7 views

35:45
Hash Function in Cryptography(Malayalam)/CS 409 Cryptography and Network Security
Renisha's CS Eduworld
2.8K views

6:08
What is Security requirement of hash function in cryptography
Chirag Bhalodia
25.1K views

10:53
PART 4 | HASH FUNCTION ATHENTICATION TECHNIQUE IN CRYPTOGRAPHY & NETWORK SECURITY (BANGLA)
COMPUTER SCIENCE WITH BHASKAR SIR
229 views

7:40
MAC Based on Hash Function | HMAC in network security
Chirag Bhalodia
67.7K views

5:07
cryptanalytic attacks| urdu hindi | cryptanalytic attacks lecture| cryptanalytic attacks tutorial|19
IT Expert Rai Jazib
4.0K views

13:51
Most Amazing Snake Attacks - King Cobra attacks Python - Python attacks Cobra
Our Animals
1 views

16:00
Top 10 Leopard Attacks - Most Amazing Animal Attacks - Crazy Leopard Attacks
Diverte Mania
35 views

3:47
7.2 Security Requirements for Cryptographic Hash Functions
EngiNerd
152 views

15:26
Security Protocols: Lecture 2e (Cryptographic Hash Functions & Communication Integrity)
Antonis M
322 views

7:04
Cryptographic Hash Functions - CompTIA Security+ SY0-401: 6.2
Professor Messer
46.0K views
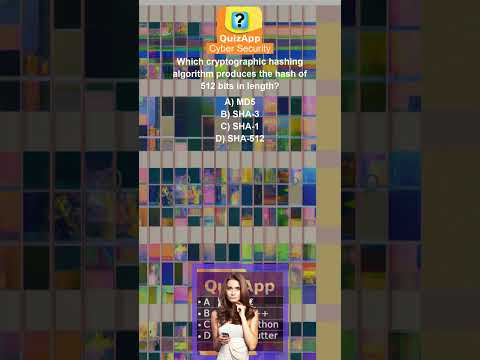
0:13
Cyber Security Which cryptographic hashing algorithm produces the hash of 512 bits in length
QuizApp learn programming quiz C C++ Python Java
89 views

3:17
Cryptographic Security: Understanding Hash Functions and Their Implications for Investment in 2025
Crypto Luminary
4 views

6:57
Cryptographic Hash Functions - CompTIA Security+ SY0-301: 6.2
Professor Messer
21.2K views

44:53
Networks Security | Security Services | Security Goals | Cryptography | Steganography | Attacks | IA
Bhavishya Coaching SGNR
929 views

1:01:28
Cryptography & Network Security | CH1.2 The OSI Security Architecture & 1.3 Security Attacks
Computer & IT lectures
67 views

14:40
SECURITY ATTACKS || TYPES || ACTIVE || PASSIVE || OSI SECURITY ARCHITECTURE --NETWORK SECURITY
t v nagaraju Technical
35.3K views

9:13
What is Security and security attacks, security services in CNS
Lab Mug
13.4K views

9:31
Cryptographic Attacks - CompTIA Security+ SY0-701 - 2.4
Professor Messer
116.9K views

4:29
CISSP Cyber Security: Cryptographic Attacks (Known/Chosen Ciphertext) #cryptography #cryptosecrets
Cyber Security Cartoons
132 views

5:19
Cryptographic Attacks - SY0-601 CompTIA Security+ : 1.2
Professor Messer
292.5K views

9:54
Cryptographic Attacks - CompTIA Security+ SY0-501 - 1.2
Professor Messer
185.3K views

10:35
Cryptography and Network Security: #6 Cryptographic Attacks
Shreya's E-Learning
4.1K views

15:14
77. CompTIA Security+ SY0-701: 🔐 Top Cryptographic Attacks Explained
CertPro Hub
41 views

22:27
Security + 1.2 Cryptographic Attacks
Cyber-Recon
590 views

3:55
2.4 - Cryptographic Attacks (CompTIA Security+ SY0-701)
CyberMuk
178 views

2:49
Domain 1.8: Cryptographic attacks - CompTIA Security+ SY0 601
Hans IT Academy
4.0K views

1:26
Cryptographic Attacks - CompTIA Security+
HackerHacks
1 views

5:02
1.6-Types of Security Attacks | Active & Passive Attacks |Cryptography | hindi
OVERNIGHT ENGINEERING
29 views

8:14
Network Security - Attacks (Types of attacks - Active and Passive) | Cryptography
Lectures by Shreedarshan K
391 views

9:26
Security Attacks : Types Of Active Attacks Explained in Hindi
5 Minutes Engineering
282.2K views

12:05
What is Network Security? | Types of Network Attacks | How these Attacks are done
Tech Guru Manjit
14.6K views

9:32
Top 10 Cyber Attacks In History | Biggest Cyber Attacks Of All Time | Cyber Security | Simplilearn
Simplilearn
359.4K views

14:51
DoS / DDoS ATTACKS IN CYBER SECURITY || Denial of Service || Distributed Denial of Service Attacks
Sundeep Saradhi Kanthety
35.7K views

19:15
Hash Functions in hashing, Hashing in data structures, Types of hash functions, division method
CSIT Tutorials by KanyaKumari
4.5K views
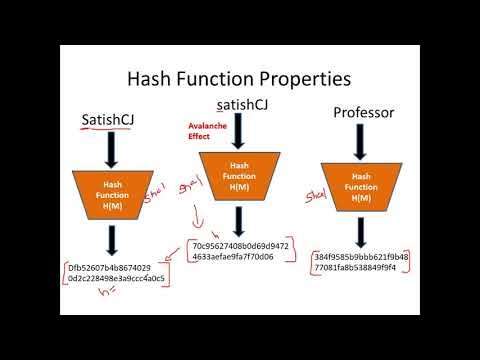
44:53
Introduction to Hash Functions and Application of Hash Functions in Cryptography - CSE4003
Satish C J
24.6K views

1:07
Lok Sabha Security Breach on Parliament Attack Anniversary: Om Birla Assures Everyone's Security
Oneindia
1.3K views