Search Results for "secure your data"
Find videos related to your search query. Browse through our collection of videos matching "secure your data". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "secure your data"
50 results found
5:09
Understanding Asymmetric Key Algorithms: How They Keep Your Data Secure
securityconceptsnotes
80 views

19:34
Secure your sensitive data with VeraCrypt
OPSEC IT
1 views

0:26
🔒Encryption & Decryption Explained: Secure Your Data!🌐#short #tendting# #cybersecurity
Sarkar Study Waves Education
2.8K views

0:39
Confused between Data Mesh & Data Fabric? Watch to learn which aligns better with your data strategy
Knowi
2.6K views

7:01
Proton Authenticator Tutorial How to Secure Your 2FA Codes & Never Get Locked Out of Your Account
Proton
35 views

7:41
An RSA-Based Secure Image Steganography Technique Using Adaptive Data Hiding - Mid
Akash Joy
7 views

12:01
Secure Data Transfer Based on Visual Cryptography - Part1
AmAn
30 views

1:02
Techniques for Secure Data Aggregation #ai #artificialintelligence #machinelearning #aiagent
NextGen AI Explorer
6 views

7:49
Hybrid Algorithm for secure data over Cloud OS
Avin Pasupuleti
1.4K views
1:04
Java Secure Coding: Data Confidentiality and Integrity 12 2 Asymmetric Crypto
AppSec Labs
823 views

13:45
Secure Binary Image Steganography Using F5 algorithm Based on Data Hiding and Diffusion techniques
Jitendra Singh
954 views
5:31
Secure Cloud Data Using Hybrid Cryptography Using Python
Myra Projects
60 views

0:09
🔒 SSL (Secure Sockets Layer) 🌐 | Data Encryption, Cybersecurity & Safe Web Browsing
Smart Digital Pakistan
138 views
7:35
Intelligent cryptography approach secure distributedbig data | Final Year Projects 2016 - 2017
ClickMyProject
130 views
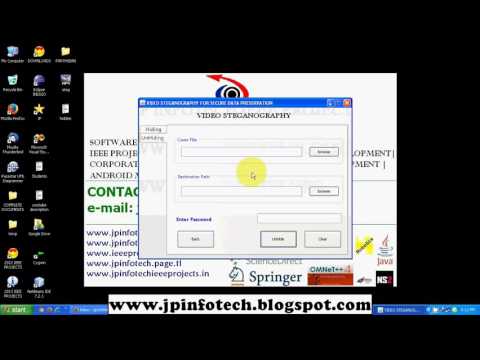
2:52
Video Steganography for Secure Data Preservation
Final Year Projects
797 views

3:01
How Will Quantum Cryptography Secure Consumer Data? - America First Democrats
America First Democrats
0 views
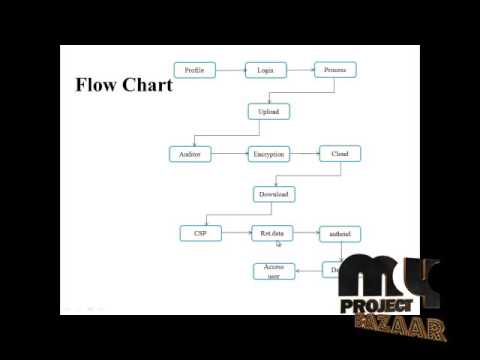
7:36
Intelligent cryptography approach for secure distributed big data | Final Year Projects 2016 - 2017
MyProjectBazaar
140 views
13:13
Secure data transfer based on visual cryptography
AmAn
122 views
4:23
Secure Data Transfer Over Internet Using Image Steganography
Nevon Projects
15.6K views
13:28
Secure Data Transfer Based on Visual Cryptography- Working Demo
AmAn
121 views
3:24
Secure Data Transfer Video Steganography Projects | Student Projects
Python Projects
475 views

4:01
Speech Steganography | Data Hiding in Speech | Secure Speech File using Arduino or Raspberry-Pi
Techpacs
193 views

8:55
Final Year Projects | Secure Data Hiding Algorithm using Encrypted Screte Message
ClickMyProject
2.3K views

2:11
Secure Medical Imaging Data using Cryptography | Classification |Brain Tumor Dataset | MATLAB | FYP
Saqqiya Technology Point
170 views
10:40
SecRBAC: Secure data in the Clouds ||best ieee 2017 java projects list.
SD Pro Solutions Pvt Ltd
194 views
11:10
An RSA-Based Secure Image Steganography Technique Using Adaptive Data Hiding - Final
Akash Joy
22 views

3:45
How Secure Is Big Data Development? - Next LVL Programming
NextLVLProgramming
0 views
5:28
Secure Data Aggregation Technique for Wireless Sensor Networks in the Presence of Collusion Attacks
MyProjectBazaar
18 views

2:46
What Is Symmetric-key Encryption And How Does It Secure Data? - Emerging Tech Insider
Emerging Tech Insider
1 views

2:47
Locking Down Data: Cryptographic Protocols for Secure Communication Explained
Operational Excellence Mastery
6 views
19:58
DNA Cryptography An New Approach to Secure Cloud Data in Java
OKOKPROJECTS
161 views
1:14
Secure Data Transfer Using Image Steganography through Socket Programming using Java
GOPINATHNAIDU CHENNAMSETTI
70 views

7:13
A SECURE DATA DYNAMICS AND PUBLIC AUDITING SCHEME FOR CLOUD STORAGE | CLOUD COMPUTING
Takeoff Edu Group
523 views

0:51
Elliptic Curve Cryptography-Based Scheme for Secure Signaling and Data Exchanges in P... | RTCL.TV
Social RTCL TV
106 views

0:45
The Secret to Secure Data: Encryption by Ak. Coder
Ak. Coder
37 views
1:00
Post Quantum Cryptography Secure Data in the Quantum Age
Relax Reels shorts
13 views

2:54
Unlocking Secure Data Mining: Cryptographic Algorithms Explained
Operational Excellence Mastery
8 views

14:19
Asymmetric Algorithms & Hashing Explained Simply | CRISC Domain 4 | Secure Data & Digital Signatures
ISACA PREP ACADEMY
66 views
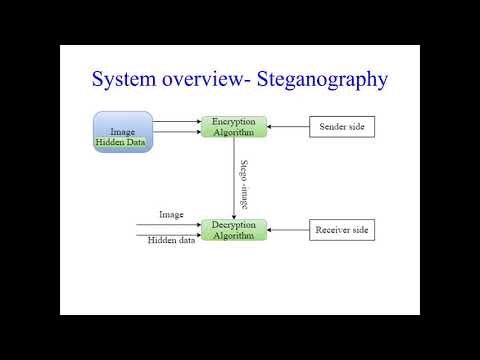
13:14
235_Study of secure data transmission based wavelets using steganography and cryptography techniques
CMRCET CSE
11 views

3:25
Secure Data Transfer using Crytography and Image Steganography
TRU PROJECTS
218 views

0:58
🔐 RSA Encryption Explained: Secure Data Transmission! 🌐💡 | Cryptography & Crypto Wallets 🔑#crypto
BitnByte Mining
145 views

3:02
Secure Data Communication And Cryptography Based On DNA based Message Encoding
Naren Projects
36 views

24:09
SECURE DATA TRANSFER USING CRYPTOGRAPHY AND HYBRID STEGANOGRAPHY
Ashna Choudhary
146 views

3:30
How Does Quantum Cryptography Secure Modern Data? - CountyOffice.org
County Office Law
8 views

1:01:01
Cutting Edge Advances In Data Science - Secure Multiparty Computation - Brett Hemenway Falk
The Encrypted Economy
81 views

3:10
Is Telehealth Data Encryption Really Secure? - Gen Z Telehealth Guide
Gen Z Telehealth Guide
0 views

0:15
Large Prime Numbers & AI in Cryptography | Secure Data 2024
Digi Twins AI News
23 views
1:30:44
Tutorial 5a: Advances in Cryptography and Secure Hardware for Data Outsourcing
IEEE ICDE
230 views
1:30
Secure Data Transfer Using Image Steganography | 4K
Don Escriba
301 views

1:18
MONA SECURE MULTI-OWNER DATA SHARING FOR DYNAMIC GROUPS IN THE CLOUD
Gagner Technologies
211 views
Previous Page 2