Search Results for "re-powering Protocol"
Find videos related to your search query. Browse through our collection of videos matching "re-powering Protocol". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "re-powering Protocol"
50 results found
11:59
41.Quantum key distribution II: EPR protocol
Jochen Rau
892 views

6:59
19.4 Cryptographic protocol
World Gurukul way of Learning Values and Wisdom
3.6K views

10:02
S/MIME protocol in Hindi | Cryptography and Network Security
Abhishek Sharma
142.4K views

3:24
Skeng X Sparta - Protocol (Official Music Video)
Skeng
104.2M views

1:02:51
DEF CON 8 - Bennett Haselton - A protocol that uses steganography to circumvent
DEFCONConference
202 views

6:32
URGENT - Tounkara réagit au discours en anglais de Diomaye Faye et tire sévèrement sur le protocol
Senegalactu Tv
88.7K views

14:08
Low Exponent Attack | Attacks on RSA | Protocol Failure Attack | Cryptography & Network Security
Quick Trixx
11.4K views

3:03
Is The BB84 Protocol Essential For Quantum Cryptography? - Quantum Tech Explained
Quantum Tech Explained
14 views
7:19
What is MQTT Protocol ? How it works ? | 2022
IT and Automation Academy
178.4K views

5:43
How To Hide A Message In An Image (Steganography) Using Linux Terminal | The Protocol S
The Protocol S
140 views

6:43
Kerberos Authentication Protocol 🔥🔥
Perfect Computer Engineer
198.5K views

1:07:03
Steve Girvin: Secure Communication in a Quantum World – BB84 Protocol
Yale University
4.3K views

1:01
Symmetric Cryptography - AES Encryption - Exa Protocol #shorts
Exa Protocol
96 views

9:24
Kerberoes protocol in Cryptography and Network Security #cryptography #education #computerscience
Lab Mug
1.8K views
16:34
Graciela Bachu: The BB84 Quantum Cryptography Protocol (TSI)
Talaria
221 views

5:04
SSL/TLS handshake Protocol
Sunny Classroom
496.8K views

13:38
8 - Cryptography Basics - SSL TLS Protocol Explained
CBTVid
15.7K views

13:39
9-3 BB84 Protocol
Q-Leap Edu Quantum Communications
9.6K views

9:23
MIME protocol in Cryptography and Network Security | Email security in Network Security
Abhishek Sharma
119.7K views
1:07:12
DY*: A Modular Symbolic Verification Framework for Executable Cryptographic Protocol Code
F* PopUp Seminar
189 views

4:03
Cryptographic protocol
WikiAudio
520 views

12:17
Video of Protocol Presentation by Daniel Klingenberg on Quantum Cryptography
Daniel Klingenberg
25 views

2:53
What Is The BB84 Protocol In Quantum Cryptography? - Quantum Tech Explained
Quantum Tech Explained
9 views

0:59
Analyze a Crypto Protocol: Governance Model
Leapfrog Crypto
394 views
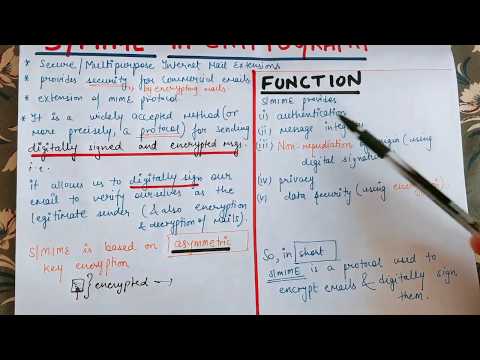
8:22
S/MIME protocol in English | Cryptography and Network Security
Educator Abhishek
45.4K views

12:16
Common Modulus Attack | Attacks on RSA | Protocol Failure Attack | Cryptography & Network Security
Quick Trixx
14.1K views
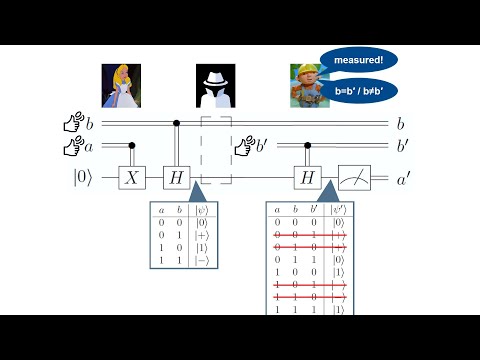
21:53
28.Quantum key distribution I: BB84 protocol
Jochen Rau
16.9K views

4:26
Trivial Flag Transfer Protocol Pico CTF
Mustapha Ait Ichou
264 views

58:50
A distillation–teleportation protocol for fault-tolerant QRAM
Simons Institute for the Theory of Computing
117 views

4:14
Rawal pindi babla Heavy Protocol
Babla Champ
1 views
2:37
Bakhtawar Zardari Protocol
Faisal
705 views

0:05
Read Cryptographic Protocol: Security Analysis Based on Trusted Freshness Ebook Free
Aschock
1 views

0:06
Download Cryptographic Protocol: Security Analysis Based on Trusted Freshness Ebook Free
Kstocker
7 views

0:34
The Leatherman's Protocol Handbook: A Handbook on "Old Guard" Rituals, Traditions and Protocols
Joey D Coffman
16 views

9:38
Bitcoin's Lost Funds Recovery System in Action: NAR Protocol & Upcoming Whitepaper Analysis
Gavin Mehl
923 views

8:12
What is FF & What is HART Protocol
Instrument study
2 views

2:01
Exit Protocol | Official Trailer - Dolph Lundgren
80PoundMedia
29 views
9:19
Cryptography | The Mathematics of RSA and the Diffie-Hellman Protocol
Zach Star
115.5K views
0:51
Poppy Protocol: How To Wear Your Poppy This Remembrance Day #shorts
Narcity
14.4K views

22:15
Verifpal: Cryptographic Protocol Analysis for the Real World
CRSInd
438 views

41:17
CS M S022 Non-Cryptographic Protocol Vulnerabilities
Studio IIT Bombay
429 views
2:32
Drift Protocol #shorts (2) #trading #nosacapital #cryptocurrencyanalysis #driftprotocol
Nosa Capital
184 views

0:42
Part-2 AI coin that can go 10x by 2025, Anyone protocol #cryptoniamhindi #crypto #bitcoin #trading
Cryptoniam Hindi
343 views

49:42
Quantum cryptography | BB84 Protocol, Security & Future Trends | Exploring Future of QM Cryptography
Research Tech info
103 views

43:44
'RSA Multi-party Computation Protocol Overview' by Muthu Venkitasubramaniam. VDF Day '19
MIT Digital Currency Initiative
400 views
6:31
HCG Diet Protocol Explained
Colin Watson
41 views

6:08
Kerberos - authentication protocol
Sunny Classroom
506.1K views

13:22
Needham and Schroeder Protocol
WorthWatching
32.3K views

13:18
Authentication protocol | Cryptography and Network Security
Ekeeda
2.0K views

30:27
LoneStarRuby 2015 - Building a binary protocol client in Ruby: A magical journey!
Confreaks
893 views
Previous Page 2